Severity
High
Analysis Summary
As part of a recent attack campaign, the Iranian nation-state actor MuddyWater was detected utilizing a backdoor that had never been seen before. This marks a departure from its well-known strategy of utilizing genuine remote monitoring and management (RMM) software to maintain permanent access.
Independent research conducted by cybersecurity researchers, who have nicknamed the malware strains BugSleep and MuddyRot, indicates as much. Unlike prior campaigns, MuddyWater did not use the official Atera remote monitoring and management tool (RRM) as a validator and instead modified its infection chain. Rather, it was seen that they were using a recently acquired, unregistered implant. Turkey, Azerbaijan, Jordan, Saudi Arabia, Israel, and Portugal are among the nations that were targeted.
Iranian Ministry of Intelligence and Security (MOIS) is believed to be connected to MuddyWater, also known as Boggy Serpens, Mango Sandstorm, and TA450, a state-sponsored threat actor. Using spear-phishing lures in email messages, the organization has launched fairly frequent cyberattacks that use a variety of RMM tools, including Atera Agent, RemoteUtilities, ScreenConnect, SimpleHelp, and Syncro.
Researchers reported earlier in April that they had observed an increase in MuddyWater operations that have been supplying Atera Agent to companies in Israel, India, Algeria, Turkey, Italy, and Egypt since late October 2023. Airlines, IT firms, telecoms, pharmaceuticals, the car industry, logistics, travel, and tourism are among the industries targeted. Obtaining access to corporate email accounts is a top aim for MuddyWater as part of their continuous attack activities.
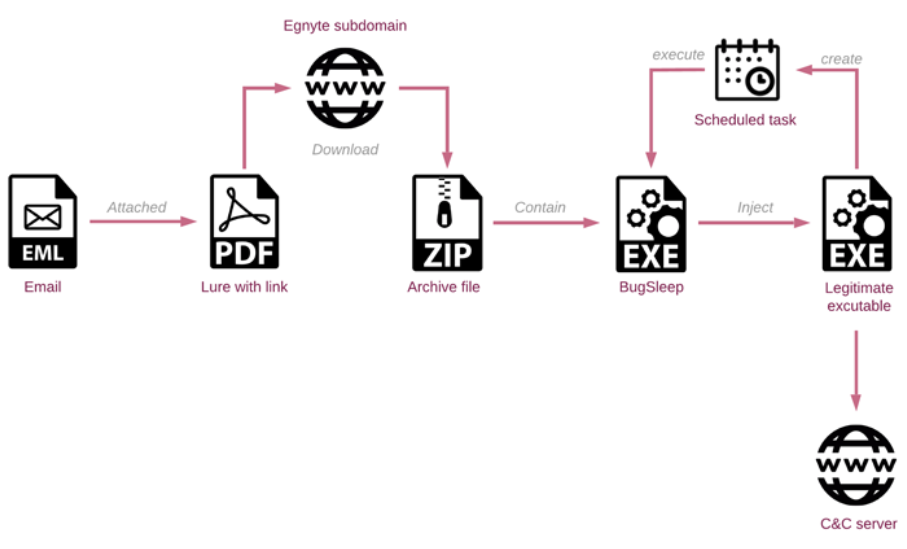
With the use of these compromised accounts, the group can persist inside the targeted organizations, increase the legitimacy and efficacy of their spear-phishing attempts, and avoid detection by blending in with normal network traffic. The most recent attack chains operate similarly, using hacked email accounts associated with reputable businesses to send spear-phishing messages that point to an Egnyte subdomain—which has been exploited by threat actors in the past to spread Atera Agent—either directly or through a PDF attachment.
BugSleep, also known as MuddyRot, is an x64 implant written in C with the ability to initiate a reverse shell, download and upload any file to and from the compromised host, and establish persistence. A raw TCP socket on port 443 is used for communications with a command-and-control (C2) server. The victim host fingerprint, which consists of the hostname and username connected by a slash, is the first message to be transmitted to the C2. The software terminates if the victim receives a '-1,' but if not, the malware starts an endless loop in which it waits for the C2 to issue new commands.
Although the reason behind MuddyWater's switch to a custom implant is presently unknown, it's thought that security vendors' heightened observation of RMM tools may have contributed. MuddyWater's heightened activity in the Middle East, especially in Israel, emphasizes how tenacious these threat actors are in their pursuit of a wide range of regional objectives. They've been using phishing attacks consistently, and the addition of a proprietary backdoor, BugSleep, to their arsenal of techniques, tactics, and procedures (TTPs) is a noteworthy advance.
Impact
- Command Execution
- Cyber Espionage
- Sensitive Data Theft
Indicators of Compromise
IP
- 91.235.234.202
- 146.19.143.14
- 85.239.61.97
MD5
- a50a20edddaded453410600549968914
- c17f4bb8e415e21e6010b98e13c6dff3
- d783001d1f98fe3b33e7b97b0b7d96dc
- a713e686fd984588a4db74f34bf32275
- e7df84a5a22aeafcf1c3abf4fd986c91
SHA-256
- 94278fa01900fdbfb58d2e373895c045c69c01915edc5349cd6f3e5b7130c472
- b8703744744555ad841f922995cef5dbca11da22565195d05529f5f9095fbfca
- 73c677dd3b264e7eb80e26e78ac9df1dba30915b5ce3b1bc1c83db52b9c6b30e
- 960d4c9e79e751be6cad470e4f8e1d3a2b11f76f47597df8619ae41c96ba5809
- 5df724c220aed7b4878a2a557502a5cefee736406e25ca48ca11a70608f3a1c0
SHA-1
- d76e5ac85cd57425dc3c5dc27c438b0725d6eaa4
- e2bee0b9a6e262daa4842245e469f5a0310da868
- b99d3ac574d6611c7304ef87e9c51c187bb5dd42
- dfaae4c2ac9a19d2ef0fde43b6786a01b39b5521
- 72775239683ea6a651b5c73d2e3ed006af5e1cad
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Enable antivirus and anti-malware software and update signature definitions promptly. Using multi-layered protection is necessary to secure vulnerable assets.
- Patch and upgrade any platforms and software timely and make it into a standard security policy.
- Employ network intrusion detection and prevention systems to monitor and block malicious network activities.
- Implement network segmentation to limit lateral movement for attackers within the network.
- Implement advanced email filtering to detect and block phishing emails.
- Employ updated and robust endpoint protection solutions to detect and block malware.
- Develop and test an incident response plan to ensure a swift and effective response to security incidents.
- Enhance logging and monitoring capabilities to detect anomalous activities and unauthorized access.
- Conduct regular security audits and penetration testing to identify and address potential vulnerabilities.
- Regularly back up critical data and ensure that backup and recovery procedures are in place.

