Severity
High
Analysis Summary
The massive American telecom provider T-Mobile has acknowledged that it was one of the companies targeted by Chinese threat actors to obtain sensitive data.
The attackers, known as Salt Typhoon, broke into the business as part of a months-long campaign to intercept high-value intelligence targets' cellphone conversations. It's unclear what data, if any, were stolen during the nefarious activity. T-Mobile is keeping a careful eye on this industry-wide attack, and as of right now, there has been no discernible impact on T-Mobile systems or data, nor is there any indication that customer information has been harmed.
“We will continue to monitor this closely, working with industry peers and the relevant authorities,” said a spokesperson for the company.
With the most recent development, T-Mobile has joined several prominent companies that have been singled out as part of what seems to be a full-fledged cyber espionage campaign, including AT&T, Verizon, and Lumen Technologies. The reports do not yet specify the types of information that were targeted, whether malware was implanted, or the extent to which these attempts were successful. It has previously been revealed that Salt Typhoon gained illegal access to Americans' cellular data.
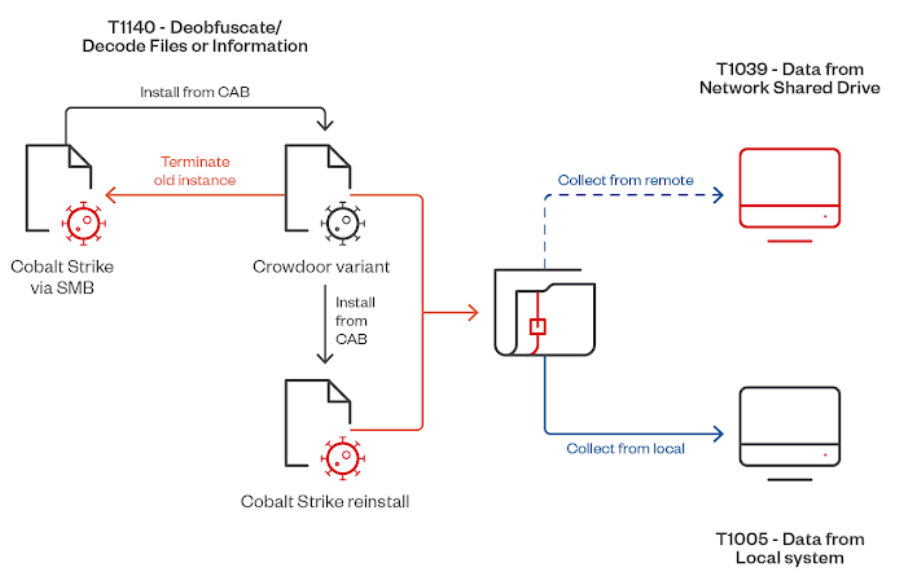
The People’s Republic of China (PRC) was responsible for a large-scale attack, according to the U.S. government’s ongoing investigation into the targeting of commercial telecommunications infrastructure last week. The theft of customer call records, the compromise of private communications of a small number of people primarily involved in government or political activity, and the copying of specific information that was subject to U.S. law enforcement requests in response to court orders have all been made possible by PRC-affiliated actors who have compromised networks at several telecommunications companies. It further cautioned that as the investigation progresses, the breadth and depth of these compromises may increase.
Salt Typhoon—also called Earth Estries, FamousSparrow, GhostEmperor, and UNC2286—has been active since at least 2020. The espionage group was implicated in a string of attacks against government and technological establishments in the Philippines, Taiwan, Malaysia, South Africa, Germany, and the United States in August 2023. The threat actors have carefully constructed their payloads and employed an intriguing mix of reputable and custom tools and strategies to get past defenses and keep access to their targets.
The researchers saw two different attack chains used by the threat group, suggesting that Salt Typhoon's toolkit is as diverse as it is wide. Vulnerabilities in remote management tools or services visible to the outside world be exploited to get initial access to target networks. Programs like PortScan for network mapping and discovery and NinjaCopy for credentials extraction are also used in the attacks. Scheduled tasks are the way by which the host is sustained.
In one instance, Salt Typhoon is also thought to have tried to hide the malicious traffic by using a victim's proxy server to redirect traffic to the real command-and-control (C2) server. FuxosDoor, an Internet Information Services (IIS) implant installed on a compromised Exchange Server that is also made to run commands using cmd.exe, and Cryptmerlin, which carries out additional commands sent by a C2 server, were two more backdoors found on one of the compromised computers.
Impact
- Sensitive Data Theft
- Unauthorized Access
- Cyber Espionage
Remediation
- Conduct regular, comprehensive cybersecurity training programs for employees, focusing on spear-phishing recognition and avoidance. Simulate phishing attacks to test awareness and response.
- Enforce multi-factor authentication (MFA) for all critical systems, including email, source code repositories, and proprietary software, to reduce the risk of unauthorized access.
- Apply the principle of least privilege, ensuring that only authorized personnel have access to sensitive software and source code. Regularly review and audit access control policies.
- Use advanced email filtering systems that detect and block phishing attempts, especially those involving domain spoofing and impersonation tactics.
- Employ continuous network monitoring tools to detect unauthorized access or unusual activity. Regularly audit system logs for any indicators of compromise (IOCs) or anomalous behavior.
- Deploy EDR solutions to detect and respond to malicious activity on endpoints, particularly those involving attempts to exfiltrate sensitive data.
- Ensure timely patching of software vulnerabilities in operating systems, email servers, and security tools to reduce the risk of exploitation by cybercriminals.
- Establish protocols for quickly reporting cyber incidents to relevant authorities, like the FBI or other national agencies, to assist with tracking and mitigating cybercriminal activities.
- Perform periodic penetration testing and vulnerability assessments to identify and address weaknesses in the security infrastructure.
- Leverage real-time threat intelligence feeds to stay informed about new phishing campaigns and tactics targeting industries like aerospace and defense.

