Severity
High
Analysis Summary
A threat actor known as Zeroplayer has reportedly advertised a dangerous zero-day remote code execution (RCE) exploit paired with a sandbox escape affecting Microsoft Office and Windows systems. Listed for $30,000 on a prominent Russian hacking forum, the exploit is said to work on most modern Office file formats and even on fully patched Windows installations. This claim has raised major concern in the cybersecurity community, as a sandbox escape significantly amplifies the impact of any Office-based attack.
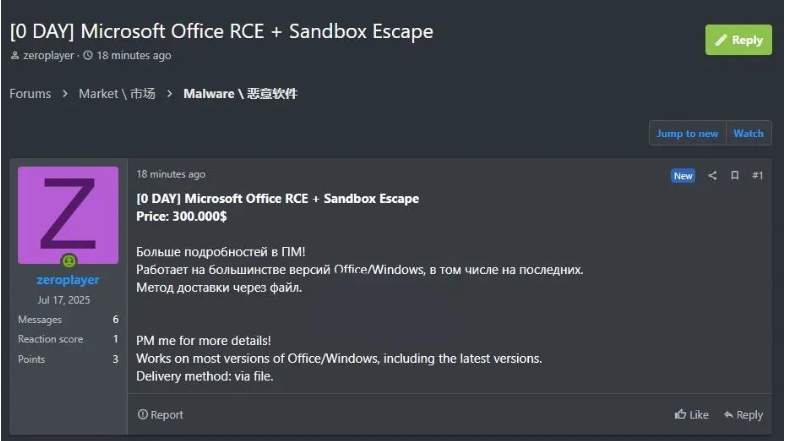
According to the listing, the exploit allows attackers to deliver malicious payloads through common Office documents such as Word and Excel, delivered via phishing campaigns or compromised websites. Zeroplayer asserts that the vulnerability enables escape from Microsoft Office’s sandbox a key security barrier designed to isolate untrusted code and ultimately results in full system compromise. The seller is offering private demonstrations and stresses that the exploit is compatible with recent security updates, reducing the chance of detection by antivirus tools.
Zeroplayer is not new to the underground exploit market, having previously sold a WinRAR zero-day RCE for $80,000 in July 2025, indicating a trend of targeting widely used software. While Microsoft addressed several RCE vulnerabilities in its November 2025 Patch Tuesday, including CVE-2025-62199, none of these patches reference this alleged 0-day. This increases fears that the exploit remains unpatched, especially dangerous due to the inclusion of a sandbox escape. Sandbox bypasses effectively neutralize one of Office's strongest defenses against macro-based and document-embedded malware.
Experts warn that Russian-language cybercrime forums often host state-linked and high-tier threat actors, making this exploit a potential tool for ransomware operators, espionage groups, or supply-chain attackers. Historical parallels, such as the exploitation of CVE-2023-36884 by Storm-0978, underscore how Office-based RCE vulnerabilities have been weaponized for targeted intrusions. With Office deployed on over 1.4 billion devices, widespread exploitation could have global impact. Organizations are strongly urged to enforce macro restrictions, enable Protected View, monitor suspicious documents and forum activity, and be prepared to apply emergency patches if Microsoft confirms the flaw.
Impact
- Remote Code Execution
- Gain Access
Indicators of Compromise
CVE
CVE-2023-36884
CVE-2025-62199
Remediation
- Disable all Office macros by default and enforce strict macro security policies across the organization.
- Enable Protected View for all documents originating from email, internet downloads, or network locations.
- Block Office applications from creating child processes using Attack Surface Reduction (ASR) rules.
- Deploy advanced endpoint protection (EDR/XDR) capable of detecting suspicious Office document behavior.
- Implement email filtering to block or quarantine suspicious attachments, especially Word/Excel files.
- Train employees to identify phishing emails and avoid opening unsolicited Office documents.
- Restrict the execution of Office files from temporary and user-writable folders.
- Monitor for emerging indicators of compromise (IOCs) and threat actor activity on underground forums.
- Apply Microsoft security patches immediately when released, especially emergency or out-of-band updates.
- Use application whitelisting or Microsoft Defender Application Control (MDAC) to limit unauthorized code execution.
- Enforce strong network segmentation to limit lateral movement if an exploit is executed.
- Regularly back up critical systems and verify restore readiness in case of compromise.


