Severity
High
Analysis Summary
The industrial remote access tool Ewon Cosy+ has security flaws that have been made public. These vulnerabilities could be leveraged to escalate an attacker's privileges to root the device and launch subsequent attacks.
Elevated access may then be used as a weapon to obtain properly signed X.509 VPN certificates for foreign devices, allowing them to take control of their VPN sessions, as well as to decrypt encrypted firmware files and encrypted data, including passwords in configuration files. This makes it possible for threat actors to take over VPN connections, posing serious security threats to Cosy+ users as well as the nearby industrial equipment.
Over the weekend, the discoveries were disclosed at the DEF CON 32 conference. As part of an alert released by Ewon on July 29, 2024, the flaws have been fixed in firmware versions 21.2s10 and 22.1s3 following responsible disclosure. These vulnerabilities include:
- CVE-2024-33892: Information disclosure via cookies.
- CVE-2024-33893: XSS when the logs are displayed because the input was not properly sanitized.
- CVE-2024-33894: Multiple processes with escalated privileges get executed.
- CVE-2024-33895: The encryption of the configuration settings using a distinct key.
- CVE-2024-33896: Code injection brought on by incorrect blacklisting of parameters.
- CVE-2024-33897: A compromised device might be used to send Talk2m a Certificate Signing Request (CSR) for a different device, which would cause a problem with availability.
The design of Ewon Cosy+ makes use of an OpenVPN-managed VPN connection that is directed to a vendor-managed platform named Talk2m. The industrial gateway can be accessed remotely by technicians via an OpenVPN-powered VPN relay. The researchers said to have found a filter bypass and an operating system command injection vulnerability that allowed an attacker to upload a specifically designed OpenVPN configuration to get a reverse shell.
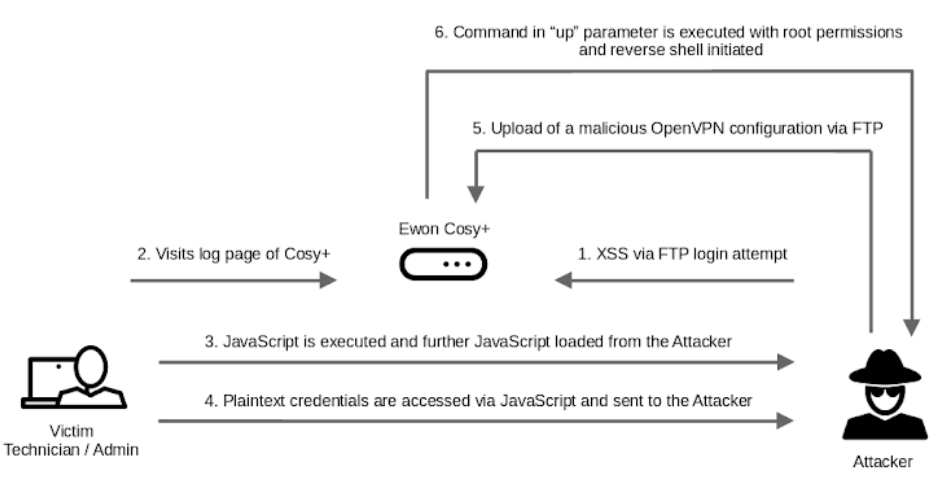
Subsequently, an attacker might have exploited a persistent cross-site scripting (XSS) vulnerability and the device's unencrypted cookie-named credentials, which store the Base64-encoded credentials of the active web session, to obtain administrator access and ultimately root it. By combining the discovered vulnerabilities and, for example, waiting for an admin user to log in to the device, an unauthenticated attacker can obtain root access to the Cosy+.
The firmware update file could then be decrypted, persistence could be established, and firmware-specific encryption keys could be accessed by expanding the attack chain. Furthermore, the secrets may be retrieved by using a hard-coded key that is kept in the binary for password encryption. Mutual TLS (mTLS) authentication secures the HTTPS connection between the Cosy+ and the Talk2m API. When a Cosy+ device is linked to a Talk2m account, it creates and submits a certificate signing request (CSR) to the Talk2m API that includes its serial number as the common name (CN).
This certificate is used for OpenVPN authentication and is accessible by the device using the Talk2m API. Nevertheless, researchers discovered that a threat actor might successfully launch a VPN session by enrolling their own CSR with a target device's serial number if they only relied on the device's serial number. The original device will no longer be accessible as the initial VPN session will be overwritten. Talk2m users will be routed to the attacker if they connect to the device with the VPN client program Ecatcher.
This allows attackers to launch additional attacks against the target client, such as gaining access to the victim client's RDP or SMB network services. This attack is made easier by the fact that the tunnel connection is unrestricted. Since the attacker receives the network traffic, it is possible to mimic the original network and systems to intercept user input from the victim, including uploaded PLC programs or other similar files.
Impact
- Privilege Escalation
- Exposure of Sensitive Data
- Cross-Site Scripting
Indicators of Compromise
CVE
- CVE-2024-33892
- CVE-2024-33893
- CVE-2024-33894
- CVE-2024-33895
- CVE-2024-33896
- CVE-2024-33897
Remediation
- Refer to HMS Security Advisory for patch, upgrade, or suggested workaround information.
- Organizations must test their assets for the vulnerability mentioned above and apply the available security patch or mitigation steps as soon as possible.
- Implement multi-factor authentication to add an extra layer of security to login processes.
- Regularly monitor network activity for any unusual behavior, as this may indicate that a cyberattack is underway.
- Organizations must stay vigilant and follow best practices for cybersecurity to protect their systems and data from potential threats. This includes regularly updating software and implementing strong access controls and monitoring tools.
- Develop a comprehensive incident response plan to respond effectively in case of a security breach or data leakage.
- Maintain regular backups of critical data and systems to ensure data recovery in case of a security incident.
- Adhere to security best practices, including the principle of least privilege, and ensure that users and applications have only the necessary permissions.
- Establish a robust patch management process to ensure that security patches are evaluated, tested, and applied promptly.
- Conduct security audits and assessments to evaluate the overall security posture of your systems and networks.
- Implement network segmentation to contain and isolate potential threats to limit their impact on critical systems.

