Severity
High
Analysis Summary
Threat actors are leveraging public GitHub repositories to host malicious payloads distributed via Amadey malware as part of campaigns observed in April 2025. Researchers reported that Malware-as-a-Service (MaaS) operators created fake GitHub accounts to host tools, payloads, and Amadey plugins to bypass web filtering. The attack chain uses a malware loader called Emmenhtal (aka PEAKLIGHT) to deliver Amadey, which then downloads various payloads like Lumma Stealer, RedLine Stealer, and Rhadamanthys Stealer from GitHub.
The campaign mirrors tactics seen in a February 2025 phishing attack that used billing-themed lures to distribute SmokeLoader via Emmenhtal targeting Ukrainian entities. While both Emmenhtal and Amadey deliver secondary payloads such as info stealers, Amadey is more advanced, capable of collecting system information and extending functionality through DLL plugins for credential theft or screenshot capture. Researchers also identified three GitHub accounts (Legendary99999, DFfe9ewf, and Milidmdds) used for hosting malicious plugins and payloads, which GitHub has since removed.
Some JavaScript files found matched Emmenhtal scripts from previous campaigns, with Emmenhtal loader files serving as vectors for Amadey, AsyncRAT, and legitimate PuTTY.exe downloads. A Python script incorporating embedded PowerShell commands was also uncovered, likely representing an evolved Emmenhtal version.
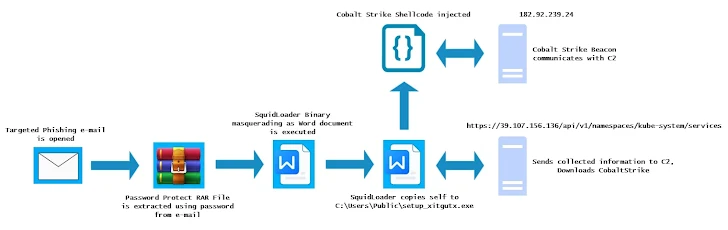
Separately, another security firm detailed a phishing campaign deploying SquidLoader against financial institutions in Hong Kong, with possible activity in Singapore and Australia. SquidLoader incorporates anti-analysis, anti-sandbox, and anti-debugging techniques, eventually deploying a Cobalt Strike beacon for remote access.
Additional campaigns include phishing attacks using invoice and tax themes to deploy ConnectWise ScreenConnect, SSA-themed lures to harvest credentials or sync victims’ phones to steal 2FA codes, Logokit phishing kits hosted on AWS, QR codes in PDFs mimicking Microsoft login portals (termed Scanception), ClickFix tactics to deliver Rhadamanthys Stealer and NetSupport RAT, and cloaking-as-a-service (CaaS) offerings like Hoax Tech to hide malicious sites from scanners. Researchers reported that QR codes accounted for 57% of campaigns using advanced tactics in 2024, with password-protected archives also used to evade security scanning.
Impact
- Credential Theft
- Malware Deployment
- Unauthorized Access
- Security Bypass
Indicators of Compromise
IP
- 39.107.156.136
- 8.140.62.166
- 38.55.194.34
- 47.116.178.227
- 121.41.14.96
- 185.156.73.73
- 185.215.113.209
- 185.215.113.75
MD5
- d2a909dffe9f645d5da592a992126e63
- 2a571238803846eeacd1274c54048d9c
- 5279efa6a0d9bca7541748078f0555ee
- d61587e79217f91278c13e81e59a2e18
- f627cf464b6f0a98a20076a2d3e18937
- b5086bc2224f44d7331b98656c1a009b
- 99b5b06ca2f41e988a6bafe7bf2d51f9
- 22892b8303fa56f4b584a04c09d508d8
- dd3fa6ae969ccdf3d221bd95ffef5a7b
- 176c3de6c4a1ac5c34b6d6be54fca774
- e72e6f28b3fc6bfe087a7bdffb068443
SHA-256
- bb0f370e11302ca2d7f01d64f0f45fbce4bac6fd5613d8d48df29a83d382d232
- b2811b3074eff16ec74afbeb675c85a9ec1f0befdbef8d541ac45640cacc0900
- 6960c76b624b2ed9fc21546af98e1fa2169cd350f37f6ca85684127e9e74d89c
- 9dae4e219880f0e4de5bcba649fd0741e409c8a56b4f5bef059cdf3903b78ac2
- 34d602d9674f26fa2a141c688f305da0eea2979969f42379265ee18589751493
- a244bfcd82d4bc2de30fc1d58750875b638d8632adb11fe491de6289ff30d8e5
- 2d371709a613ff8ec43f26270a29f14a0cb7191c84f67d49c81d0e044344cf6c
- 87618787e1032bbf6a6ca8b3388ea3803be20a49e4afaba1df38a6116085062f
- 21cf7da02e01b3c2317178395eff873e50ab9b8f27a23ffed37b2efff8fd6b90
- 35c1eb5ff8913c4ca4feb712e05354772146247bdb4b337868c687730f201023
- 0334cd1b8ab17203179da1ae77c1fad97ddf794cc63a6048aca664956d10b2ca
SHA1
- 5f73525f85770f0451ab97a61dfa29cd16275702
- bf0a9974fa95bac158557802c0d1792990724fd1
- 117de3290e60dddac7c7c234690a5a55c19595ff
- a3a20e2d1ea20b0870ba1fa53c69b030d18feb72
- e8fa82460c34c947ed9149ec17fd4d5cfca6c476
- ab8af51a969cb11025d08dce7a940c6c7ccf6d83
- d38f8bdec3a7bc77186e19c10cb0099361f50e47
- e1d65daaf338663006014f7d86eea5aebf142134
- 8975046c5cdbab0e36aa9ccad61b05a898810079
- 73efc19941b9341f7735a616888b4f306b4815eb
- 50c5d24005f477410c633af5d2dd90e6bcb8f116
URL
- https://39.107.156.136/api/v1/namespaces/kube-system/services
- https://8.140.62.166/api/v1/namespaces/kube-system/services
- https://38.55.194.34/api/v1/namespaces/kube-system/services
- https://47.116.178.227/api/v1/namespaces/kube-system/services
- https://121.41.14.96/api/v1/namespaces/kube-system/services
- http://pivqmane.com/doc/fb.mp4
- http://pivqmane.com/testonload.mp4
- http://185.215.113.16/test/amnew.exe
- http://185.215.113.43/Zu7JuNko/index.php
Remediation
- Block all threat indicators at your respective controls
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls
- Use strict GitHub domain filtering to block malicious repository access
- Implement endpoint protection to detect Amadey and Emmenhtal activity
- Monitor PowerShell execution for suspicious embedded commands
- Block known malicious IP addresses hosting payloads
- Apply sandbox analysis to detect anti-analysis and anti-debug techniques
- Deploy network intrusion detection systems for Cobalt Strike beacons
- Train users to identify phishing emails with invoice, SSA, and tax themes
- Warn users against scanning unknown QR codes in emails
- Use email security solutions to detect phishing kits and Logokit-based attacks
- Monitor for installation of unauthorized remote access tools like ScreenConnect
- Inspect archives in emails even if password protected before allowing access
- Block execution of unsigned DLL plugins to prevent Amadey feature expansion
- Use domain-based filtering to block access to cloaking-as-a-service infrastructure
- Conduct regular threat hunting for AsyncRAT, SquidLoader, and information stealers
- Enforce application whitelisting to block unauthorized script execution

