Severity
High
Analysis Summary
A sophisticated cyberattack campaign known as Operation SyncHole has been uncovered, attributed to the Lazarus Group. This advanced persistent threat (APT) operation targeted at least six organizations in South Korea, including those in the software, IT, financial, semiconductor, and telecommunications sectors. The true number of affected entities may be higher.
The attackers began with watering hole tactics, compromising popular media websites to selectively redirect users of interest to malicious domains. These sites delivered an attack chain exploiting a one-day vulnerability in Innorix Agent, a browser-integrated file transfer tool commonly used in administrative and financial systems. Exploiting this flaw enabled lateral movement within networks and deployment of known Lazarus malware such as ThreatNeedle and LPEClient.
Further investigation revealed an additional zero-day vulnerability in the same software, which was patched before active exploitation was observed. Another attack vector involved Cross EX, a legitimate tool used to support security functions in various browser environments. The malware ran in memory within trusted processes like SyncHost.exe, complicating detection efforts. The infection chain often began with vulnerabilities in these third-party tools, highlighting a consistent and calculated method of infiltration.
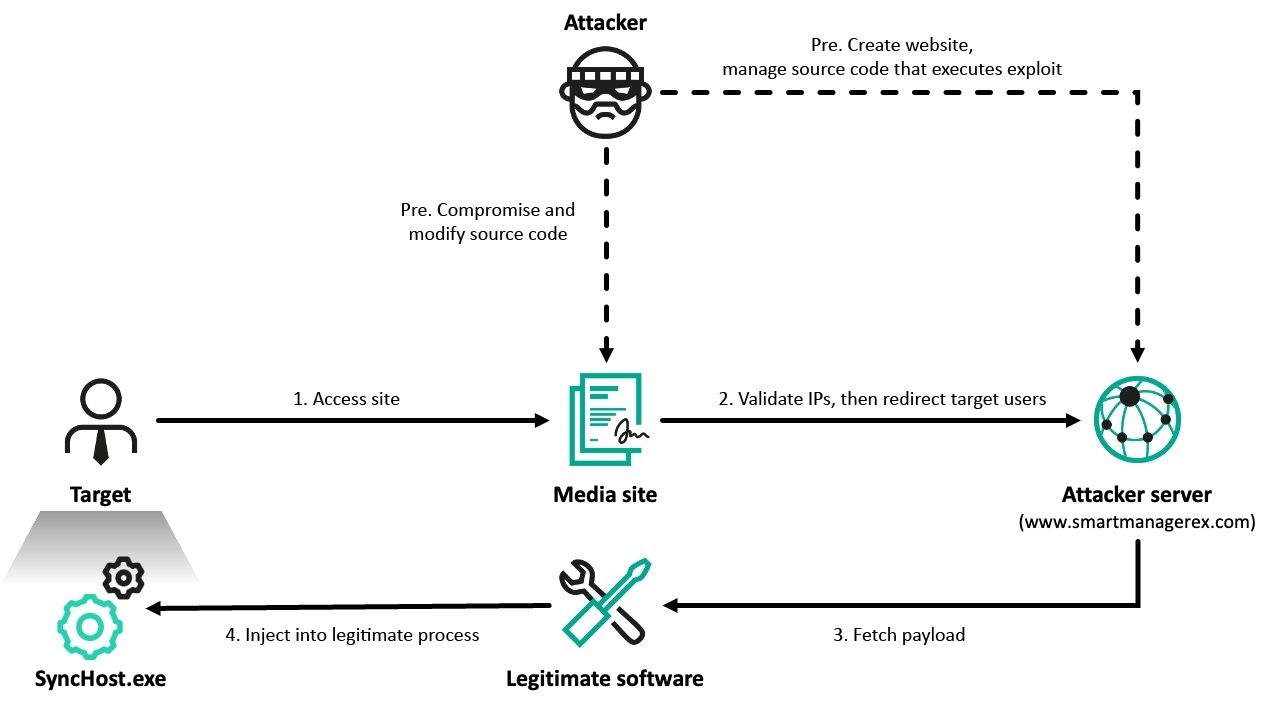
This campaign emphasizes broader cybersecurity concerns around third-party browser plugins and helper tools—especially those that are region-specific or outdated. These components typically have deep integration with browser environments and elevated privileges, making them attractive targets for threat actors.
To defend against such threats, organizations should ensure timely software updates, conduct thorough cybersecurity audits to identify vulnerabilities, and adopt solutions that provide real-time protection, deep threat visibility, and extended detection and response capabilities. Proactive threat intelligence and timely remediation are critical to preventing widespread compromise from well-resourced adversaries like Lazarus.
Impact
- Lateral Movement
- Unauthorized Access
- Sensitive Data Exfiltration
Indicators of Compromise
URL
- https://thek-portal.com/eng/career/index.asp
- https://builsf.com/inc/left.php
- https://www.rsdf.kr/wp-content/uploads/2024/01/index.php
- http://www.shcpump.com/admin/form/skin/formBasic/style.php
- https://kadsm.org/skin/board/basic/write_comment_skin.php
- http://bluekostec.com/eng/community/write.asp
- https://www.smartmanagerex.com/
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Apply all available security patches, especially for third-party tools like Innorix Agent and Cross EX.
- Conduct regular vulnerability scans to identify and mitigate system weaknesses.
- Review and limit the use of third-party browser-integrated software, particularly region-specific tools.
- Implement application control and whitelisting to restrict execution to verified applications only.
- Use network segmentation to isolate critical systems and prevent lateral movement in the event of a breach.
- Deploy endpoint detection and response (EDR) solutions for real-time threat monitoring and response.
- Integrate threat intelligence feeds to stay updated on current tactics, techniques, and procedures (TTPs).
- Utilize memory protection technologies to detect and block fileless and in-memory threats.
- Monitor processes and system behavior for anomalies, especially trusted ones like SyncHost.exe.
- Provide regular cybersecurity awareness training to staff to reduce risk from phishing and social engineering.

