Severity
High
Analysis Summary
Grandoreiro, a banking malware, has been discovered to use new strategies to evade anti-fraud systems. This suggests that the malicious software is still being actively developed even while law enforcement is working to stop the operation.
Cybersecurity researchers reported, “Only part of this gang was arrested: the remaining operators behind Grandoreiro continue attacking users all over the world, further developing new malware and establishing new infrastructure.”
Other recently added techniques include mouse tracking, ciphertext stealing (CTS) encryption, and the application of a domain generation algorithm (DGA) for command-and-control (C2) communications. Lighter, regional variants that are especially aimed at Mexican bank clients have also been noticed. Since it began operations in 2016, Grandoreiro has continuously changed, expanding its geographic reach to include Latin America and Europe while making an effort to remain undiscovered. It can steal login information from 1,700 financial institutions spread over 45 nations and territories.
Although evidence suggests that it is exclusively available to a restricted group of trusted partners and cybercriminals, it is supposed to function under the malware-as-a-service (MaaS) model. The arrests of several Grandoreiro members, which have caused the malware's Delphi coding to become fragmented, are among the most important events that have happened this year.
The fact that two different codebases are running concurrent campaigns—newer samples with updated code and older samples that still utilize the legacy codebase—supports this finding. The older samples are now exclusively aimed at consumers in Mexico, who are clients of about 30 banks. Grandoreiro is mostly disseminated via phishing emails, with malicious Google advertising playing a smaller role. A genuine file and an MSI loader, which downloads and launches the malware, are both included in the first stage, which is a ZIP file.
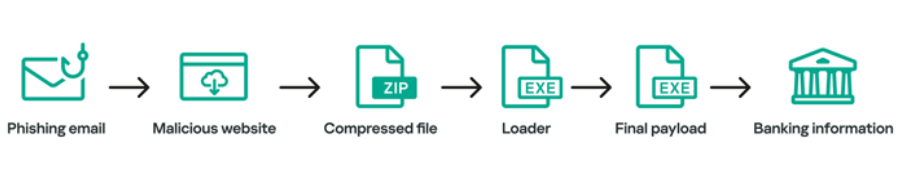
It has been discovered that campaigns seen in 2023 use incredibly huge portable executables—up to 390 MB in size—by posing as AMD External Data SSD drivers in order to get around sandboxes and go undetected. The banking malware has tools to collect IP address location data and host information. Additionally, it extracts the username, determines whether it contains the strings "John" or "WORK," and stops running if it does.
AVAST, Bitdefender, Nod32, Kaspersky, McAfee, Windows Defender, Sophos, Virus Free, Adaware, Symantec, Tencent, Avira, ActiveScan, and CrowdStrike are some of the anti-malware programs that Grandoreiro looks for. Additionally, it searches for financial security software like Trusteer and Topaz OFD. The malware's ability to detect the existence of specific web browsers, email clients, VPNs, and cloud storage apps on the system and track user activity across those apps is another noteworthy feature. Additionally, it can be used as a clipper to redirect cryptocurrency transactions to wallets controlled by the threat actor.
To circumvent automatic analysis, more recent attack chains discovered in the wake of this year's arrests incorporate a CAPTCHA barrier before the primary payload is executed. Significant modifications have also been made to the most recent version of Grandoreiro, which now can self-update, collect keystrokes, choose the country for listing victims, identify banking security solutions, send spam emails using Outlook, and keep an eye out for particular terms in Outlook emails.
Additionally, it has the ability to record mouse movements, which indicates an effort to imitate user behavior and fool anti-fraud systems into thinking the activity is authentic. This finding demonstrates how malware like Grandoreiro is constantly evolving and how attackers are using strategies meant to thwart contemporary security measures that depend on machine learning and behavioral biometrics.
After obtaining the credentials, the threat actors use transfer applications, Bitcoin, gift cards, or an ATM to cash out the money to local money mules' accounts. Telegram chats are used to identify the mules, who are paid between $200 and $500 every day. When a victim starts to browse a specific financial institution website, a Delphi-based application called Operator shows a list of victims, allowing remote access to the victim's computer.
In order to successfully execute attacks against their targets and elude security measures, the threat actors responsible for the Grandoreiro banking malware are constantly improving their strategies and software. Already posing a global danger, Brazilian banking trojans are stepping in to cover the void left by Eastern European gangs transitioning to ransomware.
Impact
- Financial Loss
- Sensitive Data Theft
- Security Bypass
- Keylogging
- Unauthorized Access
Indicators of Compromise
MD5
- f0243296c6988a3bce24f95035ab4885
- dd2ea25752751c8fb44da2b23daf24a4
- 555856076fad10b2c0c155161fb9384b
- 49355fd0d152862e9c8e3ca3bbc55eb0
- 43eec7f0fecf58c71a9446f56def0240
- 150de04cb34fdc5fd131e342fe4df638
- b979d79be32d99824ee31a43deccdb18
SHA-256
- c9cde25c2ca45cda9d70129a010fccce62ce42245e972debb9f3bd71cd3682a5
- 993ae5a4c9da10d48b84943c1c0dc6ccd67ce2b39c0d8ad7af52d4a9d50fd718
- 22bbfbc1022553280c799697b9737772fc2491a1ca20089ce74a877ee1d31a48
- 893cc8f199ed9599e21983220fdb4bc3c3360132c24d158887b67a8cf09fc8f8
- cc3f6cde8a18e1177a32c03b54bb348263dfc6926f345192455aa386a7c23e6b
- 0b233e2c844eb27061363ddc4b0d5ae62812a7ac13bfd4783650f5e3f6e92650
- 10ce3b08784f1d06f4f014ed2005be8418edea4ab8360f084024b5fa9f431894
SHA-1
- 0a4655b8ec4a82d529ca37c9fec595f515cbc3f9
- 4ed4e7ad683993c18de43c22ca97d83515b4c162
- f40b8672914046f6328806056a63c13f4f90ae0c
- 0d23a3c273d7b9fc37e0210225b69e8e4b30c27f
- a2e44430e5924b9cee8102aa9fc9da391c21a709
- 38270d9a549d25d80d0b6bd8211700bdae52f89b
- ae1b6c699f59c4bd4d58f9cb1614919588c3bb74
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Implement multi-factor authentication (MFA) mechanisms such as biometric verification or one-time passwords (OTPs) to add an extra layer of security to banking transactions.
- Utilize advanced threat detection and monitoring tools to proactively identify and respond to suspicious activities or anomalies indicative of mobile banking.
- Adopt secure coding practices and conduct regular security assessments and code reviews to identify and remediate vulnerabilities in mobile banking applications.
- Educate users about the risks associated with mobile banking trojans including phishing scams, social engineering tactics, and suspicious app downloads.
- Establish partnerships with other financial institutions, cybersecurity firms, and law enforcement agencies to share threat intelligence and collaborate on the detection and mitigation of mobile banking trojan campaigns.
- Adhere to industry regulations and compliance standards governing data protection, privacy, and financial transactions.
- Deploy advanced security technologies such as endpoint detection and response (EDR) solutions, network intrusion detection systems (NIDS), and machine learning-based anomaly detection tools, to detect and prevent mobile banking trojan infections.

