Severity
High
Analysis Summary
The SideWinder APT group has launched a new cyber-espionage campaign targeting government institutions across South Asia, with confirmed attacks on agencies in Sri Lanka, Bangladesh, and Pakistan. According to a report, the campaign begins with phishing emails carrying malicious documents that activate only when opened within specific geographic regions. In all other cases, the document appears blank, showcasing the attackers' use of geo-fencing to limit detection and focus on intended victims.
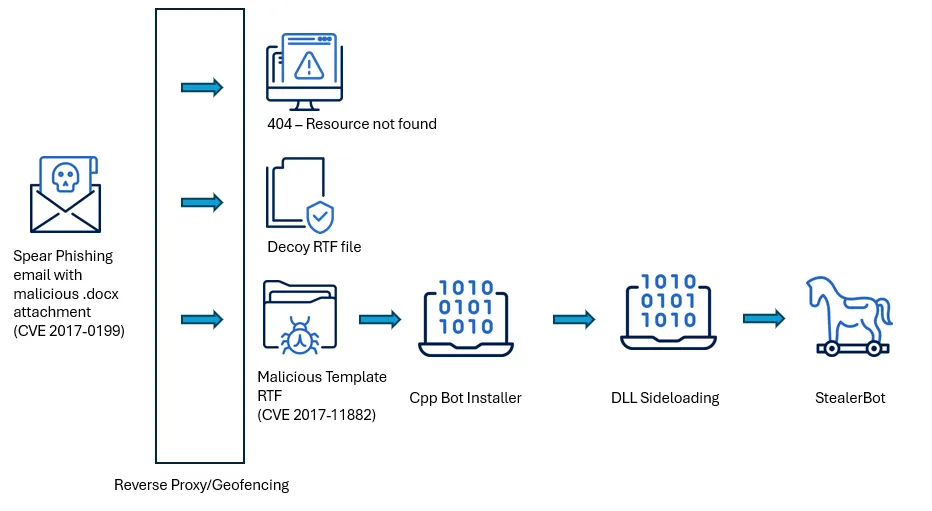
The malicious documents exploit two long-known but frequently unpatched Microsoft Office vulnerabilities—CVE-2017-0199 and CVE-2017-11882. When triggered, these exploits download and execute StealerBot, a custom .NET-based malware designed for espionage. This malware captures screenshots, keystrokes, stored passwords, and files, and also provides attackers with remote shell access. The malware uses DLL hijacking for delivery, a technique that helps bypass standard security detection methods and gain persistent access.
Targets of this campaign include high-value government sectors such as ministries of defense and finance, central banks, and telecommunications regulators. The campaign’s use of tightly constrained execution conditions and geographic filters highlights a deliberate, focused approach aimed at maximizing intelligence collection while minimizing exposure.
SideWinder’s operational continuity has been previously observed by various cybersecurity firms, which have documented the group’s consistent use of similar tactics and tools. The campaign’s effectiveness, despite relying on outdated exploits, emphasizes a persistent gap in cybersecurity hygiene among targeted organizations. Many institutions remain vulnerable due to unpatched systems and slow adoption of critical updates.
Overall, this campaign underscores SideWinder’s ongoing capability and intent to conduct focused espionage operations in the region, exploiting technical and organizational weaknesses with precision and persistence.
Impact
- Information Theft
- Cyber Espionage
- Security Bypass
Remediation
- Apply the latest security patches for Microsoft Office, specifically addressing CVE-2017-0199 and CVE-2017-11882.
- Implement application whitelisting to prevent unauthorized execution of downloaded files.
- Disable macros and embedded scripts in Office documents by default, especially from untrusted sources.
- Use advanced endpoint detection and response (EDR) tools to monitor and flag DLL hijacking behavior.
- Configure geolocation-aware security alerts to detect suspicious access patterns or region-specific attacks.
- Search for indicators of compromise (IOCs) using your organization's security controls, such as SIEM and EDR tools.
- Do not download email attachments or enable macros unless the source is verified and trusted.
- Reinforce cybersecurity awareness among all staff, focusing on email hygiene, link scrutiny, and prompt application of updates.
- Harden networks, systems, and codebases using secure development practices and vulnerability scanning tools.
- Enable two-factor or multi-factor authentication (MFA) across all critical systems and user accounts.
- Deploy and maintain updated antivirus and anti-malware solutions with regularly refreshed signature definitions.
- Enforce strict access management policies and implement the principle of least privilege across the organization.
- Maintain regularly updated and tested backups to ensure fast recovery in case of a data breach or ransomware attack.
- Keep all operating systems, software, and applications up to date with the latest security patches.
- Establish and routinely test a comprehensive incident response plan with clearly defined roles for all stakeholders.
- Monitor network activity continuously to detect and respond to suspicious behavior in real time.
- Share threat intelligence and collaborate with national and international cybersecurity bodies to stay ahead of evolving threats.
- Promote public cybersecurity awareness, especially during high-profile national events, encouraging citizens to adopt safe digital practices.

