Severity
High
Analysis Summary
A threat actor has claimed responsibility for a data breach targeting American Income Life (AIL), a major U.S.-based provider of life, accident, and supplemental health insurance. The actor is reportedly offering a stolen database for sale on a well-known cybercrime forum, raising concerns about the potential exposure of sensitive client data.
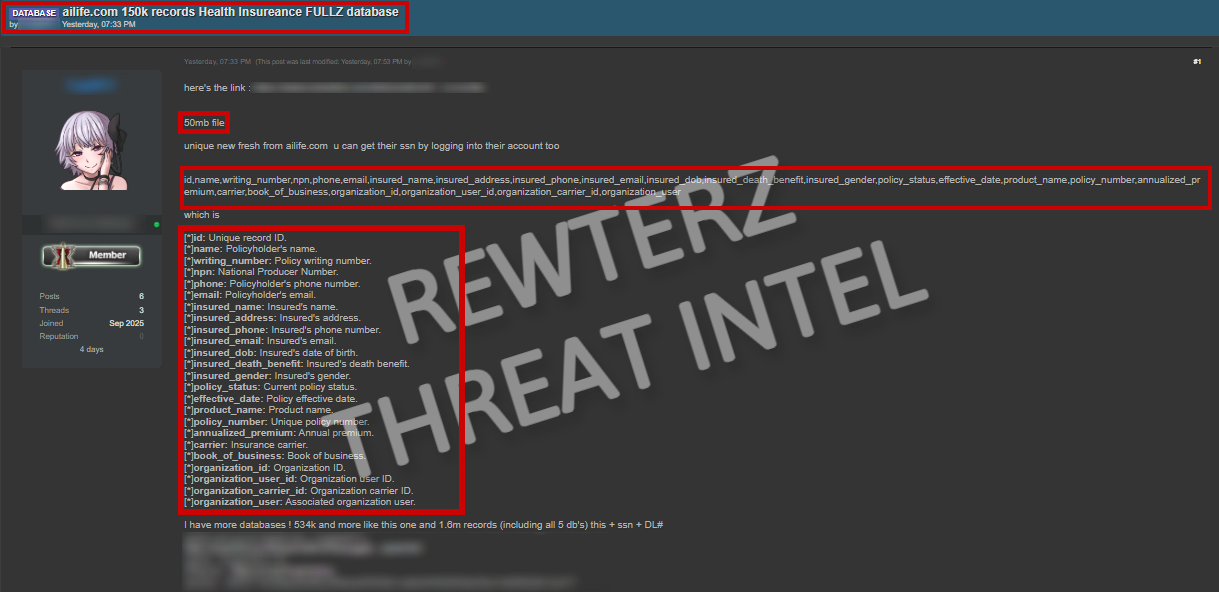
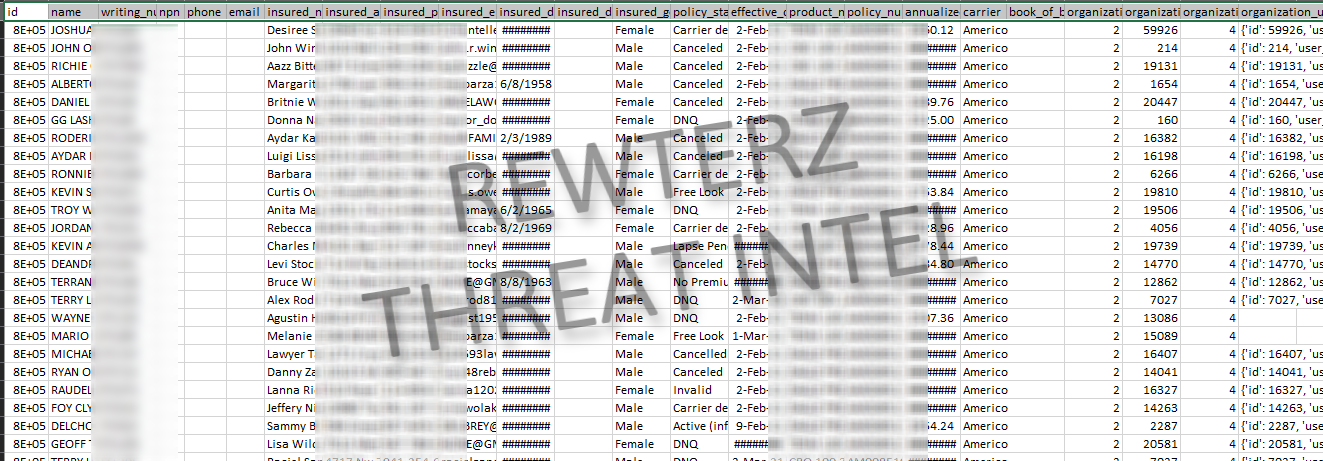
According to the claims, the exfiltrated database contains approximately 150,000 records belonging to policyholders. The compromised dataset allegedly includes personally identifiable information (PII) and policy details, such as full names, policy writing numbers, phone numbers, email addresses, physical addresses, and dates of birth. In addition, the database reportedly holds highly sensitive financial and insurance-related data, including death benefits, gender, policy status, effective dates, premium amounts, and carrier information.
If validated, this breach could have significant consequences for both AIL and its customers, as the data could be leveraged for identity theft, financial fraud, or social engineering attacks. The sale of such information on underground markets further increases the risk of widespread misuse by malicious actors.
As of now, AIL has not issued an official statement confirming or denying the breach. Security experts emphasize the need for vigilance, monitoring, and timely incident response to mitigate potential damage.
Impact
- Sensitive Information Theft
- Reputational Damage
Remediation
- Implement robust multi-layered security measures to detect and respond to ransomware activities.
- Conduct regular security assessments and penetration testing to identify and mitigate vulnerabilities in critical infrastructure and government systems.
- Deploy advanced threat detection tools, such as Endpoint Detection and Response (EDR) and Network Traffic Analysis (NTA), to monitor for suspicious activities and anomalies.
- Ensure timely patching and updating of all software and systems to close known security gaps.
- Use multi-factor authentication (MFA) and strong password policies to protect user accounts from unauthorized access.
- Segment networks to limit lateral movement within the organization in case of a breach.
- Develop and maintain an incident response plan that includes procedures for ransomware attacks and data breaches.
- Train employees on cybersecurity best practices and phishing awareness to reduce the risk of social engineering attacks.
- Regularly back up critical data and ensure backups are stored securely and are not accessible from the primary network.
- Implement encryption for sensitive data at rest and in transit to protect against data theft.
- Limit access to critical systems and data to only those individuals who require it for their role.
- Monitor for and immediately investigate the presence of known ransomware and indicators of compromise associated with ransomware groups.
- Ensure legal and compliance measures are in place, particularly for industries subject to specific regulatory requirements.

