Severity
High
Analysis Summary
Cybersecurity researchers have detailed a new malware called MDifyLoader, observed in attacks exploiting vulnerabilities in Ivanti Connect Secure (ICS) appliances between December 2024 and July 2025. Threat actors exploited CVE-2025-0282, a critical unauthenticated remote code execution flaw patched in January 2025, and CVE-2025-22457, a stack-based buffer overflow fixed in April 2025, to deploy MDifyLoader for further compromise.
Earlier reports linked CVE-2025-0282 to malware like SPAWNCHIMERA and DslogdRAT, but the latest analysis reveals attackers using DLL side-loading techniques to run MDifyLoader, which loads an encoded Cobalt Strike beacon (version 4.5) in memory. MDifyLoader is built using the open-source libPeConv project, allowing it to decode and execute encrypted payloads stealthily without writing them to disk.
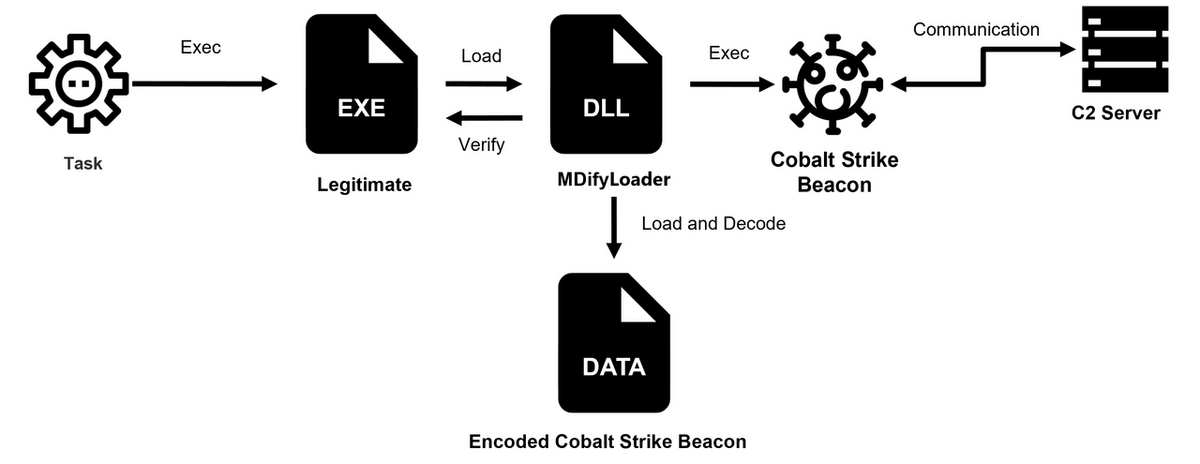
The campaign also used VShell, a Go-based remote access tool, and Fscan, an open-source Go-based network scanning utility. Both tools have been widely adopted by Chinese threat groups. Fscan was deployed via a loader that used DLL side-loading based on FilelessRemotePE, while VShell’s language-checking function, intended to block execution on Chinese systems, inadvertently blocked attacker deployments, forcing multiple installation attempts.
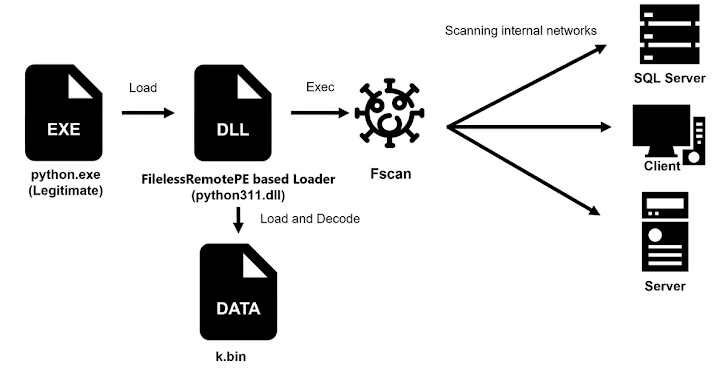
Once initial access was gained, attackers conducted brute-force attacks against FTP, MS-SQL, and SSH servers to harvest credentials. They also leveraged EternalBlue (MS17-010) to move laterally within compromised networks. Persistence was established by creating new domain accounts, adding them to existing groups to blend with legitimate activity and retain access even if other credentials were revoked. Additionally, malware was registered as services or scheduled tasks to ensure execution upon system startup or specific event triggers.
This activity demonstrates sophisticated tradecraft combining zero-day exploitation, stealthy fileless malware deployment, and effective lateral movement. The use of open-source tools like libPeConv and FilelessRemotePE reflects the continued trend of threat actors leveraging legitimate public projects to evade detection and maintain operational flexibility.
Impact
- Remote Code Execution
- Malware Deployment
- Lateral Movement
- Credential Theft
Indicators of Compromise
Domain Name
proxy.objectlook.com
api.openedr.eu.org
community.openedr.eu.org
query.datasophos.com
IP
- 172.237.6.207
MD5
- 6371a1324746a7bc39f10209d6912314
SHA-256
- 699290a753f35ae3f05a7ea1984d95f6e6f21971a146714fca5708896e5e6218
SHA1
- 8f8c2bda128eb626d02766fde9a5b8d7a47306b3
Remediation
- Apply Ivanti security patches for CVE-2025-0282 and CVE-2025-22457 to prevent exploitation
- Monitor for DLL side-loading behavior to detect stealthy malware loaders
- Deploy EDR solutions to identify in-memory execution of Cobalt Strike beacons
- Restrict use of open-source tools like libPeConv and FilelessRemotePE in production environments
- Block known malicious indicators related to MDifyLoader and associated payloads
- Monitor and control installation of Go-based tools like VShell and Fscan
- Enforce strong passwords and account lockout policies to mitigate brute-force attacks
- Disable SMBv1 and apply MS17-010 patch to block EternalBlue exploitation
- Conduct regular credential hygiene reviews to detect unauthorized account creation
- Monitor domain group memberships for unexpected additions
- Audit scheduled tasks and services for suspicious entries indicating malware persistence
- Implement network segmentation to limit lateral movement opportunities
- Conduct proactive threat hunting for indicators of fileless malware and Cobalt Strike beacons

