Severity
High
Analysis Summary
Researchers are alerting people about malicious email campaigns that use the Rockstar 2FA phishing-as-a-service (PhaaS) toolset to obtain Microsoft 365 account credentials. Even users with a multi-factor authentication (MFA) set may still be at risk because this campaign uses an adversary-in-the-middle (AitM) attack that enables attackers to intercept user credentials and session cookies.
It is believed that Rockstar 2FA is a modernized DadSec (also known as Phoenix) phishing kit. Under the name Storm-1575, Microsoft is monitoring the creators and resellers of the Dadsec PhaaS platform. Similar to its forerunners, the phishing kit is promoted through platforms such as ICQ, Telegram, and Mail.ru, charging $200 for a two-week membership (or $350 for a month). This allows cybercriminals with minimal technical knowledge to launch extensive campaigns.
Two-factor authentication (2FA) bypass, 2FA cookie harvesting, antibot protection, login page themes that imitate well-known services, fully undetectable (FUD) links, and Telegram bot integration are some of the capabilities that Rockstar 2FA advertises. Additionally, it has a contemporary, easy-to-use admin panel that lets users create URLs and attachments, monitor the progress of their phishing operations, and even customize the themes applied to the generated links.
Various initial access vectors, including URLs, QR codes, and document attachments, are used in email campaigns detected by researchers. These vectors are included in messages sent from compromised accounts or spamming programs. The emails employ a variety of bait formats, from demands for e-signatures to advisories about file sharing. The kit includes antibot checks using Cloudflare Turnstile to discourage automated analysis of the AitM phishing pages, in addition to employing legitimate link redirectors (such as shortened URLs, open redirects, URL protection services, or URL rewriting services) as a way to get around antispam detection.
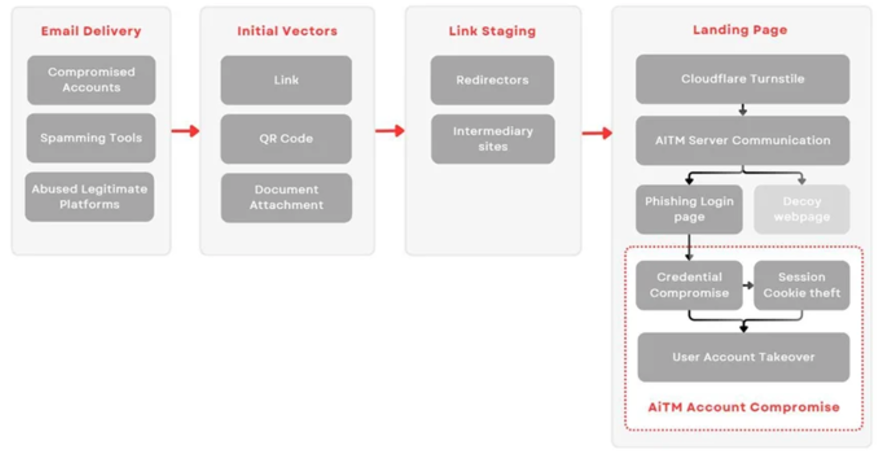
Threat actors are exploiting the trust that comes with platforms like these, according to the experts, who noted that they saw the platform using legitimate services like Atlassian Confluence, Google Docs Viewer, LiveAgent, Microsoft OneDrive, OneNote, and Dynamics 365 Customer Voice to host the phishing links. Despite several obfuscations put into the HTML code, the design of the phishing page closely matches the sign-in page of the brand being copied. The AiTM server receives all user data entered on the phishing page instantly. The target account's session cookie is then obtained using the credentials that were stolen.
Impact
- Credential Theft
- Security Bypass
- Identity Theft
Indicators of Compromise
Domain Name
- entertainmentcircuitss.ru
- fruechtebox-expresszsnu.ru
- recambioselecue.ru
- entertaingadgetop.ru
URL
- https://www.curiosolucky.com/dos/
- https://magenta-melodious-garnet.glitch.me/public/rc.htm
- http://track.senderbulk.com/9164124/c?p=pDvu1IoaZGOuiG9hOsGCPPBXFmtx2_vWwJfaiQBzucIA8v9mjc3ztSyOneYxrKLjPngUzpA11TuGi1aI2aLIylOF1nHcpBoP4YzUvVEMYHtwY1nRlztPcQOoC6S6KSWuNNAgIAVnfapCVCgF1cOjSXtedVH_tWc1vLDH7FDQA0VZbtHORodc9jBuNuHh0DMH7zq9Mo6OMyLjnApzvQ3Kvw==
- https://edlyj.r.ag.d.sendibm3.com/mk/cl/f/sh/OycZvHuFo1eQsnbcJj9r9GQ4/Lf5JdugpPYQV
- https://u1427642.ct.sendgrid.net/ss/c/u001.d04lnC885Iiw-JDl08ZraoSXFe9HwA-SkWLpgNZDbZzgIKoIZZYrlHao4m6r2Vm6/4a0/vg0RNJ9pTvCzCNn5rS7A6Q/h0/h001.3pGdTVyFoOmaVG2IhlxshDsg0cLE6sckLThbmumHqI0
- https://docsend.com/view/q6f7ukbdeviagha2
- https://cloudflare-kol.github.io/out/red.html?url=aHR0cHM6Ly9zaG9ydHVybC5hdC80SlZnbg==
- https://shorturl.at/4JVgn
- https://system23cfb9.link.bmesend.com/api/LinkHandler/getaction2?redirectParam2=K09weU5vMDBKWXFUK0ZPdkw4azdKWHk5QlJsZkNXWXlLMUxiMHdXQU1YK3FFZGFsZG9ZQ2ZqNUdHd3ErZEpLeGpyeVE1U1hmU2xoSy9WemJySVEzQytGajZBVWE4em5jaEpuRHhEa05xOTZOcWxQRVdUN1g2S2ViR3YvZjN1K2dJZk9rQTRVajZmMD0=
- https://r.g.bing.com/bam/ac?!&&daydream=vasectomy&u=a1aHR0cHM6Ly9jeWJlcm5leGlsbHVtby56YS5jb20vVFZOUHIv==
- https://ctrk.klclick3.com/l/01J5V2NHDC0KB0P8B51Z9PCPZS_0
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Enable antivirus and anti-malware software and update signature definitions promptly. Using multi-layered protection is necessary to secure vulnerable assets.
- Patch and upgrade any platforms and software timely and make it into a standard security policy.
- Employ network intrusion detection and prevention systems to monitor and block malicious network activities.
- Implement network segmentation to limit lateral movement for attackers within the network.
- Never trust or open links and attachments received from unknown sources/senders.
- Implement advanced email filtering to detect and block phishing emails.
- Employ updated and robust endpoint protection solutions to detect and block malware.
- Develop and test an incident response plan to ensure a swift and effective response to security incidents.
- Enhance logging and monitoring capabilities to detect anomalous activities and unauthorized access.
- Conduct regular security audits and penetration testing to identify and address potential vulnerabilities.
- Regularly back up critical data and ensure that backup and recovery procedures are in place.

