Severity
High
Analysis Summary
A newly uncovered and highly sophisticated strain of malware targeting Windows systems has demonstrated advanced evasion capabilities, successfully operating undetected for weeks. Identified within a compromised system’s memory, the malware embedded itself in the dllhost.exe process (PID 8200), maintaining persistent access and avoiding traditional detection mechanisms. Its discovery stemmed from a detailed investigation involving a 33GB memory dump.
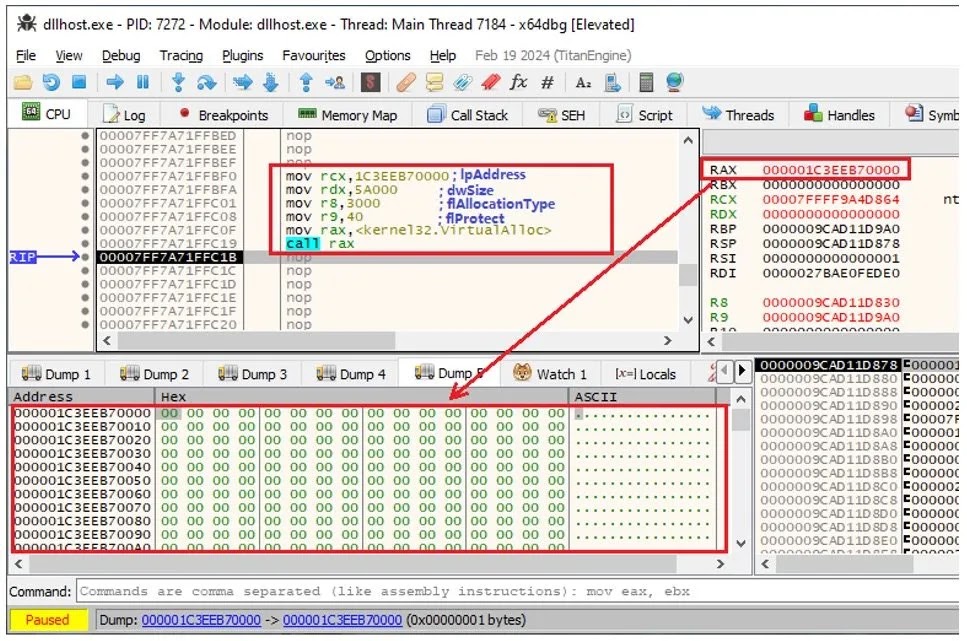
Security researchers, in particular, found that the malware was delivered via a sequence of batch scripts and PowerShell commands, indicating a deep understanding of Windows internals and system architecture by the threat actors.
Classified as a Remote Access Trojan (RAT), the malware possesses extensive features designed for deep system compromise and data exfiltration. It can capture and transmit screenshots, control remote servers for command and control (C2) operations, and manipulate system services through the Windows Service Control Manager API. Its C2 communications are secured using Windows security APIs such as SealMessage() and DecryptMessage(), employing encryption techniques that hinder network-based detection and make forensic analysis significantly more difficult.
One of the malware’s most notable innovations is its use of a rare and highly effective evasion technique: the deliberate corruption of the DOS and Portable Executable (PE) headers.
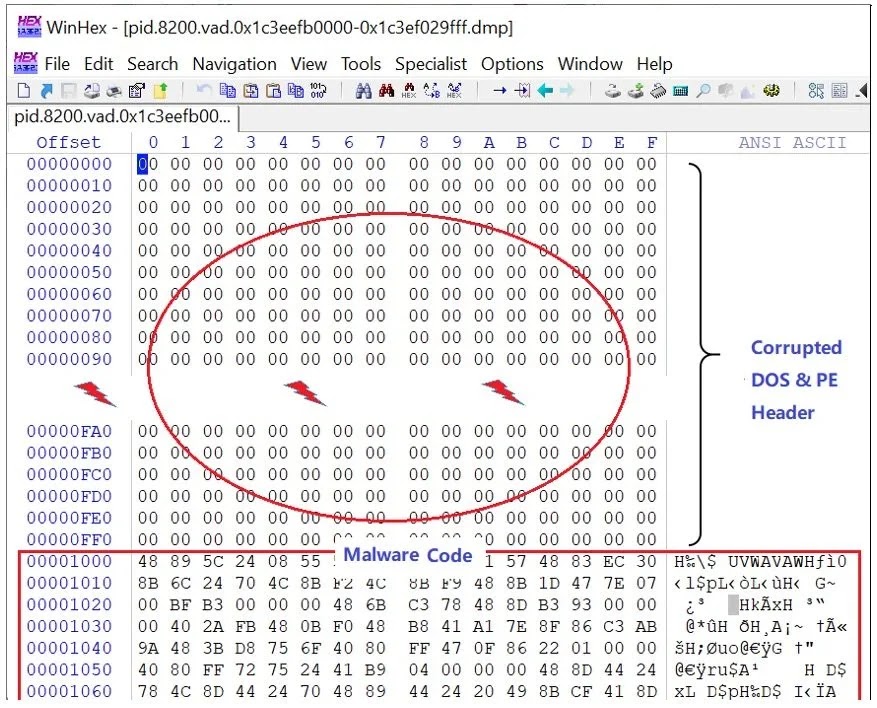
These headers, crucial for security tools and reverse engineering, are nullified post-execution by overwriting them with zero bytes. While Windows no longer needs these headers once a file is running, their absence renders conventional analysis tools nearly useless. Security analysts had to manually locate the malware’s entry point using instruction pattern recognition, ultimately pinpointing the function at address 0x1C3EEFEE0A8 via IDA Pro, emphasizing the intense manual effort required.
Further complicating the analysis, the malware dynamically resolves its API imports using obfuscation techniques like XOR operations and indirect jumps. For example, the code at address 0x1C3EEEE1CE0 ultimately resolved to valid Windows API functions, such as one in GDI32.dll at 0x7FFD74224630. These layered anti-analysis mechanisms not only show a high level of technical sophistication but also reflect a broader trend in malware development, where adversaries prioritize stealth and longevity in compromised environments. This case highlights the urgent need for more advanced memory forensic tools and techniques to combat such threats in enterprise networks.
Impact
- Data Exfiltration
- Security Bypass
- Gain Access
Indicators of Compromise
Domain Name
- rushpapers.com
URL
- https://rushpapers.com/ws/
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Disconnect any suspected systems from the network to prevent lateral movement and further data exfiltration.
- Use advanced memory analysis tools (e.g., Volatility, Rekall) to analyze live memory dumps and detect malware hiding without PE headers.
- Due to the malware's stealth and persistence, it's recommended to fully wipe and reinstall affected systems to ensure complete removal.
- Assume that all credentials on infected systems have been compromised. Enforce organization-wide password resets and review privileged account activity.
- Ensure all Windows systems are up to date with the latest security patches. Disable unnecessary services and restrict the use of PowerShell and batch scripts where possible.
- Use tools like Microsoft AppLocker or WDAC to prevent unauthorized executables and scripts from running.
- Deploy EDR solutions that support memory scanning and behavioral analysis, not just file-based detection.
- Continuously inspect network traffic for signs of encrypted outbound communications to unknown or suspicious IP addresses.
- Investigate recent changes to services and validate that only legitimate service binaries are running.
- Consider involving third-party experts to assist in analyzing advanced threats and ensuring full remediation.

