Severity
High
Analysis Summary
A new ransomware-as-a-service (RaaS) operation called VanHelsing has appeared, targeting Windows, Linux, BSD, ARM, and ESXi systems. It was first advertised on cybercrime forums on March 7, allowing experienced hackers to join for free while requiring a $5,000 deposit from less experienced ones.
Researchers have analyzed VanHelsing, identifying it as a Russian-based operation that avoids attacking CIS (Commonwealth of Independent States) countries. Affiliates keep 80% of ransom payments, while operators take a 20% cut, with payments processed through an automated escrow system using blockchain confirmations.
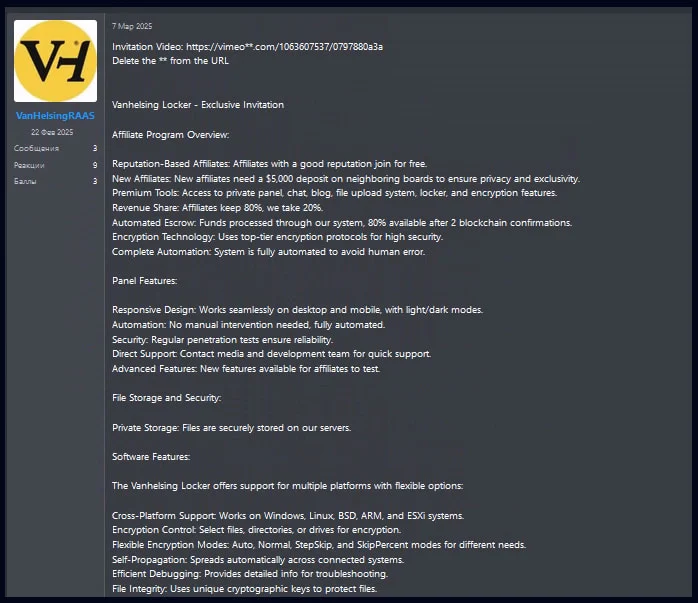
Approved affiliates get access to an automated panel and support from the developers. The stolen data is stored on VanHelsing’s servers, and the team claims to conduct penetration tests to maintain security.
The ransomware's dark web extortion portal currently lists three victims: a city in Texas and two technology companies, one in the U.S. and another in France. The attackers threaten to leak stolen files if a ransom is not paid.
VanHelsing is written in C++ and was first deployed on March 16. It uses the ChaCha20 algorithm for encryption, generating unique keys for each file and encrypting them with an embedded Curve25519 public key. Larger files over 1GB are only partially encrypted, while smaller files are fully encrypted.
In stealth mode, encryption happens first, and renaming occurs later, making detection harder. Even if security tools detect the renaming process, the files will already be encrypted.
Despite its advanced techniques, VanHelsing has some flaws, including inconsistencies in file extensions, errors in exclusion logic, and unimplemented command-line options. However, it remains a growing threat that could gain traction quickly.
Impact
- Unauthorized Access
- Financial Loss
- Data Theft
Indicators of Compromise
MD5
5c254d25751269892b6f02d6c6384aef
3e063dc0de937df5841cb9c2ff3e4651
SHA-256
86d812544f8e250f1b52a4372aaab87565928d364471d115d669a8cc7ec50e17
99959c5141f62d4fbb60efdc05260b6e956651963d29c36845f435815062fd98
SHA1
79106dd259ba5343202c2f669a0a61b10adfadff
e683bfaeb1a695ff9ef1759cf1944fa3bb3b6948
Remediation
- Regularly update and patch operating systems and software to fix security vulnerabilities.
- Implement strong access controls and limit user privileges to reduce the risk of unauthorized execution.
- Use endpoint protection solutions with real-time malware detection and behavioral analysis.
- Enable network segmentation to prevent the spread of ransomware across systems.
- Regularly back up important data and store backups offline or in a secure cloud environment.
- Monitor network traffic for unusual activities and restrict access to remote management tools.
- Disable unnecessary services and ports to minimize attack entry points.
- Implement multi-factor authentication (MFA) for accessing critical systems and accounts.
- Use email filtering solutions to block malicious attachments and links.
- Keep antivirus and firewall protections updated and properly configured.
- Establish an incident response plan to quickly contain and mitigate ransomware attacks.
- Regularly test security defenses through vulnerability assessments and penetration testing.
- Block known malicious IP addresses and domains associated with ransomware operations.

