Severity
High
Analysis Summary
Cybersecurity researchers are warning about rising phishing campaigns that impersonate popular brands and use telephone-oriented attack delivery (TOAD), also known as callback phishing, to deceive victims.
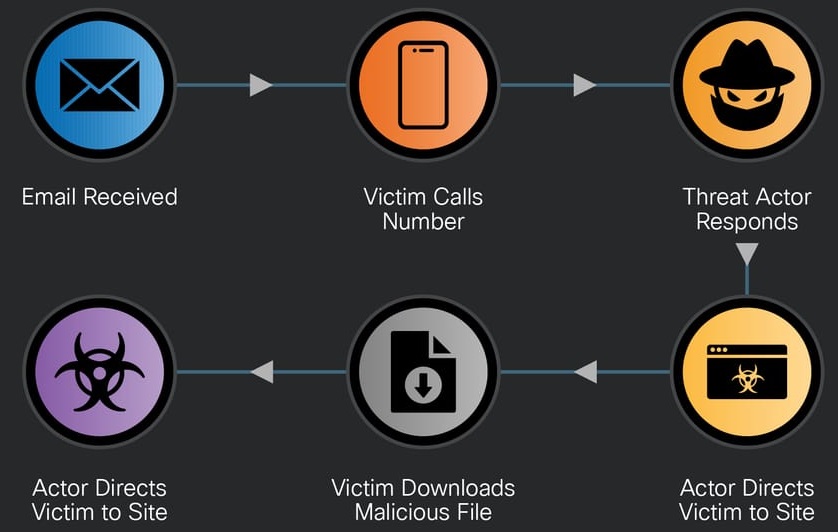
A Security Firm reports that many phishing emails with PDF attachments between May 5 and June 5, 2025, impersonated Microsoft, DocuSign, NortonLifeLock, PayPal, and Geek Squad. These emails often coax recipients into calling attacker-controlled phone numbers, where threat actors masquerade as customer support agents to steal sensitive data or install malware.
In TOAD attacks, emails typically claim account issues or payment problems, urging victims to call for resolution. Attackers use realistic call center tactics such as scripted interactions, hold music, and spoofed caller IDs, manipulating victims' emotions to extract credentials or install remote access tools like AnyDesk or TeamViewer. Many attackers leverage Voice over Internet Protocol (VoIP) numbers, which remain active for several days, enabling multi-stage social engineering operations while maintaining anonymity.
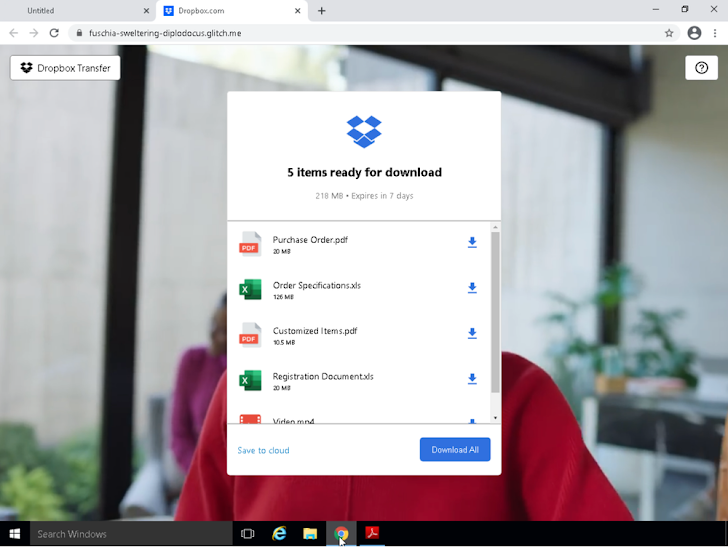
Additionally, PDF-based phishing campaigns embed malicious URLs within annotations, sticky notes, or QR codes, often pointing to fake Microsoft login pages or services like Dropbox. QR codes are frequently linked to authentic-looking websites to establish trust. The FBI recently warned about such tactics being used by groups like Luna Moth to breach networks by impersonating IT staff.
New campaigns are exploiting Microsoft 365’s Direct Send feature to spoof internal users without account compromise, delivering phishing emails from addresses like "<tenant_name>.mail.protection.outlook.com". This method has targeted over 70 organizations since May 2025. Unlike traditional BEC or vishing, these attacks exploit trusted internal communication channels to bypass scrutiny.
Meanwhile, a research revealed that large language models (LLMs) frequently suggest incorrect or unregistered login URLs when asked where to sign in to known brands, with 30% of these domains inactive and vulnerable to takeover by attackers for phishing.
Threat actors have also attempted AI poisoning, publishing fake Solana blockchain APIs to GitHub, promoting them through blog posts and forums to integrate malicious code into AI coding assistant suggestions. Furthermore, attackers are using illicit marketplaces like Hacklink to inject JavaScript or HTML into compromised .gov or .edu domains, manipulating search engine results to promote phishing sites. These techniques not only deceive users but also damage brand integrity and trust by associating official websites with malicious activity.
Impact
- Sensitive Information Theft
- Unauthorized Gain Access
- Security Bypass
Remediation
- Implement advanced email filtering to detect TOAD and PDF-based phishing emails
- Educate users on identifying callback phishing and suspicious QR codes
- Disable or restrict Microsoft 365 Direct Send feature if not needed
- Regularly audit VoIP call logs for unusual external contact numbers
- Enforce multi-factor authentication to protect against credential theft
- Monitor for brand impersonation attempts targeting your organization
- Use endpoint protection to block malware and remote access tool installations
- Review AI-generated code suggestions for malicious or unverified sources
- Scan organizational domains for injected malicious scripts or SEO manipulation
- Collaborate with security vendors for brand impersonation detection solutions
- Promptly patch systems and software to reduce exploit opportunities
- Limit user privileges to minimize potential damage from social engineering attacks

