Severity
High
Analysis Summary
In a newly uncovered campaign, the DoNot APT group—also known as APT-C-35, Mint Tempest, Origami Elephant, and Viceroy Tiger—has escalated its cyber-espionage activities by targeting a European foreign affairs ministry. According to a report by a security firm, the group, active since at least 2016 and historically focused on South Asia, is now expanding its operations to gather European diplomatic intelligence.
The campaign began with spear-phishing emails impersonating defense officials, referencing an event titled “Italian Defence Attaché Visit to Dhaka, Bangladesh,” and containing a Google Drive link to a malicious RAR archive named SyClrLtr.rar. This archive housed a disguised executable (notflog.exe) posing as a PDF file. When executed, it triggered a multi-stage infection chain deploying a batch script (djkggosj.bat) and establishing persistence via a scheduled task named PerformTaskMaintain.
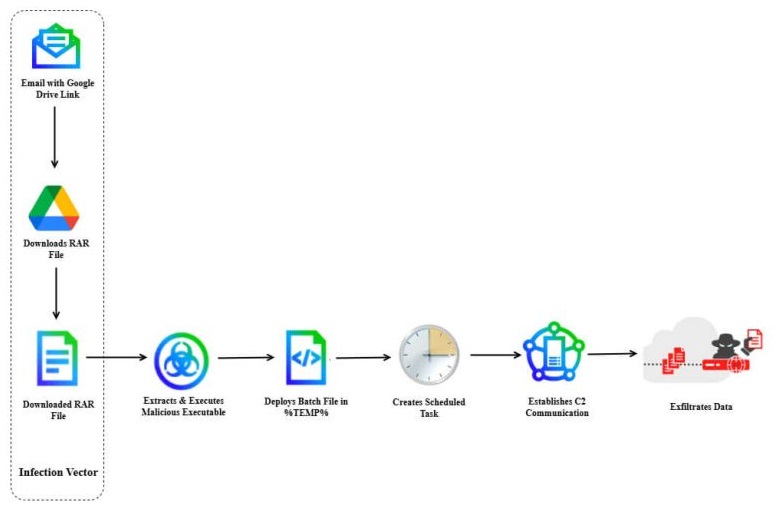
The malware was identified as LoptikMod, a backdoor exclusively used by DoNot APT since 2018. Its code included strings marked “Loptik” and used runtime decoding to evade static analysis. The malware employed dynamic API loading, minimal import tables, and anti-virtual machine evasion techniques to avoid detection.
It created a mutex named 08808 to ensure only one running instance, then dropped a DLL payload (socker.dll) and another batch file (sfs.bat) to set up a second scheduled task, MicorsoftVelocity, ensuring long-term persistence. Upon infection, it collected system metadata, such as CPU model, OS version, hostname, username, and installed applications, encrypting this data with AES and Base64 before sending it via HTTPS POST requests to its command-and-control domain, which mimicked legitimate services to avoid detection.
The security firm attributed the operation to DoNot APT based on infrastructure and tactics, concluding that the group’s focus is broadening towards gathering sensitive political, military, and economic intelligence within Europe.
Impact
- Sensitive Information Theft
- Long-Term Persistence
- Operational Disruption
Indicators of Compromise
Domain Name
- totalservices.info
IP
- 64.52.80.252
MD5
- 893561ff6d17f1e95897b894dde29a2a
SHA-256
- 4d036e0a517774ba8bd31df522a8d9e327202548a5753e5de068190582758680
SHA1
- 59269cc2d0c169205ceea420b2b6a1a4dedc1700
Remediation
- Implement advanced email filtering to block spear-phishing attempts with malicious attachments
- Educate staff on identifying phishing emails and suspicious cloud links
- Monitor scheduled tasks creation for unauthorized persistence mechanisms
- Deploy endpoint detection and response (EDR) tools to identify malware behaviors
- Regularly update and patch operating systems and applications to reduce exploit risk
- Use application whitelisting to prevent execution of unauthorized files
- Conduct threat hunting for known indicators linked to DoNot APT campaigns
- Block access to known malicious command-and-control domains at the firewall level
- Analyze network traffic for unusual encrypted outbound connections
- Restrict macro and script execution from email attachments unless validated

