Severity
High
Analysis Summary
Threat actors can use a recently discovered vulnerability in the open-source Common Unix Printing technology (CUPS) printing technology to execute 600x amplification factor distributed denial-of-service (DDoS) attacks.
A CVE-2024-47176 vulnerability in the cups-browsed daemon can also be used to magnify DDoS attacks, as discovered by security researchers. This flaw can be linked with three other bugs to obtain remote code execution on Unix-like computers via a single UDP packet. By sending a specially constructed packet that fools a CUPS server into thinking a target is a printer that needs to be added, an attacker can exploit this issue.
Sending a packet to a susceptible CUPS server causes it to send a bigger IPP/HTTP request to the intended device. This uses up the bandwidth and CPU resources of the CUPS server as well as the target. A threat actor just has to send one packet to a vulnerable and exposed CUPS service that is accessible online to start such an assault. Out of the more than 198,000 devices that are exposed, experts believe that about 58,000 servers might be used in DDoS attacks.
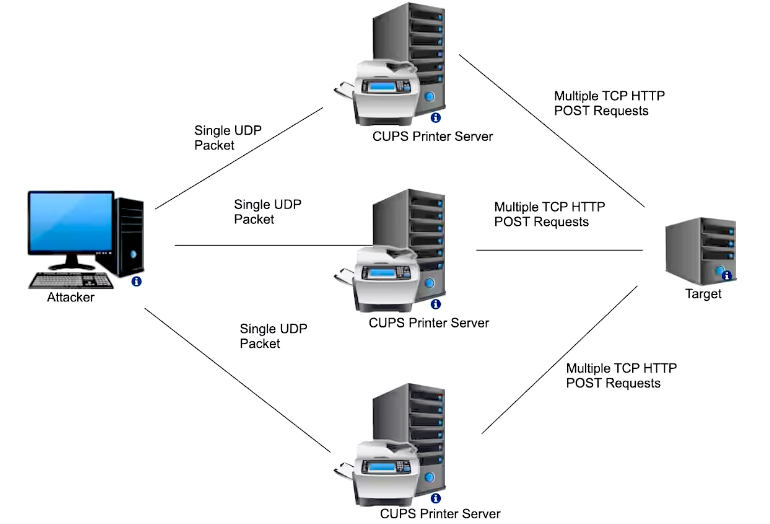
Additionally, an unlimited cycle of requests was displayed by hundreds of vulnerable devices; certain CUPS servers would send requests again after receiving the initial probe, and other servers would start an endless loop in response to particular HTTP/404 errors. Many of these susceptible computers were running out-of-date versions of CUPS (dating back to 2007), making them easy pickings for threat actors who can use them to amplify DDoS attacks or create botnets via the RCE chain.
In the worst-case situation, researchers saw that a single probe resulted in what seemed to be an infinite stream of attempted connections and requests. These seemingly endless flows won't stop unless the daemon is destroyed or restarted. Thousands of requests were made by several of these systems that we saw during testing and sent to our testing infrastructure. This conduct seemed to go on forever in certain situations.
It takes very little time and resources to carry out this DDoS amplification attack. A threat actor may quickly take over all publicly accessible CUPS services on the internet. Administrators can lessen the likelihood that their systems will be added to a botnet or used in DDoS attacks by applying the CVE-2024-47176 patches or turning off the cups-browsed service.
DDoS attacks are still effective at harassing and upsetting targets on the internet, including small content producers, online retailers, governments, and gamers in addition to larger corporations. Even though DDoS amplification is also easily abused in this scenario, the initial analysis concentrated on the RCE, which could have a more dire consequence.
Impact
- Denial of Service
- Code Execution
Indicators of Compromise
CVE
- CVE-2024-47176
Remediation
- Refer to the cups-browsed GIT Repository for patch, upgrade, or suggested workaround information.
- Organizations must test their assets for the vulnerability mentioned above and apply the available security patch or mitigation steps as soon as possible.
- Implement multi-factor authentication to add an extra layer of security to login processes.
- Regularly monitor network activity for any unusual behavior, as this may indicate that a cyberattack is underway.
- Organizations must stay vigilant and follow best practices for cybersecurity to protect their systems and data from potential threats. This includes regularly updating software and implementing strong access controls and monitoring tools.
- Develop a comprehensive incident response plan to respond effectively in case of a security breach or data leakage.
- Maintain regular backups of critical data and systems to ensure data recovery in case of a security incident.
- Adhere to security best practices, including the principle of least privilege, and ensure that users and applications have only the necessary permissions.
- Establish a robust patch management process to ensure that security patches are evaluated, tested, and applied promptly.
- Conduct security audits and assessments to evaluate the overall security posture of your systems and networks.
- Implement network segmentation to contain and isolate potential threats to limit their impact on critical systems.

