Severity
High
Analysis Summary
Over 390,000 WordPress credentials have been stolen by a threat actor known as MUT-1244 in a massive, year-long campaign that used a trojanized WordPress credentials checker to target other threat actors.
SSH private keys and AWS access keys were also taken from the hacked systems of hundreds of other victims, who are thought to include malicious actors, penetration testers, security researchers, and red teamers, according to the researchers who discovered the attacks. The same second-stage payload, which was distributed through dozens of trojanized GitHub repositories and contained malicious proof-of-concept (PoC) exploits targeting known security flaws, as well as a phishing campaign that tricked targets into installing a phony kernel upgrade disguised as a CPU microcode update, were used to infect the victims.
The phony repositories fooled threat actors and security experts looking for exploit code for certain vulnerabilities, while the phishing emails deceived victims into running commands that installed the malware. Threat actors have previously targeted researchers with phony proof-of-concept attacks to obtain access to cybersecurity company networks or steal important research. Because of their names, several of these repositories are automatically listed as proof-of-concept repositories for these vulnerabilities in reputable sources like Vulnmon or Feedly Threat Intelligence. This gives them a more legitimate appearance and makes it more likely that someone will run them.
Multiple techniques, such as backdoored configure compilation files, malicious PDF files, Python droppers, and malicious npm packages contained in the projects' dependencies, were used to deploy the payloads via GitHub repos. This campaign is similar to one described in a November report about a year-long supply-chain attack where malicious code in the "0xengine/xmlrpc" npm package was used to trojanize the "hpc20235/yawp" GitHub project to mine Monero cryptocurrency and steal data.
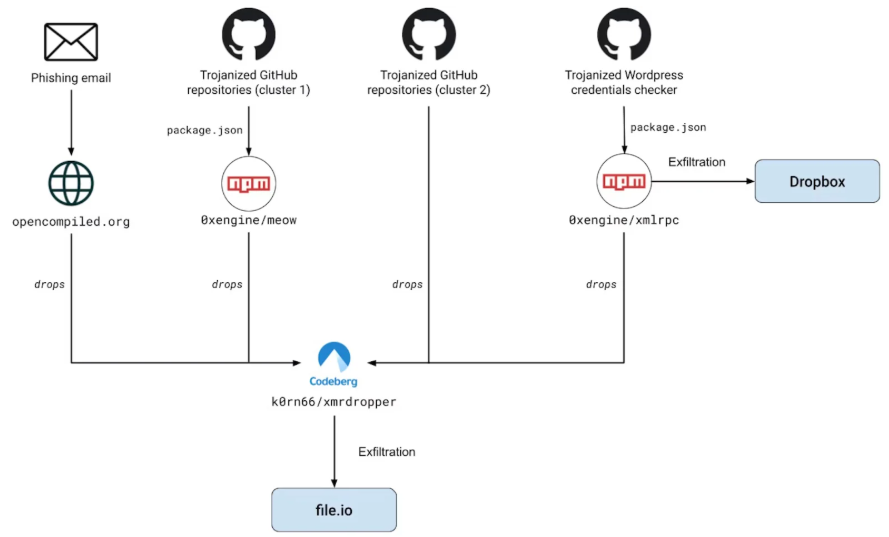
The malware used in these attacks contains a backdoor and a cryptocurrency miner that enabled MUT-1244 to gather and steal environment variables, private SSH keys, AWS passwords, and important directory contents like "~/.aws." The investigators discovered that the second-stage payload, which was housed on a different site, had hardcoded login credentials for file-sharing services like Dropbox and file.io, which made it simple for the attackers to retrieve the stolen material.
More than 390,000 credentials, thought to be WordPress ones, were accessible to MUT-1244. Researchers conclude with high confidence that offensive actors, who most likely obtained them illegally, held these credentials before their exfiltration to Dropbox. The Yawpp tool they used to verify the legitimacy of these credentials was subsequently utilized to hack these actors. It's hardly surprising that an attacker with a set of stolen credentials—which are frequently bought from underground markets to expedite threat actor operations—would use Yawpp to validate them, given that MUT-1244 promoted it as a "credentials checker" for WordPress.
After the targets unintentionally ran the threat actor's malware, the attackers were able to take advantage of the trust in the cybersecurity community to compromise dozens of computers owned by both white hat and black hat hackers. This resulted in the theft of data, including command histories, SSH keys, and AWS access tokens. According to cybersecurity experts, this continuous attack is still compromising hundreds of systems and infecting others.
Impact
- Credential Theft
- Unauthorized Access
- Command Execution
- Cryptocurrency Theft
Indicators of Compromise
IP
- 94.156.177.14
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Enable antivirus and anti-malware software and update signature definitions promptly. Using multi-layered protection is necessary to secure vulnerable assets.
- Patch and upgrade any platforms and software on time and make it into a standard security policy.
- Employ network intrusion detection and prevention systems to monitor and block malicious network activities.
- Implement network segmentation to limit lateral movement for attackers within the network.
- Implement advanced email filtering to detect and block phishing emails.
- Employ updated and robust endpoint protection solutions to detect and block malware.
- Develop and test an incident response plan to ensure a swift and effective response to security incidents.
- Enhance logging and monitoring capabilities to detect anomalous activities and unauthorized access.
- Conduct regular security audits and penetration testing to identify and address potential vulnerabilities.
- Regularly back up critical data and ensure that backup and recovery procedures are in place.
- Do not download documents attached in emails from unknown sources and strictly refrain from enabling macros when the source isn’t reliable.

