Severity
High
Analysis Summary
Security researcher has disclosed an in-depth analysis and Proof of Concept (PoC) exploit for CVE-2024-54887, a critical buffer overflow vulnerability in TP-Link TL-WR940N routers. The flaw resides in the handling of IPv6 DNS server configuration parameters, specifically dnsserver1 and dnsserver2, within the router’s web interface. These parameters fail to validate input string lengths before copying them into memory, enabling potential remote code execution (RCE) or denial-of-service (DoS) attacks.
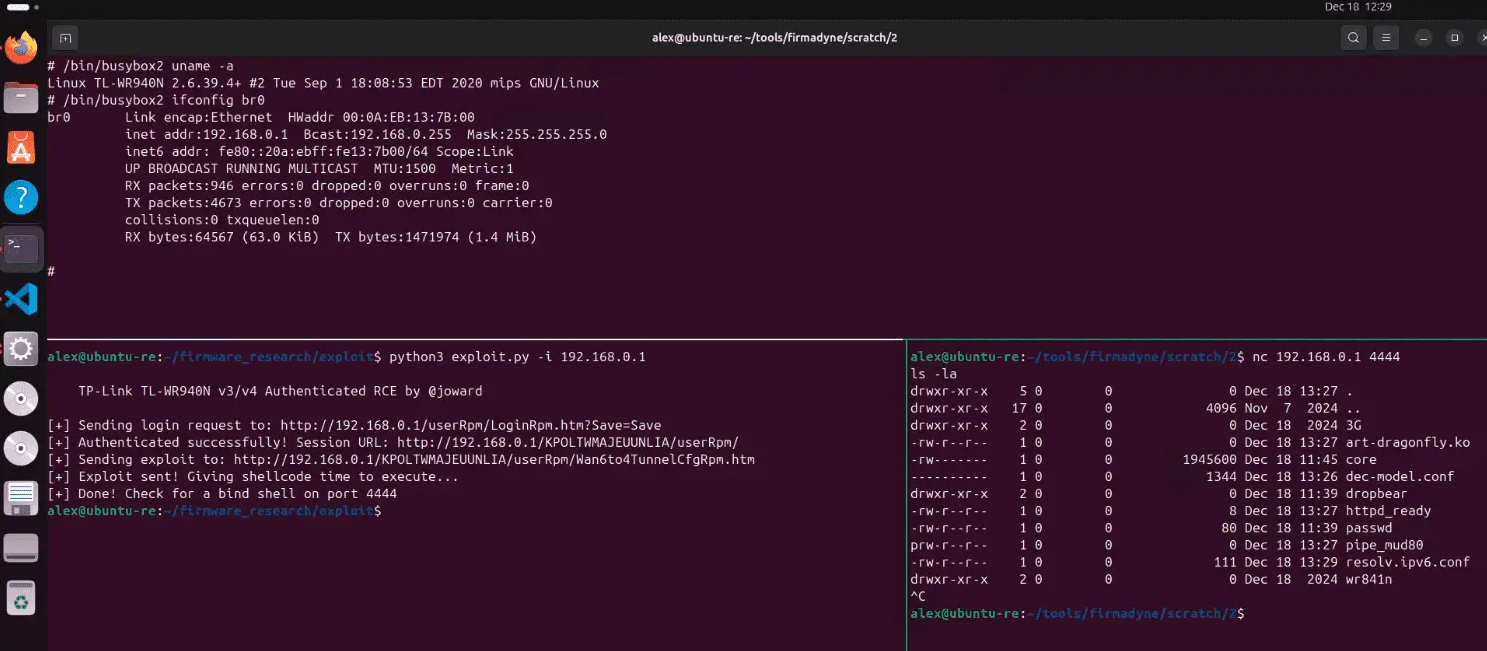
The vulnerability affects hardware versions 3 and 4 of the TL-WR940N running the latest firmware. These versions lack modern security mitigations such as NX and PIE protections, significantly easing exploitation. Researcher’s analysis, utilizing tools like Firmadyne and Ghidra, uncovered that both parameters are inadequately checked, leading to a stack buffer overflow.
The PoC exploit demonstrates a sophisticated method for achieving RCE, employing Return Oriented Programming (ROP) techniques. Researcher highlights unique challenges in crafting a ROP exploit for MIPS Linux, including cache incoherency and delay instructions, but overcomes them to execute custom shellcode. The exploit uses a bind shell for simplicity, granting attackers full control over compromised devices.
This vulnerability is particularly severe due to the absence of Address Space Layout Randomization (ASLR) in affected devices, allowing for reliable exploitation. “Not only can we crash the program, but we can likely control execution flow,” researcher warns. However, these hardware versions have reached their end-of-life support, and TP-Link confirmed they no longer receive security updates. Users are advised to upgrade to newer devices for continued protection.
The analysis and PoC, available on GitHub, serve as a technical resource for understanding the exploit and underscore the importance of keeping hardware up-to-date to mitigate such vulnerabilities.
Impact
- Denial of Service
- Buffer Overflow
- Remote Code Execution
Indicators of Compromise
CVE
- CVE-2024-54887
Affected Vendor
TP-Link
Affected Products
- TP-LINK TL-WR940N
Remediation
- Refer to TP-Link Security Advisory for patch, upgrade, or suggested workaround information.
- Organizations must test their assets for the vulnerability mentioned above and apply the available security patch or mitigation steps as soon as possible.
- Implement multi-factor authentication to add an extra layer of security to login processes.
- Regularly monitor network activity for any unusual behavior, as this may indicate that a cyberattack is underway.
- Organizations must stay vigilant and follow best practices for cybersecurity to protect their systems and data from potential threats. This includes regularly updating software and implementing strong access controls and monitoring tools.
- Develop a comprehensive incident response plan to respond effectively in case of a security breach or data leakage.
- Maintain regular backups of critical data and systems to ensure data recovery in case of a security incident.
- Adhere to security best practices, including the principle of least privilege, and ensure that users and applications have only the necessary permissions.
- Establish a robust patch management process to ensure that security patches are evaluated, tested, and applied promptly.
- Conduct security audits and assessments to evaluate the overall security posture of your systems and networks.
- Implement network segmentation to contain and isolate potential threats to limit their impact on critical systems.

