Severity
High
Analysis Summary
On December 18, 2024, a malicious package named "ethereumvulncontracthandler" was discovered on the npm package registry, masquerading as a library intended to detect vulnerabilities in Ethereum smart contracts. The package published by a user named "solidity-dev-416," has been downloaded 66 times as of the latest report. Upon installation, it deploys an open-source remote access trojan (RAT) called Quasar RAT onto developer systems which establishes persistence by modifying the Windows Registry and connects to a command-and-control (C2) server to receive further instructions. Despite the malware’s heavy obfuscation including Base64 and XOR encoding, the RAT effectively enables the attacker to maintain full control over the victim's system.
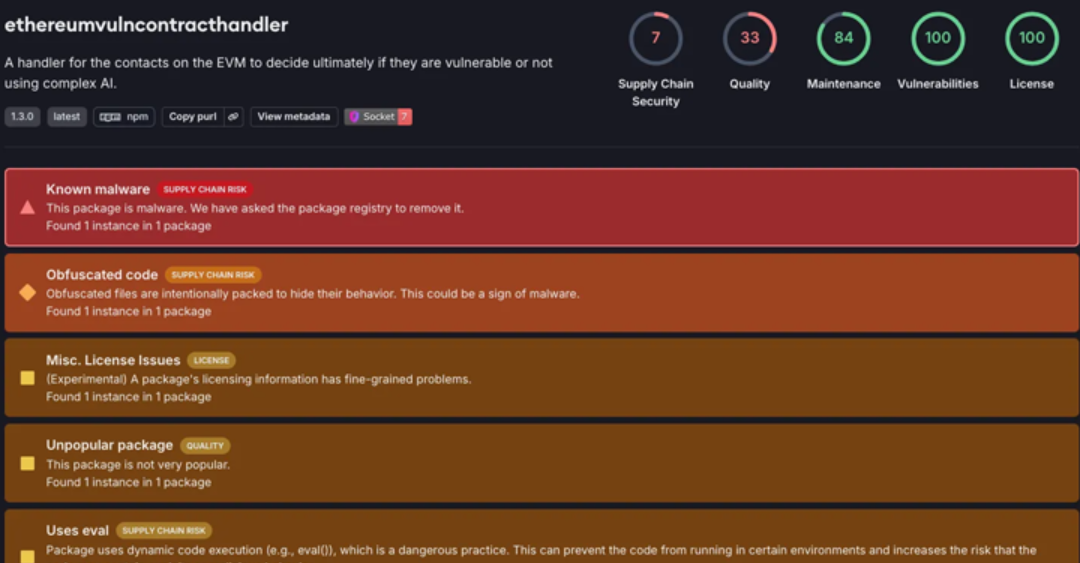
According to the researchers, the malicious package was specifically designed to evade detection leveraging multiple layers of obfuscation to resist analysis. The attacker ensured the payload would not execute in sandboxed environments by implementing checks that prevent the code from running in virtual machines or debugging environments. After bypassing these checks the malicious script silently executes PowerShell commands to launch the Quasar RAT which then connects to a C2 server (captchacdn[.]com:7000). This C2 communication allows the attacker to manage the compromised machine exfiltrate sensitive information, and catalog infected hosts potentially turning them into a botnet.
Quasar RAT, originally released in 2014 on GitHub has been employed by cybercriminals and espionage actors in a variety of campaigns, and its usage in this attack highlights its continued relevance. This remote access tool grants attackers full surveillance and control over infected machines enabling them to run further malicious operations, steal data, or deploy additional payloads. As the RAT establishes persistence, it ensures that the victim's machine remains compromised for ongoing exploitation, making the victim an ideal target for sustained attacks or further cyber espionage activities.
This incident highlights a broader trend in the cybersecurity world where attackers are increasingly targeting open-source repositories and package registries like npm. In parallel a study conducted by Socket, Carnegie Mellon University, and North Carolina State University exposed the use of fake stars on GitHub to artificially boost the popularity of malicious repositories. The study found that 60% of accounts involved in fake star campaigns exhibited suspicious activity patterns, and these artificial metrics were commonly used to promote repositories associated with pirated software game cheats, and cryptocurrency bots. This phenomenon demonstrates the vulnerabilities of relying solely on metrics like star count to assess the trustworthiness of open-source projects.
The combination of malicious npm packages and the manipulation of repository popularity through fake stars underscores the growing risk in the open-source ecosystem. As attackers continue to exploit these systems both developers and users must be more vigilant about the sources of their dependencies and the reputation of repositories. GitHub has been working to mitigate the impact of fake stars by removing fake accounts but the overall lesson is clear: automated metrics like star counts are not reliable indicators of quality or security, and they should be accompanied by thorough reviews and scrutiny before trust is granted to any open-source package.
Impact
- Cyber Espionage
- Sensitive Data Theft
- Gain Access
- Financial Loss
Indicators of Compromise
Domain Name
- jujuju.lat
- captchacdn.com
IP
- 154.216.17.47
MD5
- dd89f166318c7640673dc83253874f85
SHA-256
- 9c3d53c7723bfdd037df85de4c26efcd5e6f4ad58cc24f7a38a774bf22de3876
SHA1
- c6d10f65f6ff4df23404ac521f1d3db79264657e
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Regularly monitor and audit npm packages for malicious activities, ensuring that all packages are thoroughly vetted before being published.
- Developers should carefully review the code and dependencies of any package before using it, especially when downloaded from open-source repositories. Avoid using packages from unknown or untrusted authors.
- Use security tools that automatically analyze npm packages for potential malicious code, and deploy sandbox environments to execute and validate code in a controlled manner before it reaches production systems.
- npm should continue improving their security protocols, implementing stricter validation mechanisms for package submissions, and increasing scrutiny over new or lesser-known package authors.
- Ensure that systems are configured to monitor outbound traffic and block communication with known malicious command-and-control (C2) servers, such as "captchacdn[.]com" in this case.
- Raise awareness among developers about common evasion techniques like obfuscation (Base64, XOR encoding) and provide guidelines on how to identify them during code reviews.
- Use integrity checksums (e.g., SHA256) and digital signatures to ensure that the downloaded packages have not been tampered with.
- Require MFA for publishing and managing npm packages to reduce the risk of unauthorized package uploads.
- Ensure that all developer systems are up to date with security patches to minimize the risk of malware exploitation.
- Integrate threat intelligence feeds into development and CI/CD pipelines to detect and block known malicious packages and repositories before they can be incorporated into production.
- Developers and users should verify the credibility of repositories by looking beyond star counts, considering other factors like the number of contributors, recent activity, and community feedback before relying on open-source projects.
- Establish peer review processes within development teams to analyze and approve code dependencies before integration into projects, helping to catch potential security issues early.

