Severity
High
Analysis Summary
The recently disclosed "ReVault" vulnerability set affects millions of Dell laptops, particularly those used by government agencies, cybersecurity professionals, and enterprises. These critical vulnerabilities reside in the Broadcom BCM5820X chip embedded in Dell’s ControlVault3 and ControlVault3+ firmware. This chip underpins Dell’s hardware-based security architecture by storing sensitive data like passwords and biometric credentials.
Researchers uncovered five high-severity vulnerabilities ranging from out-of-bounds read/write flaws to unsafe deserialization and arbitrary memory manipulation that can lead to arbitrary code execution, firmware tampering, and persistent device compromise.
These vulnerabilities impact more than 100 Dell Latitude and Precision models, widely deployed in high-security environments. Attackers can exploit ControlVault’s Windows APIs without administrative privileges, potentially implanting malicious code that survives even a full OS reinstallation. One of the most alarming findings is that compromised firmware can be manipulated to accept any fingerprint, including those from non-human objects like vegetables, for authentication. This effectively breaks biometric security and provides a stealthy pivot point for deeper system access, undermining the laptop's core trust anchor.
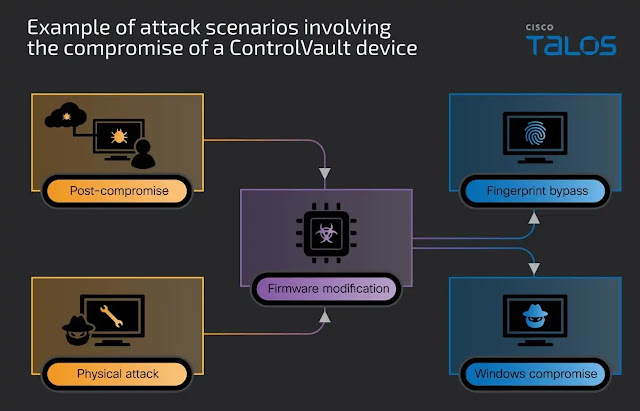
In addition to remote exploitation, the vulnerabilities facilitate physical attacks. Researchers demonstrated how an attacker could directly connect to the Unified Security Hub (USH) board via USB after briefly opening the chassis, bypassing system logins and encryption mechanisms. This adds another layer of risk, especially in scenarios where laptops may be left unattended or accessed by malicious insiders. A researcher's demonstration showing a spring onion unlocking a compromised laptop highlights the severity of the biometric bypass.
Dell has responded by collaborating with Broadcom to develop and release firmware patches beginning in March 2025. As of June 13, Dell started notifying customers and releasing updates through both Windows Update and its support site. However, due to restrictive update policies in many enterprises, organizations are strongly advised to manually verify and apply updates. Dell ControlVault3 versions earlier than 5.15.10.14 and ControlVault3+ versions before 6.2.26.36 are affected. The incident underscores the critical need to assess hardware security not just software and prioritize firmware updates as a key part of a comprehensive cybersecurity strategy.
Impact
- Sensitive Credential Theft
- Gain Access
- Security Bypass
Indicators of Compromise
CVE
CVE-2025-24311
CVE-2025-25050
CVE-2025-24922
CVE-2025-25215
CVE-2025-24919
Remediation
- Apply firmware updates to Dell ControlVault3 version 5.15.10.14 or later and ControlVault3+ version 6.2.26.36 or later via Dell’s support website or Windows Update.
- Manually confirm that firmware patches have been deployed, especially in enterprise environments with restricted update policies.
- Regularly audit and monitor firmware integrity across all Dell devices to detect unauthorized modifications.
- Limit physical access to laptops to prevent direct hardware-based exploitation through the USH board.
- Disable fingerprint or smart card authentication temporarily if not essential, until firmware is secured.
- Use advanced security tools that support firmware-level scanning and anomaly detection.
- Include hardware component risk evaluations in procurement and regular security assessments.
- Educate users and IT administrators on firmware risks and ensure they are aware of update procedures.
- Review Dell Security Advisory DSA-2025-053 for the full list of affected models and recommended fixes.

