Severity
High
Analysis Summary
A Russian state-sponsored hacking group known as APT28 has been found using a new zero-day vulnerability to hack into government and defense-related email servers. This campaign, named Operation RoundPress by researchers, focused on webmail platforms like MDaemon, Roundcube, Horde, and Zimbra. The attackers used cross-site scripting (XSS) vulnerabilities in these platforms to silently run malicious code when a user opened a specially crafted email.
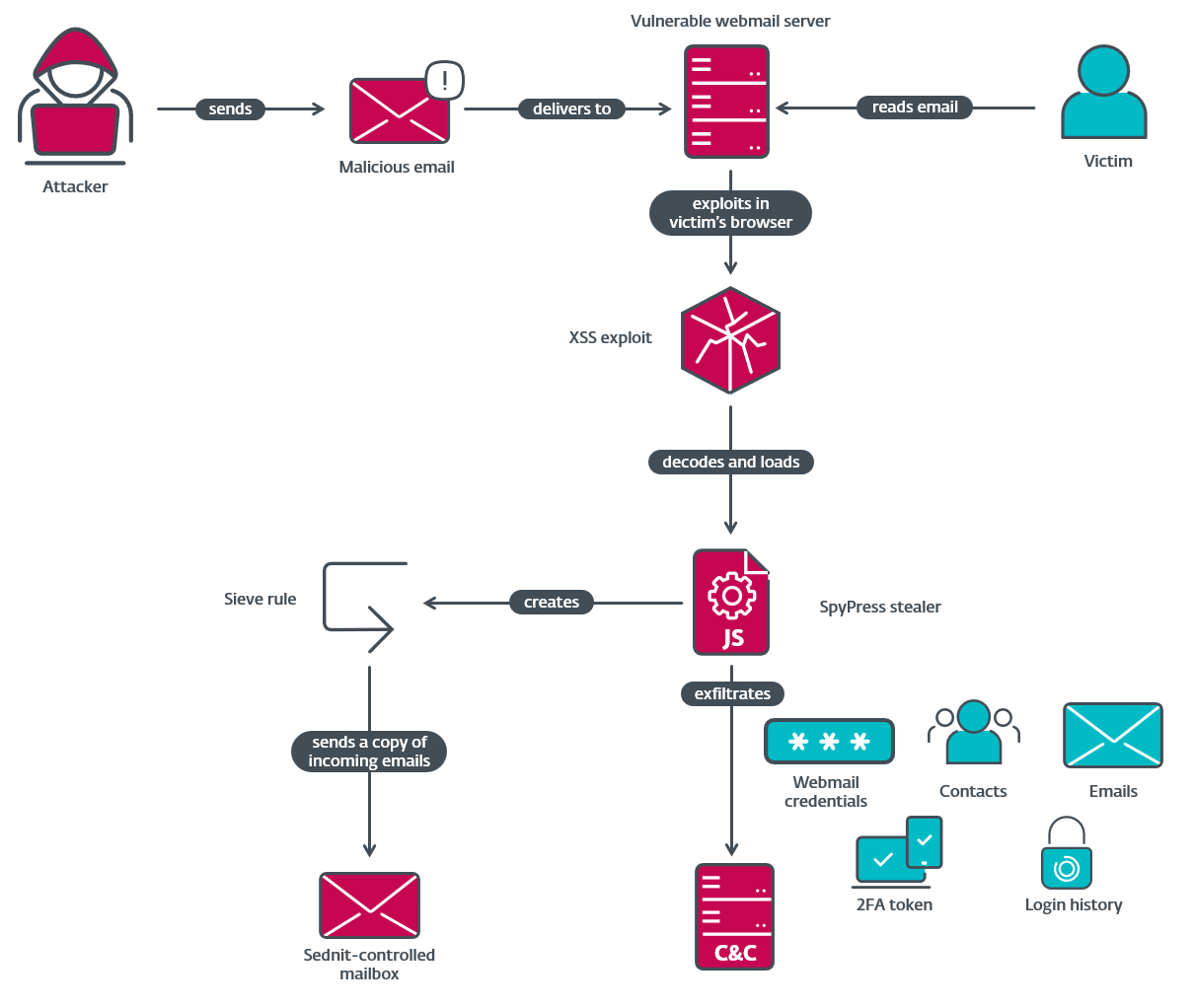
The most serious part of this operation is the use of a zero-day vulnerability in MDaemon Webmail. This flaw, now tracked as CVE-2024-11182, had not been publicly known or patched at the time the attackers started using it. By exploiting this bug, the attackers were able to execute hidden JavaScript code inside the victim’s browser, directly through the email view without needing any click or interaction from the user.
Once the email was opened in a browser through a vulnerable webmail portal, the malicious script would automatically activate. This allowed the attacker to steal the user's email credentials, download their messages, and collect contact lists from the inbox. In some cases, the malware even created custom rules inside Roundcube (called Sieve rules), which secretly forwarded all incoming emails to the attacker’s email address.
The malicious JavaScript payload used in this operation is called SpyPress. It works only when the user opens the email, but if the email is reopened later, the payload gets executed again. Even though this malware doesn’t stay permanently on the system, the attackers used tricks like creating app passwords in MDaemon to keep access even after passwords were changed.
APT28 targeted mostly government departments and defense companies in Ukraine, Bulgaria, and Romania, including those involved in producing Soviet-era weapons. But their scope was wider. They also hit organizations in Greece, Serbia, Cyprus, Ecuador, Cameroon, and parts of Africa and South America. The attackers often sent phishing emails that looked normal but contained hidden JavaScript in the HTML content, making the attack hard to detect.
Impact
- Cross-Site Scripting
- Remote Code Execution
- Sensitive Information Theft
Indicators of Compromise
Domain Name
- sqj.fr
- tgh24.xyz
- tuo.world
- lsjb.digital
- jiaw.shop
- hfuu.de
- raxia.top
- rnl.world
- hijx.xyz
- ikses.net
IP
- 185.225.69.223
- 193.29.104.152
- 45.137.222.24
- 91.237.124.164
- 185.195.237.106
- 91.237.124.153
- 146.70.125.79
- 89.44.9.74
- 111.90.151.167
MD5
- 9280def0cec100bca5d42472b114d8c7
SHA-256
- 335b1cd7708284fc1c2c6678f2f8d6737d68935ec992d680ff540f2e72774665
SHA1
- 65a8d221b9eced76b9c17a3e1992df9b085cecd7
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Patch and update all webmail platforms (MDaemon, Roundcube, Horde, Zimbra) to address known vulnerabilities, especially CVE-2024-11182.
- Implement web application firewalls (WAF) to filter and block malicious scripts.
- Enforce multi-factor authentication (MFA) for all email accounts to reduce impact of credential theft.
- Regularly monitor and audit email forwarding rules (e.g., Sieve rules) for unauthorized changes.
- Conduct phishing awareness training for users to recognize suspicious emails.
- Deploy email security gateways with advanced threat protection to scan and block malicious attachments and scripts.
- Perform regular security assessments and penetration testing on webmail infrastructure.
- Enable strict Content Security Policy (CSP) headers to mitigate XSS attacks in web applications.
- Use application-level monitoring to detect unusual account activities like mass downloads or unexpected logins.
- Review and rotate application passwords periodically, especially after suspicious activities are detected.
- Maintain up-to-date incident response plans for email compromise scenarios.
- Segment critical email infrastructure from internet-facing systems to limit attack surface.
- Collect and analyze email server logs for signs of exploitation and suspicious script executions.
- Utilize browser sandboxing and isolation technologies to limit script execution impact.
- Collaborate with threat intelligence providers for timely updates on emerging threats and zero-day vulnerabilities.

