Severity
High
Analysis Summary
APT17, a threat actor with ties to China, has been seen utilizing a known malware strain dubbed 9002 RAT to target Italian businesses and government institutions.
According to researchers, the two targeted attacks occurred on June 24 and July 2, 2024. On June 24, 2024, an Office document was utilized in the first campaign, but a link was used in the second. Both efforts asked the target to install the Skype for Business package via a link on a website that appeared to be run by the Italian government to spread a 9002 RAT variant.
The Google-owned Mandiant initially reported on APT17 in 2013 as a component of cyber espionage operations known as DeputyDog and Ephemeral Hydra, which took advantage of zero-day vulnerabilities in Microsoft Internet Explorer to compromise targets of interest. The adversary is known by several names, including Aurora Panda, Bronze Keystone, Dogfish, Elderwood, Helium, Hidden Lynx, and TEMP.Avengers. It shares some tooling overlap with another threat actor known as Webworm.
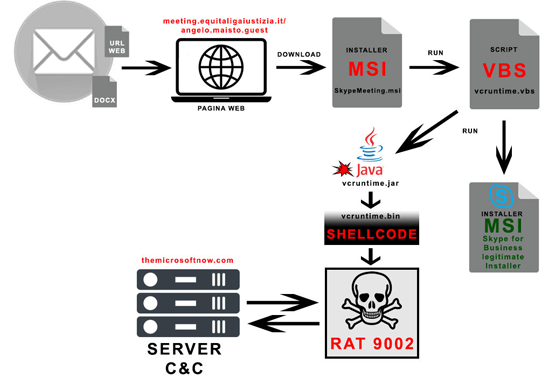
9002 RAT, also known as Hydraq and McRAT, gained attention in 2009 as the preferred cyber weapon in Operation Aurora, which targeted Google and other major corporations. It was then used in a different 2013 campaign called Sunshop when the attackers infected other websites with malicious redirection. The most recent attack chains use spear-phishing lures to deceive targets into clicking on a link that requests that they download the Skype for Business MSI installer ("SkypeMeeting.msi").
When the MSI package is launched, the legitimate chat software is installed on the Windows machine and a Java archive (JAR) file is executed using a Visual Basic Script (VBS). The shellcode that starts 9002 RAT is then decrypted and executed by the Java program. 9002 RAT is a modular trojan that may be used to do a variety of tasks, including managing processes, taking screenshots, enumerating files, monitoring network traffic, and executing additional commands that are sent from a remote server to aid in network discovery.
There seems to be a continuous upgrade cycle for the malware, including diskless versions. It is made up of different modules that the threat actor activates as necessary to lessen the chance of interception. The presence of reputable government links on the infected page raises the possibility that the cybercriminal gained access to private user data belonging to individuals or companies in Italy that had previously been impacted.
Impact
- Cyber Espionage
- Command Execution
- Exposure of Sensitive Data
Indicators of Compromise
Domain Name
- themicrosoftnow.com
- meeting.equitaligaiustizia.it
MD5
- 9847280ad804970d7a00715cd4d5468a
- 9d97d3844d4c0bb06a73257aab6c02b8
- 959f60c447728e14d25628ab5427a312
- a9648fbd4fd89787fda7fe3f2a8964b2
- a7142d05f6995e9783f2b8bf184fa8f4
- 19aff0a43f80919a6113020d3ff38300
SHA-256
- 28808164363d221ceb9cc48f7d9dbff8ba3fc5c562f5bea9fa3176df5dd7a41e
- e024fe959022d2720c1c3303f811082651aef7ed85e49c3a3113fd74f229513c
- d6b348976b3c3ed880dc41bb693dc586f8d141fbc9400f5325481d0027172436
- c0f93f95f004d0afd4609d9521ea79a7380b8a37a8844990e85ad4eb3d72b50c
- caeca1933efcd9ff28ac81663a304ee17bbcb8091d3f9450a62c291fec973af5
- de19e0163af15585c305f845b90262aee3c2bdf037f9fc733d3f1b379d00edd0
SHA-1
- c9d39d7a8d16c463e6b7f7359df8b0bb903db4df
- be72b1328454159f8781b6d9007009ab26cb9ba5
- 245c2ecf5cd4993e9e56e8a9392e0157611aa42e
- 51a25e161ac3d83a270bcc8cda3cee54f8266522
- f04ec4733cd245b80839ba8b1138d6111fe5cf23
- f0db6e0967c534fa0326c9db009d0f22e0112a6b
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Never trust or open links and attachments received from unknown sources/senders.
- Implement multi-factor authentication to add an extra layer of security to login processes.
- Regularly monitor network activity for any unusual behavior, as this may indicate that a cyberattack is underway.
- Organizations need to stay vigilant and follow best practices for cybersecurity to protect their systems and data from potential threats. This includes regularly updating software and implementing strong access controls and monitoring tools.
- Develop a comprehensive incident response plan to respond effectively in case of a security breach or data leakage.
- Maintain regular backups of critical data and systems to ensure data recovery in case of a security incident.
- Adhere to security best practices, including the principle of least privilege, and ensure that users and applications have only the necessary permissions.
- Establish a robust patch management process to ensure that security patches are evaluated, tested, and applied promptly.
- Conduct security audits and assessments to evaluate the overall security posture of your systems and networks.
- Implement network segmentation to contain and isolate potential threats to limit their impact on critical systems.

