Severity
High
Analysis Summary
Researchers has identified a stealthy spear-phishing campaign targeting finance executives across Europe, Africa, the Middle East, Canada, and South Asia. The attackers pose as recruiters from Rothschild & Co, offering fake career opportunities to lure victims into downloading and executing malware. The campaign uses Firebase-hosted phishing pages, JavaScript-based custom CAPTCHAs, and staged VBS scripts to evade detection by traditional email and web security tools.
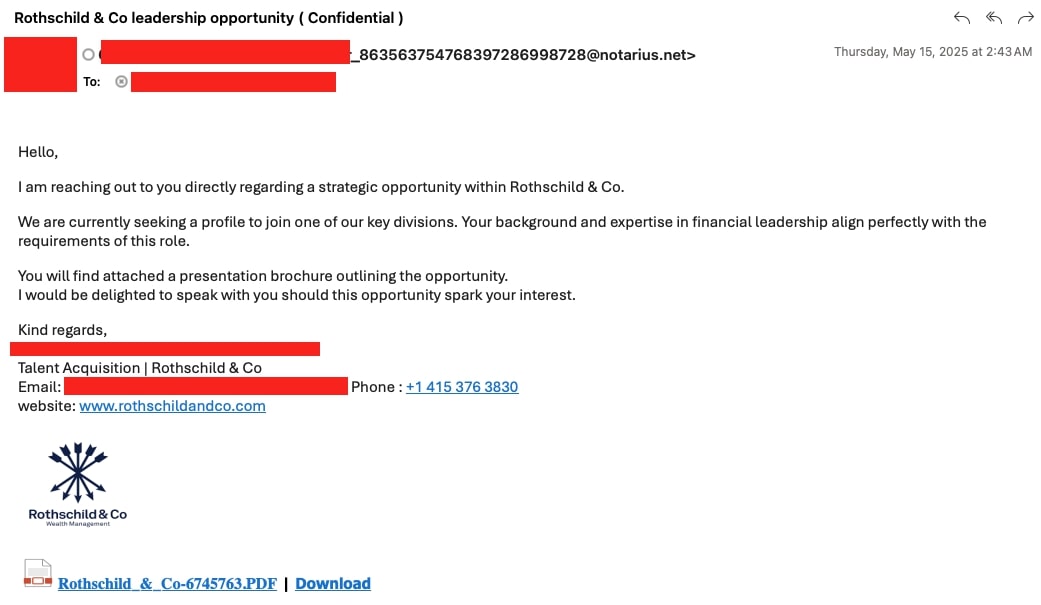
The phishing email contains a link disguised as a PDF brochure, but it actually leads to a Firebase-hosted page protected by a math-based CAPTCHA. Solving the CAPTCHA redirects the user to a site delivering a ZIP archive named Rothschild_&_Co-6745763.zip, which contains a malicious VBS script. When executed, this script downloads a secondary payload that installs legitimate tools like NetBird (a WireGuard-based remote access tool) and OpenSSH.
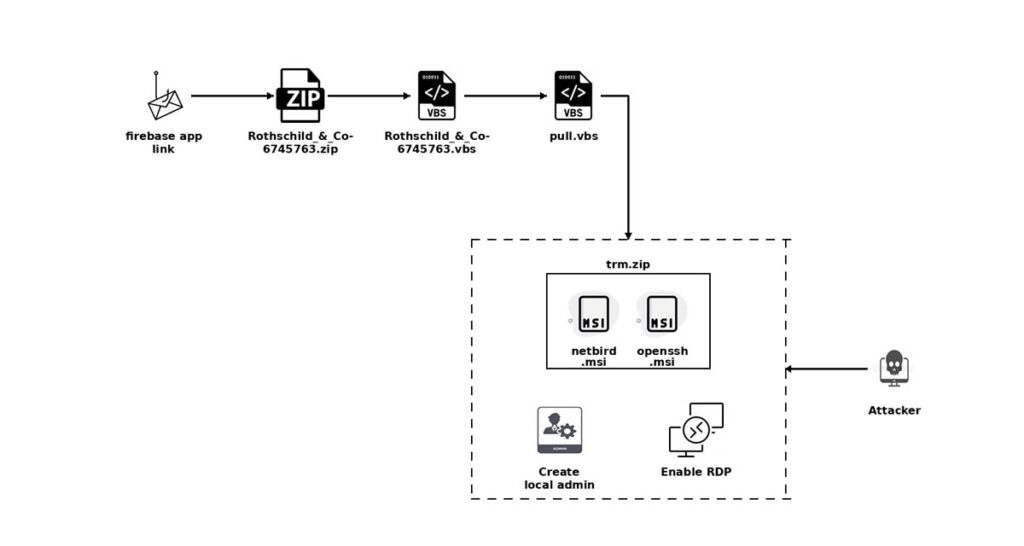
The script further establishes persistence by creating a hidden local admin account (user: user, password: Bs@202122), enabling Remote Desktop Protocol (RDP), modifying firewall rules, setting NetBird to auto-start, and deleting desktop shortcuts to avoid user detection. This setup grants the attackers encrypted remote access and a foothold for potential lateral movement or data theft.
The use of Firebase and other Google-hosted platforms makes the phishing pages appear legitimate, while the custom CAPTCHAs decrypt hidden redirect URLs only after user interaction, helping the campaign bypass automated defenses. Researchers warns that this method is becoming increasingly common in advanced phishing operations.
Researchers also found overlapping infrastructure with earlier campaigns, including an old phishing page impersonating SharePoint that still delivers the same VBS payload. These findings suggest the attackers are reusing toolkits and infrastructure for broader operations. While no specific attribution has been made, some tactics resemble those seen in nation-state campaigns. This urges organizations to monitor for suspicious web hosting behavior and block execution of VBS and MSI files.
Impact
- Unauthorized Access
- Lateral Movement
- Data Exfiltration
Indicators of Compromise
IP
- 192.3.95.152
MD5
53192b6ba65a6abd44f167b3a8d0e52d
b91162a019934b9cb3c084770ac03efe
SHA-256
f04b4532952bd0dd5a6a47ed8710f89519cdf8f0b8392d560e359bb466ccab38
d34b190baccd02b6b61e349f2cad4bfed5c0c38855ac70ec4063294dbed9c939
SHA1
d54ea13f7586a7a3d5cfdbdeef5377497d2d5f74
19a2939e4747fa90db4fb24c1cec28ba21525779
URL
- https://googl-6c11f.firebaseapp.com/job/file-846873865383.html
- https://googl-6c11f.web.app/job/9867648797586_Scan_15052025-736574.html
- http://192.3.95.152/cloudshare/atr/pull.pdf
- http://192.3.95.152/cloudshare/atr/trm
Remediation
- Block execution of VBS and MSI files from email and web downloads.
- Monitor and restrict use of remote access tools like NetBird and OpenSSH.
- Implement application allow listing to prevent unauthorized script execution.
- Enforce multi-factor authentication on all sensitive accounts.
- Disable or tightly control RDP access across endpoints.
- Inspect and block suspicious outbound connections to Firebase and similar platforms.
- Use endpoint detection and response (EDR) to monitor for lateral movement behavior.
- Educate staff on identifying spear-phishing and deceptive job lures.
- Implement email security filters to block spoofed recruiter messages.
- Monitor for unauthorized account creation and privilege escalation.
- Regularly audit firewall and remote access configuration changes.
- Keep antivirus and endpoint protection signatures updated.
- Investigate signs of persistence mechanisms such as autoruns and hidden admin accounts.
- Log and alert on abnormal use of administrative tools and scripts.
- Conduct phishing simulations to reinforce user awareness and reporting.

