Severity
High
Analysis Summary
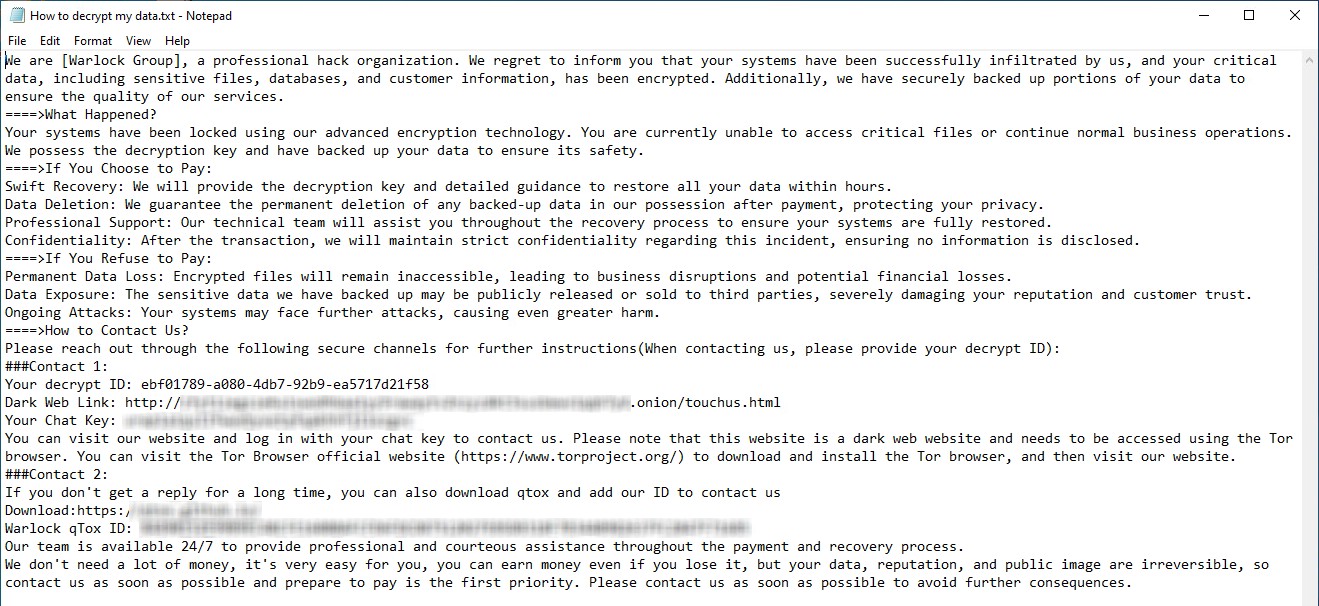
The Warlock ransomware group emerged in June 2025 on the Russian-language RAMP forum with a bold advertisement, quickly establishing itself as a notable threat actor. Operating under a ransomware-as-a-service (RaaS) model, Warlock provides affiliates with a ransomware builder, management tools, and leak sites, enabling rapid adoption and widespread attacks.
Within weeks of its debut, the group claimed multiple victims across government, financial, manufacturing, and technology sectors, with incidents spanning North America, Europe, Asia, and Africa. Affiliates such as Storm-2603, suspected to be linked to Chinese operations, have leveraged vulnerabilities like the ToolShell chain in Microsoft SharePoint servers to deliver Warlock payloads.
A common entry vector for Warlock involves exploiting unpatched, internet-facing SharePoint servers, allowing threat actors to gain remote code execution and establish persistence. Following initial compromise, attackers escalate privileges by modifying group policies, enabling guest accounts, and deploying tools such as PsExec for lateral movement. Defense evasion tactics include the use of custom executables like “Antivirus Terminator” and Trojanized binaries such as vmtools.exe designed to disable endpoint protection. In some cases, vulnerable third-party drivers like ServiceMouse.sys have been abused to facilitate process termination.
The attack lifecycle typically involves reconnaissance, credential theft via tools such as Mimikatz, and system discovery commands. Lateral movement is achieved through SMB shares, remote desktop manipulation, and administrative shares, while persistence is maintained using renamed binaries and tunneling via Cloudflare tools. Data exfiltration often relies on legitimate software disguised as benign executables, such as RClone masquerading as TrendSecurity.exe, configured to transfer large volumes of sensitive data to attacker-controlled cloud storage.
The final stage of attacks deploys the Warlock ransomware binary, which is linked to the AK47 project. The malware incorporates safety checks, process termination routines, and selective targeting, excluding certain files, directories, and extensions. Encrypted files are appended with the .x2anylock extension, and ransom notes are dropped in plaintext.
Analysis indicates that Warlock is a customized variant of LockBit 3.0, leveraging leaked builders to create a new strain. Its rapid evolution, global reach, and sophisticated toolset demonstrate how quickly modern ransomware groups adapt enterprise vulnerabilities into impactful extortion campaigns.
Impact
- Privilege Escalation
- Credential Theft
- Lateral Movement
- File Encryption
- Financial Loss
Indicators of Compromise
MD5
bf9f0c82c2ee89c7bc5480adc5e9494e
2c01e4b57b4d7e01e755dc2dca53d9b8
363dfaa9fc77ae1f899049428a86d17e
23ee7c55dc6308099d90d0ad6d9f1709
1b5e6b1f7c46aaaaaecc49352e0e41eb
SHA-256
- bba75dc056ef7f9c4ade39b32174c5980233fc1551c41aca9487019191764bac
- a919844f8f5e6655fd465be0cc0223946807dd324fcfe4ee93e9f0e6d607061e
- f711b14efb7792033b7ac954ebcfaec8141eb0abafef9c17e769ff96e8fecdf3
- aca888bbb300f75d69dd56bc22f87d0ed4e0f6b8ed5421ef26fc3523980b64ad
- d1f9ace720d863fd174753e89b9e889d2e2f71a287fde66158bb2b5752307474
SHA1
0488509b4dbc16dcb6d5f531e3c8b9a59b69e522
22a7cd4bc7c5920d2e82a8ec7b79b64fd6335f72
b9c60c84be9bb503333e82f2e0b4024ce0d500c4
a5fa4b82f9fdad3f807d84f855f111aca600f1e2
1b14acdc80b4ea8e734d40f85a6d1b8765fc1b15
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Apply security patches promptly, especially for internet-facing applications like SharePoint.
- Restrict RDP and administrative shares to limit lateral movement opportunities.
- Enable multi-factor authentication on privileged accounts to reduce unauthorized access.
- Deploy advanced EDR solutions to detect process termination and malicious executables.
- Monitor network traffic for unusual data transfers that may indicate exfiltration.
- Use application whitelisting to prevent execution of unauthorized binaries.
- Regularly back up data offline and test recovery procedures to minimize downtime.
- Conduct threat hunting for tools like PsExec, Mimikatz, and RClone in the environment.
- Segment critical infrastructure to contain the spread of ransomware.
- Train employees to recognize phishing and suspicious login attempts.

