Severity
High
Analysis Summary
North Korean-affiliated threat actors have been seen delivering upgraded variants of recognized malware families, such as BeaverTail and InvisibleFerret, to job seekers in the tech sector. The activity cluster, identified as CL-STA-0240, is a component of the Contagious Interview campaign, which researchers initially revealed in November of 2023.
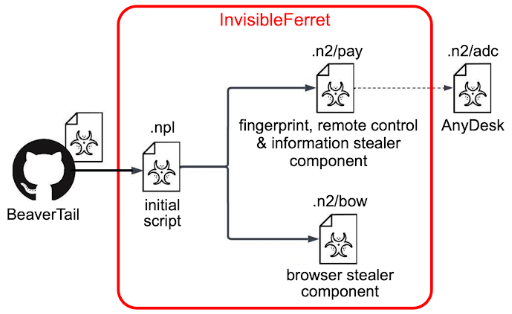
Through job search platforms, the threat actor behind CL-STA-0240 makes contact with software engineers by pretending to be a potential employer. The threat actor tries to persuade the victim to download and install malware during an online interview that the attackers encourage the victim to take part in. The BeaverTail downloader and information stealer, which is intended to target both the Windows and Apple macOS systems, is involved in the initial stage of infection. The InvisibleFerret backdoor, which is based on Python, is facilitated by the malware.
Evidence suggests that the operation is still ongoing even after it was made public, suggesting that the threat actors behind it are still enjoying success in tricking engineers into running malicious code under the guise of a coding assignment. In two independent analyses, security researchers described an attack chain that used BeaverTail and InvisibleFerret to infiltrate developer systems by using phony Windows and macOS video conferencing applications that mimicked MiroTalk and FreeConference.com.
Because of the ongoing efficacy of their strategy, researchers said that the CL-STA-0240 Contagious Interview campaign's general methodology has not altered. Even though the campaign has been well publicized and examined, social engineering tactics—such as posing as recruiters—tend to be very successful, particularly when aimed at those who are oblivious to such risks or would neglect fundamental security precautions when looking for work. Through the use of trust and urgency in work environments, these attackers have developed a dependable technique for accessing victims' systems.
The current version is notable because it uses Qt, a cross-compilation tool for Windows and macOS, to create the fake application. BeaverTail's Qt-based version can retrieve information from several Bitcoin wallets and steal passwords from web browsers. The release of a new, less dubious, and more evasive variant of their malware (BeaverTail, now developed in the Qt framework) that targets both the Windows and macOS platforms could be another reason for the campaign's lack of tactical adjustments.
This makes it possible to apply the same attack technique—fake job interviews and recruiter impersonation—across a wider range of targets and devices without having to significantly alter the campaign's operational mechanics. In addition to transferring the data to a server under the control of an opponent, BeaverTail can download and launch the InvisibleFerret backdoor, which consists of two separate components:
- A primary payload that permits AnyDesk download, remote control, keylogging, data exfiltration, and fingerprinting of the compromised host
- A browser hijacker that gathers credit card details and browser credentials
Threat actors from North Korea have a history of committing financial crimes in order to raise money for the DPRK government. Given that 13 distinct Bitcoin wallets can be stolen by the BeaverTail malware, this effort might have financial motivations.
Impact
- Sensitive Information Theft
- Unauthorized Access
- Identity Theft
- Financial Theft
Indicators of Compromise
IP
- 95.164.17.24
- 185.235.241.208
MD5
- bf82e3b5d25d167c168cc6600e797c53
- 91c89af52df3e3067ab2d3d619fcd345
- 17f47b20c26fd768bcee7b1c4bab9714
- 135848473382204d759a97aeded76f2c
- 8ebca0b7ef7dbfc14da3ee39f478e880
- d24d19a892c6afbd53d8a6e2a4a1f88c
- dc77044fe8d35882015eaa99ca31f826
- ed60b3913e6694f4a0ed2fe25551bd1f
- fb71fc9f4c0a5ff53f301d83b7462f89
- b9693b6541a22d01b100b867375279e6
- b4a46c1738473323590d766704f941f3
- ad98bec0fe9e779451cdefceb457c9b1
- 988f7544f1f4663c3b7cdcf86fdd5052
- d579bd2e8fd4d9eecc35f79420411d07
- bca9efcd61cb480dd8e6b169fbe9f9d9
- cd2b5ea77c71f186b512477392786338
- 08b48b56794242843b9e89fc15dde2dd
- 86098b4a5ae7283128a459ae17b320fb
SHA-256
- 000b4a77b1905cabdb59d2b576f6da1b2ef55a0258004e4a9e290e9f41fb6923
- 9abf6b93eafb797a3556bea1fe8a3b7311d2864d5a9a3687fce84bc1ec4a428c
- 0f5f0a3ac843df675168f82021c24180ea22f764f87f82f9f77fe8f0ba0b7132
- d801ad1beeab3500c65434da51326d7648a3c54923d794b2411b7b6a2960f31e
- 36cac29ff3c503c2123514ea903836d5ad81067508a8e16f7947e3e675a08670
- de6f9e9e2ce58a604fe22a9d42144191cfc90b4e0048dffcc69d696826ff7170
- fd9e8fcc5bda88870b12b47cbb1cc8775ccff285f980c4a2b683463b26e36bf0
- 0621d37818c35e2557fdd8a729e50ea662ba518df8ca61a44cc3add5c6deb3cd
- 9e3a9dbf10793a27361b3cef4d2c87dbd3662646f4470e5242074df4cb96c6b4
- d5c0b89e1dfbe9f5e5b2c3f745af895a36adf772f0b72a22052ae6dfa045cea6
- 07183a60ebcb02546c53e82d92da3ddcf447d7a1438496c4437ec06b4d9eb287
- 10f86be3e564f2e463e45420eb5f9fbdb14f7427eac665cd9cc7901efbc4cc59
- 1c218d15b35b79d762b966db8bc2ca90fc62a95903bd78ac85648de1d828dbce
- 34170bda5eb84d737577096438a776a968cb36eff88817f12317edcb9d144b35
- 4343fa4e313a61f10de08fa5b1b8acb98589faf5739ab5b606f540983b630f79
- 486a9a79bbb81abee2e81679ace6267c3f3e37d9b8c8074f9ec7aebc9be75cdd
- 589e22005aa166b207a7aa7384dd3c7f90b71775688e587108801c3894a43358
- 5e820d8b2bd139b3018574c349cd48ce77e7b31cf85e9462712167fcab99b30a
SHA-1
- 163099f73bc04cce1a604b731ae36bc73c2f932f
- ae8fdc45746fb64036c41490c2ca34052584198b
- 48afb0a9f769d19d02fd156a609161d8819f30bc
- 6d75ee5e44b80c232de75bb9ef2027f519bd3ec7
- 5cce14436b3ae5315feec2e12ce6121186f597b3
- 4af66bd0c6f9045f02cb8d2beb60ef346393e367
- 29d360a46ad5e3ef65d8df81456f54af64e3463f
- 18a2ee2fcd433f0fe27e0b6fc13bdfc890fc637b
- 5fc8c95aa9c485b1b2930a125f929fb6c1f2d7d3
- 69a65e7a28be4f924f5fdf79ea08f050dac760ac
- 8c0dfdd7236b56589b1a32bd3644fe38c7d40da4
- ff46b2146781484909271f1e214b86249ec9dd16
- 8ebb29c0fd817d1d52e2d8a7cb805927207d7206
- 471c975f4fda2b8a6b47d988d68fa78386b615ae
- fb2d9cfe7e4ecd0a18e71f6d3bf9180f1dc79e16
- af45ce4d0ab784c3b726dcfc4cc6b75256874ec5
- 44340d45a71e778d888b426ffd28783a4661d5c4
- a7dd36e1bee5d6e5752e0cc4210d639f974ce75f
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Ensure all operating systems and software are up to date with the latest security patches.
- Employ reliable antivirus and antimalware software to detect and block known threats.
- Regularly update these tools to maintain the latest threat intelligence.
- Implement IDPS to detect and prevent unusual network activity, system behavior, or similar threats.
- Enable two-factor authentication (2FA) on your accounts adds an extra layer of security and can help prevent unauthorized access even if your login credentials have been stolen.
- Regularly backing up your important data can help ensure that you don’t lose any critical information in the event of a malware infection or other data loss event.
- Be wary of emails, attachments, and links from unknown sources. Also, avoid downloading software from untrusted sources or clicking on suspicious ads or pop-ups.
- Use email filtering solutions to block malicious attachments and links that may deliver malware to users via phishing emails.
- Segment your network to limit lateral movement for attackers.
- Employ application whitelisting to only allow approved software to run on systems, reducing the risk of unauthorized applications being executed.
- Implement robust monitoring solutions to detect any unusual or suspicious activities, such as unauthorized access attempts or data exfiltration. Establish an effective incident response plan to respond to and mitigate any potential breaches quickly.
- Make sure all of your software, including your operating system and applications, is up-to-date with the latest security patches. This can help prevent vulnerabilities that info-stealers and other types of malware could exploit.

