Severity
High
Analysis Summary
Threat actors are increasingly relying on a novel method that uses near-field communication (NFC) to extract large sums of money from victims.
Cybercriminals can cash out money from stolen credit cards connected to mobile payment services like Apple Pay or Google Pay and relay NFC traffic using a technique called Ghost Tap by researchers. Criminals can now send users’ tap-to-pay information worldwide in a matter of seconds by abusing Google Pay and Apple Pay. This implies that they can use the victim’s account to make payments from anywhere in the world, even if they don't have the actual card or phone.
These attacks usually include deceiving victims into downloading malware for mobile banking, which then uses an overlay attack or a keylogger to obtain their banking credentials and one-time passwords. As an alternative, it can include a voice phishing element. Once the threat actors get the card information, they proceed to connect the card to Apple Pay or Google Pay. However, the tap-to-pay information is sent to a mule, who is in charge of making fraudulent transactions at a business, to prevent the issuer from blocking the cards.
A valid research tool called NFCGate, which can record, examine, and alter NFC traffic, is used to achieve this. Using a server, NFC traffic can also be transferred between two devices. One device functions as a "reader" that reads NFC tags, while the second device uses Host Card Emulation (HCE) to simulate NFC tags. Although researchers noted in August 2024 that threat actors had previously exploited NFCGate to transfer NFC information from victims' smartphones to the attacker via NGate malware, this latest revelation is the first instance of the program being misused to relay the data.
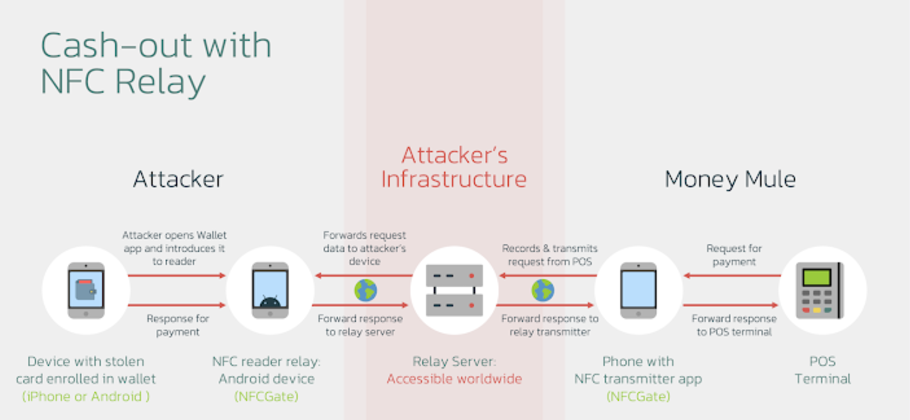
In order to remain anonymous and carry out cash-outs on a bigger scale, cybercriminals can set up a relay between a device with a stolen card and a PoS terminal at a merchant. In addition to using the same card in several places in a short amount of time, the cybercriminal who has the stolen card may be located distant from the place (even a different nation) where it will be used.
Additional benefits of the strategy include the ability to buy gift cards at real stores without the fraudsters needing to be there. Even worse, it can be used to quickly recruit multiple mules at various locations to scale the fraudulent scheme. The fact that transactions seem to be coming from the same device, circumventing anti-fraud measures, makes it more difficult to detect Ghost Tap attacks. It may be more difficult to determine their precise location and the fact that the associated card was not used to complete the transaction at the PoS terminal if the device is in airplane mode.
Researchers believe that these attacks, in which the actual devices with cards are physically located far from the location where transactions are performed (the device is not present at PoS or ATM), were made possible by the evolution of networks with increasing communication speeds combined with a lack of appropriate time-based detection on ATM/POS terminals. This cash-out approach poses serious problems for both financial institutions and retail businesses due to its capacity for quick scaling and anonymity.
Impact
- Financial Loss
- Unauthorized Access
- Credential Theft
Remediation
- Emails or SMSs from unknown senders should always be treated with caution.
- Never trust or open links and attachments received from unknown sources/senders.
- Implement email filtering and anti-phishing solutions to detect and block malicious emails before they reach users' inboxes.
- Educate employees about the risks of phishing attacks and provide training on how to recognize and report suspicious emails.
- Regularly backup your data to a secure location, such as a cloud storage service or external hard drive.
- Deploy endpoint security solutions, including antivirus software and intrusion detection systems, to detect and mitigate malicious payloads delivered through phishing emails.
- Regularly update and patch software and operating systems to address vulnerabilities that could be exploited by cyber attackers.
- Utilize network monitoring and logging tools to detect and respond to unusual or suspicious network activity indicative of a phishing attack.
- Enforce strict access controls and least privilege principles to limit the impact of successful phishing attacks by restricting user permissions and access to sensitive data and systems.
- Implement multi-factor authentication (MFA) to add an extra layer of security to user accounts and prevent unauthorized access in the event of compromised credentials.
- Establish incident response procedures and protocols to quickly identify, contain, and remediate phishing attacks, including communication plans for notifying affected parties and stakeholders.
- Collaborate with industry partners, government agencies, and cybersecurity organizations to share threat intelligence and best practices for defending against phishing attacks.

