Severity
High
Analysis Summary
Microsoft's latest "Cyber Signals" report reveals critical information about Storm-0539, also known as "Ant Lion," a Moroccan hacking group that has ramped up its activities in the lead-up to major holidays including Memorial Day.
This financially motivated group, active since 2021 focuses primarily on gift card and payment card fraud. The FBI has already flagged this group earlier in the month highlighting their sophisticated methods that mimic those of state-sponsored threat actors and cyber espionage groups. Storm-0539's modus operandi involves extensive reconnaissance and the deployment of custom-crafted phishing emails and SMS messages targeting employees of gift card issuing organizations.
Once they obtain access through these phishing campaigns, the attackers register their own devices with the company's multi-factor authentication (MFA) platforms ensuring persistence. They then move laterally within the organization compromising various systems including virtual machines, VPNs, SharePoint, OneDrive, Salesforce, and Citrix environments. This comprehensive intrusion cycle enables them to gain the credentials necessary for creating and redeeming new gift cards.
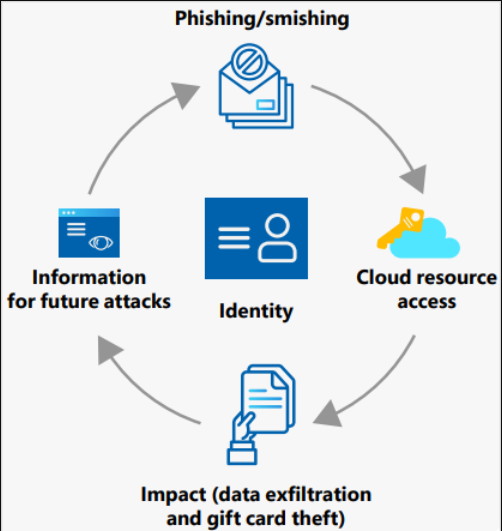
A significant aspect of Storm-0539's strategy is their exploitation of cloud service providers to conduct large-scale operations at minimal cost. By creating websites that impersonate non-profit organizations, they sign up for "pay as you go" or "free trial" tiers offered by these cloud services. This tactic allows them to operate their illegal activities efficiently and economically, resembling techniques used by state-sponsored actors. Microsoft's report notes that these methods once exclusive to espionage and geopolitical adversaries are increasingly adopted by financially motivated cybercriminals.
The impact of Storm-0539's activities is substantial. The group typically issues high-value gift cards just below organizational limits such as creating a card worth $99,000 if the limit is $100,000. Then it monetizes these cards by selling them online, often through dark web markets or money mules. Microsoft's report cites instances where the group has stolen up to $100,000 a day from certain companies. This highlights the urgent need for organizations to tighten their security measures to prevent such significant financial losses.
In response to these threats, Microsoft recommends several defense strategies for gift card issuing portal operators. These include constant monitoring for anomalies, implementing conditional access policies, and ensuring that no single account can generate an unusually large number of gift cards. Additional measures include token replay protection, enforcing least privilege access, and utilizing FIDO2 security keys to protect high-risk accounts. Merchants also play a crucial role by recognizing and rejecting suspicious orders thereby disrupting the profit chain for these cybercriminals.
As Memorial Day approaches, Microsoft advises internet users to remain vigilant against scams, fake shops, and malvertising. Although Storm-0539 primarily targets organizations rather than end-users, heightened caution is essential for everyone to avoid falling victim to various online threats. The report underscores the evolving nature of cyber threats and the importance of robust cybersecurity practices to protect against increasingly sophisticated and financially motivated attackers.
Impact
- Financial Loss
- Cyber Espionage
- Credential Theft
Remediation
- Organizations that issue gift cards should implement continuous monitoring to detect unusual activities, such as an unexpectedly high number of gift card generations or large-value cards being issued.
- Utilizing advanced behavioral analytics can help identify patterns that deviate from normal operations, signaling potential malicious activities.
- Implement conditional access policies that limit the ability of any single account to generate a large number of gift cards. This reduces the risk of a compromised account causing significant damage.
- Enforce policies that restrict access based on geographic locations and ensure that only registered, trusted devices can access critical systems.
- Ensure that MFA is robust and mandatory for all critical systems. Consider using more secure forms of MFA, such as hardware tokens or biometric authentication, to reduce the risk of MFA bypass through phishing or social engineering.
- Adopt FIDO2 security keys for high-risk accounts to provide an additional layer of security, making it harder for attackers to gain access even if credentials are compromised.
- Apply the principle of least privilege to ensure that users have the minimum necessary access to perform their duties. Regularly review and update permissions to prevent privilege creep.
- Implement RBAC to manage permissions based on the user’s role within the organization, ensuring that only those who need access to sensitive areas have it.
- Implement measures to protect against token replay attacks, where attackers reuse authentication tokens to gain unauthorized access. This can include using short-lived tokens and ensuring tokens are tied to specific sessions and devices.
- Conduct regular training sessions for employees to recognize phishing attempts and understand the importance of reporting suspicious emails and messages.
- Educate staff on best practices for password management, recognizing social engineering tactics, and the importance of following security protocols.
- Regularly audit and secure cloud environments to ensure they are not being exploited by attackers. Use advanced security features provided by cloud service providers to monitor and protect cloud resources.
- Participate in information-sharing initiatives with other organizations and cybersecurity communities to stay informed about emerging threats and tactics used by groups like Storm-0539.
- Develop and regularly update incident response plans to ensure quick and effective action in the event of a breach. Conduct drills to prepare for real-world scenarios.

