Severity
High
Analysis Summary
A Linux variant of the relatively new ransomware outbreak known as Helldown has been revealed by cybersecurity researchers, indicating that the threat actors are expanding the scope of their attacks.
The Windows ransomware used by Helldown is based on the LockBit 3.0 algorithm. It seems that the gang may be expanding its current activities to target virtualized infrastructures using VMware, especially in light of the recent creation of ransomware that targets ESX. In mid-August 2024, researchers released the first public description of Helldown, characterizing it as a malicious ransomware gang that breaches target networks by taking advantage of security flaws. The cybercrime gang targets many well-known industries, including manufacturing, healthcare, telecommunications, and IT services.
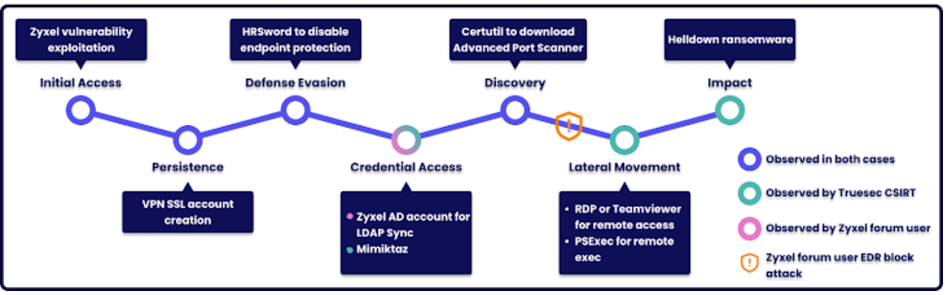
Like other ransomware groups, Helldown is infamous for using data leak websites to threaten to disclose stolen material to coerce victims into paying ransoms—a practice known as double extortion. Over three months, it is thought to have attacked at least 31 companies. In a report released earlier this month, researchers described Helldown attack chains that have been seen using internet-facing Zyxel firewalls to gain initial access. Then, they performed lateral movement, persistence, credential harvesting, network enumeration, defense evasion, and ransomware deployment.
According to the latest investigation, threat actors exploit known and undisclosed security holes in Zyxel equipment to gain network access. Using temporary users, they leverage these vulnerabilities to steal passwords and establish SSL VPN tunnels. After being launched, the Windows version of Helldown completes several actions before exfiltrating and encrypting the files, such as erasing system shadow copies and stopping several databases and Microsoft Office-related services. The machine is shut down, a ransom note is dropped, and the ransomware binary is erased to hide the evidence.
Its Linux counterpart has a limited set of features for searching and encrypting files, but not before listing and erasing all running virtual machines (VMs). It also lacks obfuscation and anti-debugging capabilities. There was no network communication, public key, or shared secret found in the static and dynamic study. This is significant because it asks how the attacker could provide a decryption tool.
Ransomware can write to image files when virtual machines are terminated before encryption. Static and dynamic analysis, however, shows that although this feature is there in the code, it is never used. All of these findings point to the ransomware's low level of sophistication and potential further evolution. It has been discovered that Helldown Windows artifacts behave similarly to DarkRace, which first appeared in May 2023 utilizing code from LockBit 3.0 before changing its name to DoNex.
Both codes are LockBit 3.0 variations. Given Darkrace and Donex's past rebrandings and their striking resemblance to Helldown, it is impossible to exclude Helldown being another rebrand. At this point, though, it is impossible to confirm this connection with certainty. This comes as researchers revealed another new ransomware family called Interlock, which has targeted European manufacturing companies as well as the government, technology, and healthcare industries in the United States. It can encrypt computers running Linux and Windows.
Impact
- Financial Loss
- Sensitive Data Theft
- Credential Theft
- File Encryption
Indicators of Compromise
MD5
- 140aad1f823157222af3da2d23de8789
- b81df159e7e338a3159f27ef3358094f
- be37cd010227d7b953b07b93d2e5dadc
- 9a31c68107a48fefe2944b0f5a1b0404
- 0260ec99d6d28c5c88f3fbce1de70772
- 24d265937b782a9398a1f6ceaa086dff
- 4a4d03743fd3a7ee1d03d89d0e3b8011
- 64cc86931bab241dcc08db03e659bcc5
SHA-256
- 7cd7c04c62d2a8b4697ceebbe7dd95c910d687e4a6989c1d839117e55c1cafd7
- 7731d73e048a351205615821b90ed4f2507abc65acf4d6fe30ecdb211f0b0872
- 3e3fad9888856ce195c9c239ad014074f687ba288c78ef26660be93ddd97289e
- 47635e2cf9d41cab4b73f2a37e6a59a7de29428b75a7b4481205aee4330d4d19
- cb48e4298b216ae532cfd3c89c8f2cbd1e32bb402866d2c81682c6671aa4f8ea
- 67aea3de7ab23b72e02347cbf6514f28fb726d313e62934b5de6d154215ee733
- 2b15e09b98bc2835a4430c4560d3f5b25011141c9efa4331f66e9a707e2a23c0
- 6ef9a0b6301d737763f6c59ae6d5b3be4cf38941a69517be0f069d0a35f394dd
SHA1
- 5de32f3a61dd692340545c3e7085678c2d557064
- f67d2108fcf1563ec11783d49e60e7d76f386d34
- 6d0a63dd7ce089dd1b25bd3ae544d5fef8515acc
- 511af9b9fb13d2295ba047917d1efa621e52086f
- 289f85ca00bd14ccc95fc7d4675470d3211801a9
- 29734bb3e264556b95fe92f45ba03e329e4fcde1
- 127d72408c87d866c72331fb0f16d13fef6a92ec
- 8ce3f9f92c6533d14ae2c8749936b4c59fcb95c5
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Implement robust multi-layered security measures to detect and respond to ransomware and cyber espionage activities.
- Conduct regular security assessments and penetration testing to identify and mitigate vulnerabilities in critical infrastructure and government systems.
- Deploy advanced threat detection tools, such as Endpoint Detection and Response (EDR) and Network Traffic Analysis (NTA), to monitor for suspicious activities and anomalies.
- Ensure timely patching and updating of all software and systems to close known security gaps.
- Use multi-factor authentication (MFA) and strong password policies to protect user accounts from unauthorized access.
- Segment networks to limit lateral movement within the organization in case of a breach.
- Develop and maintain an incident response plan that includes procedures for ransomware attacks and data breaches.
- Train employees on cybersecurity best practices and phishing awareness to reduce the risk of social engineering attacks.
- Regularly back up critical data and ensure backups are stored securely and are not accessible from the primary network.
- Collaborate with cybersecurity firms and government agencies for threat intelligence sharing and coordinated defense strategies.
- Implement encryption for sensitive data at rest and in transit to protect against data theft.
- Limit access to critical systems and data to only those individuals who require it for their role.
- Monitor for and immediately investigate the presence of known malware and indicators of compromise associated with state-sponsored groups.
- Engage in regular cybersecurity drills and exercises to ensure readiness for potential cyber incidents.
- Ensure legal and compliance measures are in place, particularly for industries subject to specific regulatory requirements.

