Severity
High
Analysis Summary
The Crimson Collective extortion group claims responsibility for breaching the private GitHub repositories of Red Hat, a leading U.S.-based open-source software provider. The hackers allege they stole nearly 570GB of compressed data across 28,000 internal repositories, including source code, internal project files, authentication tokens, database URIs, and about 800 Customer Engagement Reports (CERs). These consulting documents often contain sensitive information such as customer infrastructure details, configurations, and credentials, which could be weaponized to compromise client networks.
Red Hat has not officially confirmed a data breach but acknowledged a security incident involving its consulting business. The company stated it has taken remediation steps and emphasized that its core services and software supply chain remain unaffected.
Crimson Collective said the intrusion occurred two weeks ago and that attempts to contact Red Hat with an extortion demand were met only with an automated vulnerability reporting response, followed by ticket escalation to legal and security staff. To bolster their claims, the group posted screenshots, a full directory of stolen repositories, and a list of CERs dated from 2020–2025 on their Telegram channel.
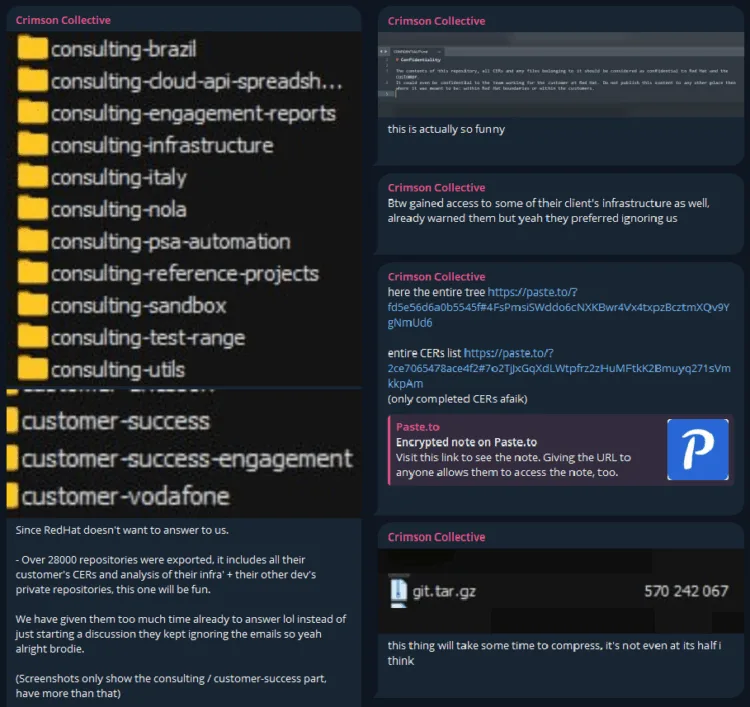
The leaked data allegedly implicates numerous high-profile organizations across finance, healthcare, defense, telecommunications, and technology. Named clients include Bank of America, JPMorgan Chase, AT&T, T-Mobile, Cisco, IBM, Intel, Oracle, Boeing, Airbus, Lockheed Martin, NASA, Mayo Clinic, Kaiser Permanente, Walmart, Starbucks, Unilever, Verizon, Vodafone, Toyota, Volkswagen, Wells Fargo, and the U.S. House of Representatives, among many others.
If legitimate, the breach poses serious risks, including potential downstream attacks on customer environments. In addition to this Red Hat incident, Crimson Collective also claimed responsibility for briefly defacing Nintendo’s topic page to advertise their Telegram channel. Red Hat has not provided further details beyond its initial statement, and the extent of the data compromise remains under investigation.
Impact
- Data Exfiltration
- Credential Theft
- Lateral Movement
- Unauthorized Access
- Reputational Damage
- Operational Disruption
Remediation
- Immediately rotate exposed credentials and tokens, invalidate and replace all potentially leaked secrets to prevent unauthorized access.
- Conduct a full forensic investigation, preserve logs and artifacts to determine scope, timeline, and affected systems.
- Audit and remove sensitive data from repositories, delete hardcoded secrets and commit history that contain credentials or URIs.
- Enforce repository access controls and least privilege, review team permissions and remove unused or excessive access.
- Enable and require multi-factor authentication (MFA) for all developer and administrative accounts, reduce risk from credential theft.
- Revoke and reissue compromised certificates and API keys, update integrations that used those keys or URIs.
- Implement secret scanning and prevention in CI/CD, block commits containing credentials and automatically rotate detected secrets.
- Harden CI/CD pipelines and limit token scopes, ensure build agents and runners cannot leak or expose secrets.
- Apply strict branch protection and code review policies, require peer review and signed commits for sensitive repositories.
- Increase logging, monitoring, and alerting on repository access and unusual Git operations, detect anomalous exfiltration patterns.
- Notify affected customers and partners promptly, provide guidance on indicators of compromise and required remediation steps.
- Offer or require password and token rotation for impacted clients, assist with containment and validation of downstream access.
- Engage external incident response and legal counsel, coordinate disclosure, regulatory reporting, and potential remediation support.
- Conduct a security posture review and third-party audit, validate supply-chain integrity and developer practices.
- Deploy network segmentation and compensating controls for critical systems, reduce blast radius from credential misuse.
- Train developers on secure coding and secret management, mandate use of vaults for secrets and remove insecure practices.

