Severity
High
Analysis Summary
A recent cyberattack campaign attributed to the advanced persistent threat group Stealth Falcon (also known as FruityArmor) targeted a major Turkish defense contractor using a previously unknown zero-day vulnerability (CVE-2025-33053). The vulnerability allowed remote code execution (RCE) by manipulating the working directory used by legitimate Windows tools. Delivered via a malicious .url file disguised as a damage report (“TLM.005_TELESKOPIK_MAST_HASAR_BILDIRIM_RAPORU.pdf.url”), the file redirected a legitimate diagnostic tool, iediagcmd.exe, to a malicious WebDAV server, enabling the execution of a remote payload. This technique exploited the .NET Process.Start() method's search order, allowing the attackers to execute malware (route.exe) from the attacker-controlled server and bypass signature-based defenses through process hollowing.
Microsoft addressed this flaw in its June 2025 Patch Tuesday release following a responsible disclosure by researchers. The campaign employed a multi-stage infection chain, culminating in the deployment of “Horus Agent”, a custom implant based on the Mythic C2 framework.
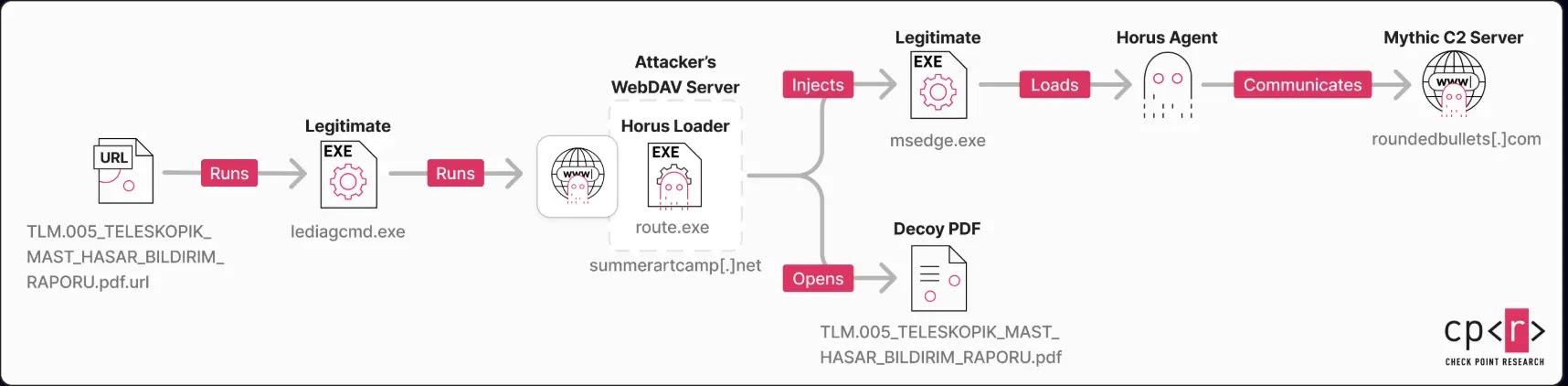
This new malware, named after the Egyptian sky god Horus, builds on the group’s earlier Apollo implant and incorporates advanced evasion techniques such as code virtualization, API hashing, and string encryption to avoid analysis. It is primarily used for initial reconnaissance, enabling the group to evaluate a compromised system’s value before deploying additional, more advanced payloads.
In addition to Horus Agent, researchers uncovered several previously unknown tools in Stealth Falcon’s arsenal, including a DC Credential Dumper that accesses virtual disk copies to bypass file locks, a passive backdoor that executes shellcode on demand, and a custom RC4-encrypted keylogger. These tools reflect the group's emphasis on stealth, persistence, and minimal exposure. The use of passive backdoors and custom tooling allows them to maintain a low footprint while still achieving comprehensive system access and data exfiltration capabilities.
Stealth Falcon, active since at least 2012, has a history of targeting government and defense sectors in the Middle East and Africa, with recent campaigns affecting entities in Turkey, Qatar, Egypt, and Yemen. The group uses repurposed legitimate domains, registered via NameCheap with common TLDs (.net/.com), to blend malicious traffic with legitimate activity, complicating detection and attribution. Their persistent evolution, combined with the exploitation of zero-day vulnerabilities and clever abuse of Windows utilities, demonstrates a high level of sophistication, posing a significant threat to national security and critical infrastructure worldwide.
Impact
- Sensitive Data Theft
- Remote Code Execution
- Security Bypass
Indicators of Compromise
CVE
- CVE-2025-33053
Domain Name
- roundedbullets.com
- summerartcamp.net
- downloadessays.net
- joinushealth.com
- healthherofit.com
- worryfreetransport.com
- radiotimesignal.com
- fastfilebackup.com
- cyclingonlineshop.com
- luxuryfitnesslabs.com
- purvoyage.com
MD5
- 33922ecb35a51a1f1999c4fef4c10187
- 7cae6334841a2750b8a4e801ee106a94
- b2d5f620b672bf58a68731a68d62dc82
- ead247b90ebd4aad7a4cf29f0e4eb111
- 9dd15d21ff456e525ef4fba26eaedc0d
- 04409d6fb02c66e4a928c5c7bf1cf663
- a17d21baa4329d6affb6f0436efc3ce2
- 5cd9a21ca2d496210caf3ce8362c309b
SHA-256
- ba5beb189d6e1811605b0a4986b232108d6193dcf09e5b2a603ea4448e6f263c
- e0a44274d5eb01a0379894bb59b166c1482a23fede1f0ee05e8bf4f7e4e2fcc6
- da3bb6e38b3f4d83e69d31783f00c10ce062abd008e81e983a9bd4317a9482aa
- 8291b886cce1f0474db5b3dc269adf31d1659b7d949f62ea23608409d14b9ceb
- 3b83250383c2a892e0ca86e54fcc6aca9960fc4b425ab9853611ff3e5aa2f9c6
- 46c95af6fea41b55fa0ab919ec81d38a584e32a519f85812fe79a5379457f111
- 0598e1af6466b0813030d44fa64616eea7f83957d70f2f48376202c3179bd6b1
- db7364296cc8f78981797ffb2af7063bba97e2f6631c29215d59f4979f8b4fce
SHA1
- 4f0365798d32b282ba4031b3809cf088152ab3e1
- 4d8cf62110f705da782742359e42a4d7501039d2
- 87901a7795fe5a9934be63ba06f4a5732a937295
- 6940459f66f7e549ae0da76b1ff3d544675e1b24
- 403e2c078bc24636ef1be8f6c37ec1c127dc65a9
- 7eb09aceefa1d0143af4bbc43d6cd880e4c49fa5
- 12494915133ec45c8fd69ce7ce8c20cb53397f50
- 50190eb15d272cb579ea1324adddf3c989b76281
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Use Microsoft Automatic Update to apply the appropriate patch for your system, or the Microsoft Security Update Guide to search for available patches.
- Use advanced email security solutions to detect and block malicious .url files and spear-phishing attempts, especially those with archived attachments.
- Disable or restrict WebDAV client functionality in enterprise environments to prevent abuse of remote file execution techniques.
- Monitor or block the execution of legacy utilities like iediagcmd.exe unless explicitly required, as they can be exploited for code execution.
- Use endpoint detection and response (EDR) tools to identify suspicious behaviors, such as Process.Start() anomalies, process hollowing, or execution from uncommon directories.
- Monitor network traffic for connections to suspicious or newly registered .net/.com domains, especially those mimicking legitimate infrastructure.
- Conduct sandbox analysis on unknown .url, .exe, or payload files, especially those linked to defense sector communications.
- Watch for unusual access to Active Directory or signs of credential dumping, particularly with tools bypassing standard file locks.
- Include Indicators of Compromise (IOCs) and behaviors linked to Mythic-based implants like Horus Agent in proactive threat hunts.
- Enforce allow-listing policies to restrict execution only to approved applications, reducing the risk of unauthorized tool usage.
- Provide regular security awareness training to high-risk staff (e.g., defense, government sectors) about spear-phishing and advanced threat tactics.

