Severity
High
Analysis Summary
A recent campaign that uses HTML smuggling to spread the commodity trojan DCRat (also known as DarkCrystal RAT) has targeted users who speak Russian.
This is the first time the malware has been spread in this way, which differs from previously known distribution methods like phishing emails with PDF attachments or Microsoft Excel sheets containing macros, or corrupted or false websites. The main purpose of HTML smuggling is payload delivery. The payload may be obtained from a remote resource or included within the HTML itself.
On the other hand, fraudulent websites or malicious spam campaigns may spread the HTML file. Upon initiating the file through the victim's web browser, the hidden payload is decrypted and downloaded onto the device. Subsequently, the attack relies on a certain degree of social engineering to persuade the target to access the malicious payload.
To avoid detection, researchers reported that they had found Russian-language HTML pages that looked similar to TrueConf and VK and, when being opened in a web browser, would automatically download a password-protected ZIP bundle to disk. A nested RarSFX archive found in the ZIP payload eventually causes the DCRat malware to be deployed.
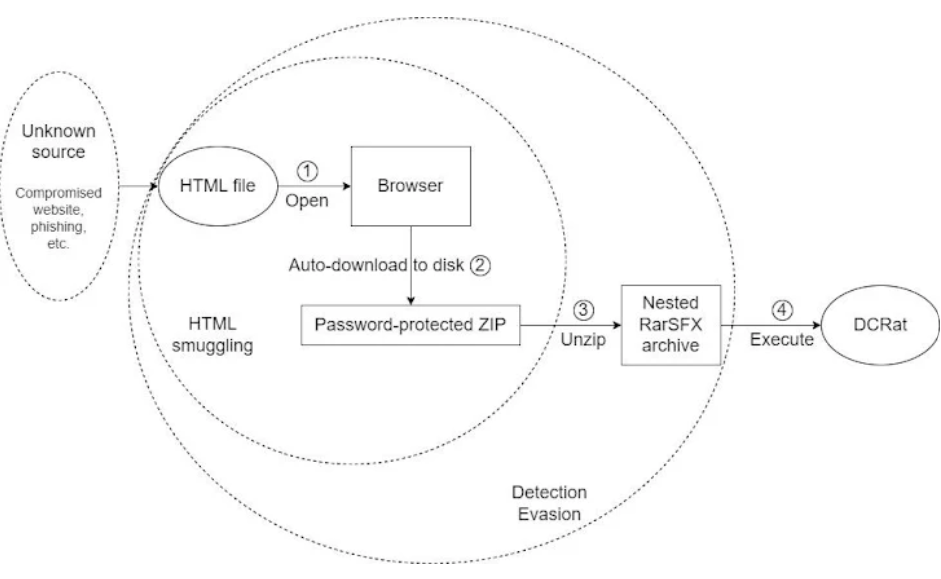
DCRat was first made available in 2018 and can operate as a complete backdoor with the inclusion of further plugins to expand its capabilities. Among other things, it can log keystrokes, run shell commands, and exfiltrate data and passwords. It is advised that organizations examine both HTTP and HTTPS traffic to make sure their systems aren't interacting with rogue domains.
Impact
- Keylogging
- Command Execution
- Data Exfiltration
- Sensitive Data Theft
Indicators of Compromise
Domain Name
- cr87986.tw1.ru
MD5
- 74e58482b63905692e7e50d92e6b48a9
- 1af7452c565df7a07bd47b4e46a4cc65
- 365630241faf63fc7ab0c37bcac6e426
- 90b238db0cc0dc15bafa33ab7709ad8b
SHA-256
- 2c898cc8d4ed2e67effe5362bf7951143563a965057110d6b803b983e7db3eb5
- 693e681c06e3b8f374bd5e25daa6c70d4947956f1aa5e1cb7a18f2da0844323f
- 763c1f21d22b7215d36e2dbd52d141d71d9e540c19f631f63f151c283b91f0d8
- 60665c8f8ff802fb116a4d761a812911a0cf209e5e56f48fdb566e94cc177c33
SHA-1
- ea9447987fc01e75ae973442964d5f95f193a93c
- 6767df97b566358852148961097771a2774e1326
- b06b7e8c83df5980802e6b04d4639de0550c2ff4
- efb1d3856ce827acb195c0e0012afa14542837a3
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Emails from unknown senders should always be treated with caution.
- Never trust or open links and attachments received from unknown sources/senders.
- Enable antivirus and anti-malware software and update signature definitions on time. Using multi-layered protection is necessary to secure vulnerable assets.
- Patch and upgrade any platforms and software on time and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.

