Severity
High
Analysis Summary
A new ransomware called Lyrix was discovered by cybersecurity experts. It first appeared online on April 20, 2025, and mainly targets Windows systems. It is written in the Python programming language and turned into an EXE file using a tool called PyInstaller.
Lyrix is dangerous because it uses advanced tricks to hide from antivirus tools and security checks. It also blocks recovery methods on the system, making it very hard to fix the damage without paying the ransom.
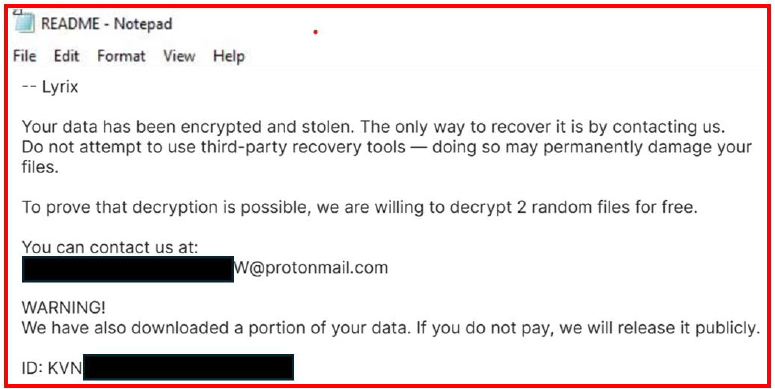
Once it enters a computer, Lyrix encrypts all important files using strong encryption methods (AES and RSA). The files are renamed with a strange extension (.02dq34jROu), and a note called README.txt is left in each folder. This note tells the victim that their data has been locked and stolen. The attackers offer to unlock two files for free and demand money to unlock the rest. If the victim doesn’t pay, they threaten to leak the stolen data.
Impact
- Financial Loss
- Information Disclosure
- Data Manipulation
Indicators of Compromise
MD5
d298fb4197d65eabf1ef427c2eb737f1
72a8f2c6e5628f5e8e3c4dc7dcdb93cb
SHA-256
fcfa43ecb55ba6a46d8351257a491025022f85e9ae9d5e93d945073f612c877b
77706303f801496d82f83189beff412d83a362f017cadecc7a3e349a699ce458
SHA1
b7c9ff6b8617f6e89fdf9c3c7f237db41ea9b5cd
2f45c203896790be01b132b0e3d5c5c5c27f0bc4
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Do not download or run unknown files or programs from untrusted websites or emails.
- Keep your Windows operating system and all software up to date with the latest security patches.
- Use strong, updated antivirus and endpoint protection software.
- Regularly back up important data to an external hard drive or secure cloud storage.
- Disable macros in Microsoft Office files by default.
- Limit user privileges; avoid giving admin rights to all users.
- Monitor systems for unusual behavior and set up alerts for possible ransomware activity.
- Use application allowlisting to block unauthorized programs from running.
- If infected, disconnect the affected system from the network immediately to prevent spread.

