Severity
High
Analysis Summary
Rhysida ransomware group claims that it has breached the Abdali Hospital in Jordan and added it to the victim list on its website. The gang also published images of stolen documents such as contracts, ID cards, and other sensitive data to prove the attack.
Abdali Hospital is a 200-bed multi-specialty hospital in Al-Abdali, Amman, Jordan. It provides care to patients in various specialties. Rhysida group claims to have committed the theft of a multitude of sensitive data that it is auctioning for 10 BTC. The group plans to sell the stolen data to a single buyer as its usual practice, and if the data doesn’t get sold within seven days of the announcement, it will be made public.
This isn’t the first time the Rhysida ransomware gang has breached a critical infrastructure. Near the end of November, the group claimed to have attacked and stolen data from King Edward VII’s Hospital in London. The group was also behind the data breach at the British Library and China Energy Engineering Corporation. The Rhysida ransomware group has been around since at least May 2023 and has claimed 62 high-profile victims since the start of its operations.
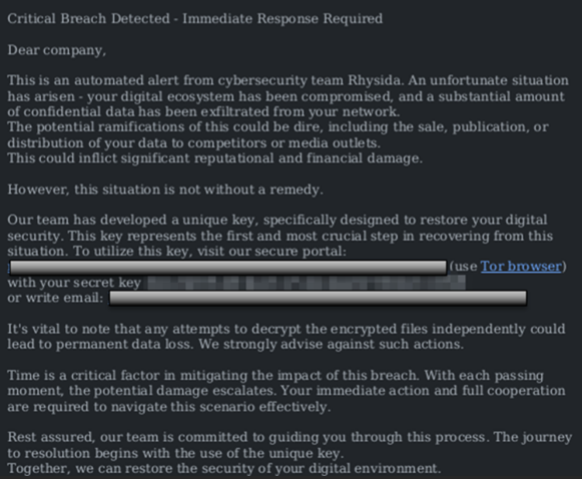
Rhysida has targeted organizations in numerous sectors like healthcare, education, information technology, manufacturing, and government. Most victims of the gang are targeted whenever they get the opportunity. Researchers have observed instances of the Rhysida threat actors operating in a ransomware-as-a-service (RaaS) space, leasing out their ransomware tools and infrastructure in a profit-sharing model, meaning that any ransoms paid are split between the operators of Rhysida and the affiliates.
The ransomware gang is known for taking advantage of Internet-facing remote services such as RDPs and VPNs to gain initial access to the targeted networks and maintain persistence. The group also relies on stolen credentials and uses them to authenticate to the internal VPN access points. It has exploited Zerologon (CVE-2020-1472) in Microsoft’s Netlogon Remote Protocol for phishing. The threat actors also use living-off-the-land techniques like network administration tools that are built into the operating system to perform malicious activities.
Impact
- Financial Loss
- Sensitive Data Theft
- File Encryption
Remediation
- Regularly back up critical data and systems. In the event of a successful attack or compromise, having recent backups can help you restore operations and minimize data loss.
- Implement multi-factor authentication to add an extra layer of security to login processes.
- Regularly monitor network activity for any unusual behavior, as this may indicate that a cyberattack is underway.
- Organizations need to stay vigilant and follow best practices for cybersecurity to protect their systems and data from potential threats. This includes regularly updating software and implementing strong access controls and monitoring tools.
- Develop a comprehensive incident response plan to respond effectively in case of a security breach or data leakage.
- Adhere to security best practices, including the principle of least privilege, and ensure that users and applications have only the necessary permissions.
- Establish a robust patch management process to ensure that security patches are evaluated, tested, and applied promptly.
- Conduct security audits and assessments to evaluate the overall security posture of your systems and networks.
- Implement network segmentation to contain and isolate potential threats to limit their impact on critical systems.

