Severity
High
Analysis Summary
Researchers have found a new variant of the infamous Android malware family called FakeCall, which uses voice phishing, often known as vishing, to deceive users into disclosing personal information.
FakeCall is a very advanced vishing attack that uses malware to gain almost total control over a mobile device, including the ability to intercept calls both inbound and outbound. By imitating the typical user experience on the device, victims are deceived into calling fake phone numbers under the attacker's control.
Since its appearance in April 2022, researchers have conducted numerous analyses on FakeCall, also known as Letscall and FakeCalls. South Korean mobile users have been the main target of earlier attack waves. FakeCall exploits accessibility services APIs to record information on the screen and give itself extra permissions when necessary, just like other families of Android banking malware that are known to misuse them to take over devices and carry out malicious activities.
Other espionage features include taking pictures, recording a live stream from the front and rear-facing cameras, adding and removing contacts, grabbing audio snippets, uploading images, and using the MediaProjection API to mimic a video stream of all the device's activities. Other features include capturing various information, including SMS messages, contact lists, locations, and installed apps. The latest models are also made to monitor the device's screen condition and Bluetooth status. However, the malware's capacity to monitor all incoming and outgoing calls is made even more harmful by instructing the user to select the program as the default dialer.
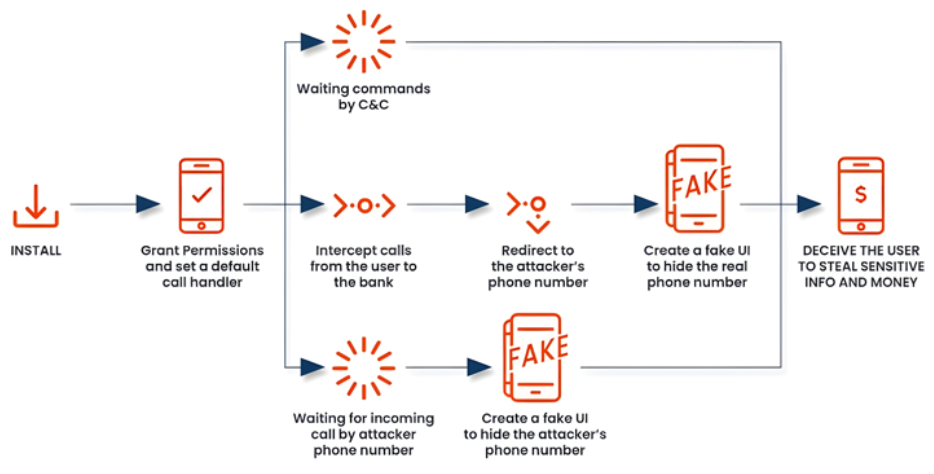
This gives FakeCall the ability to not only intercept and take over calls but also change a called number—like those to a bank—to a rogue number that they control and trick the victims into doing things they didn't plan to do. On the other hand, earlier iterations of FakeCall were discovered to trick users into calling the bank from within the malicious software, which was posing as a loan offer with a cheaper interest rate.
The software diverts calls to a phony number under the attacker's control when the affected person tries to get in touch with their financial institution. The malicious app will trick the user by presenting a convincingly false user interface (UI) that mimics the actual Android call interface with the bank's phone number. Because the malware's phony user interface will resemble the real banking experience, the victim won't be aware that they are being manipulated. This allows the attacker to obtain sensitive data or access their financial accounts without authorization.
In response to enhanced security measures and the widespread use of caller identification apps, which can flag questionable numbers and alert consumers to possible spam, new and advanced mishing (also known as mobile phishing) tactics have emerged. Google has also been testing a security project in Singapore, Thailand, Brazil, and India in recent months that automatically prevents the side-loading of potentially dangerous Android apps, including those that ask for accessibility services.
Impact
- Exposure of Sensitive Data
- Cyber Espionage
- Financial Loss
- Unauthorized Access
Indicators of Compromise
Domain Name
- allcallpush01.com
- allcallpush02.com
- allcallpush09.com
- allcallpush12.com
- allcallpush15.com
- chaowen000.com
- chaowen006.com
- chaowen105.com
- ending052.com
- tewen006.com
- tewen007.com
- vipyaooba.com
- wending015.com
MD5
- 2cd3a379b5df599e200127c719957cb5
- 857fb214a5ef100fe82cf7f4c7e15499
- 4efc6af0c4f1512933f53ca6e5668b75
- ba5c6dd2a632cb12bd4d2d7eff125510
- e6f74adc2f1ea26eb8ffba9d308dee72
- d6f6290c38d02d54b744b611f9f552ea
- 5d51b02f5270a1e1dbb1c96ec1e7940f
- b4082ac4e60e34ab1b25b348ea2efafe
- b2266670fd424e969faf7aec865594fa
- ac4204a14d0155449434c778832bf494
- 6456f84095c981bc9cd8af365be08d0a
- a6c7ecd14d6f71aef781a153edb4af57
- 0b2c68e87d4ca2f0f24e56dc5d2f82bd
- 61fd592343dcaa77d38981e7b1eb0fab
- 8cdffce37db2caab459511930823fcc0
SHA-256
- 473afda00aaf2bbff5d7c9aaa5933ba5f201b469b8546932c60119b1cf40471b
- ce154ff877691c22380cc0e67979f8d9f3ab59986b66c7b03bdab36805cfef8e
- 71073653f9992633dfbb38550cd196a7f201a8da6bea6ef88173ee2817ba023e
- fbdce3dd097f4a01814a14fa0e37c0e9a7618c0801adffb7c4dbd2e6927c220f
- 543734a2bb06d0433283a3b49d48f38b7ed500af82b47209a6087090bf1796cc
- fabdf6f305ed33293ffaac8651657426a6fa4a5bba79d95bf6b3ff481e9e6400
- 099fce4dd0f15f591f59d9e39d68c669c7ec4e421c113d86605626318e4751b5
- f886026ae6b194440eb135329bc9c6b56218560303207bd3ca45134cc6e66eeb
- d1b6ba52a08cc1eb508cb4abd236a27f5fa4d2299718485969b179cd70ffc072
- c1d412b16811f0698dec4276f9ce6f92774e0dd8eb22ffcd386b0341312ef8a5
- 2629eaf1a4477638d44797d3eab9bba1b40aeb3dfd46462813923a3ca149ff28
- baad3941f6e291aa8288ceb9f72c06c3d3fd802e89865777832f20bd5127e4fd
- 2bb50b25ecf6263514bf1922967cb93e4768f96485ee3d9f9bb6417c950cc1c7
- 9d39ace2806389638878646a90af23c716ad9f2c6d142f91f321b2324cbc2e6e
- 5daac96d677763c6e4b802501d56251960cc38f2e74fe81e8cf921672aa57c3b
SHA-1
- 065dacd2b219c1077ad73de8e868234b9456824c
- 95a56084587395cc5d2faa6e4fdf290d6b6501ca
- 4f270443336d4ad0f6f1cdf0412276a2d493238e
- 80ae4fc6b7c6f2c8374e0cd1bb2368ab1a8c5f09
- 685f87dfc403509c1ba33527a9f1447535df5077
- a1c4f0da62946896a5ea8a3bb207586bf37b8452
- c6230451d7e487ede0253d33fa7e546ba4d1250e
- f7f90f362628834ccba71b3ceb4f96a0ec99afbf
- c8e2c8e59bf3392e05117f8e5a1b2ee4b89d3c72
- 919c59f597e2178438a6cfa272d0ba1c1f7f19b9
- 5bb556cd25af9fca763a02fc89db1b8cd2fbc322
- f7add9cd0d20e5fc0907f1591a7fdfcebacc0b04
- f5a8282f48c1895435fed871f774627182797777
- 7cbf6b642efa84601281ed9556d5bc232759d9c4
- d9656de4c8951fdc81fea95f1f756b0ba3a76bb9
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Implement multi-factor authentication (MFA) mechanisms such as biometric verification or one-time passwords (OTPs) to add an extra layer of security to banking transactions.
- Utilize advanced threat detection and monitoring tools to proactively identify and respond to suspicious activities or anomalies indicative of mobile banking.
- Adopt secure coding practices and conduct regular security assessments and code reviews to identify and remediate vulnerabilities in mobile banking applications.
- Educate users about the risks associated with mobile banking trojans including phishing scams, social engineering tactics, and suspicious app downloads.
- Establish partnerships with other financial institutions, cybersecurity firms, and law enforcement agencies to share threat intelligence and collaborate on the detection and mitigation of mobile banking trojan campaigns.
- Adhere to industry regulations and compliance standards governing data protection, privacy, and financial transactions.
- Deploy advanced security technologies such as endpoint detection and response (EDR) solutions, network intrusion detection systems (NIDS), and machine learning-based anomaly detection tools, to detect and prevent mobile banking trojan infections.

