Severity
High
Analysis Summary
Latin American financial institutions are under increasing threat from the Mekotio banking trojan, a Windows malware known for targeting countries such as Brazil, Chile, Mexico, Spain, Peru, and Portugal to steal banking credentials.
According to researchers, there has been a recent surge in attacks distributing this malware. Active since 2015 and first documented in August 2020, Mekotio is part of a group of banking trojans that includes Guildma, Javali, and Grandoreiro, the latter of which was dismantled by law enforcement earlier this year. Mekotio is written in Delphi, utilizes fake pop-up windows, contains backdoor functionality, and targets Spanish and Portuguese-speaking regions.
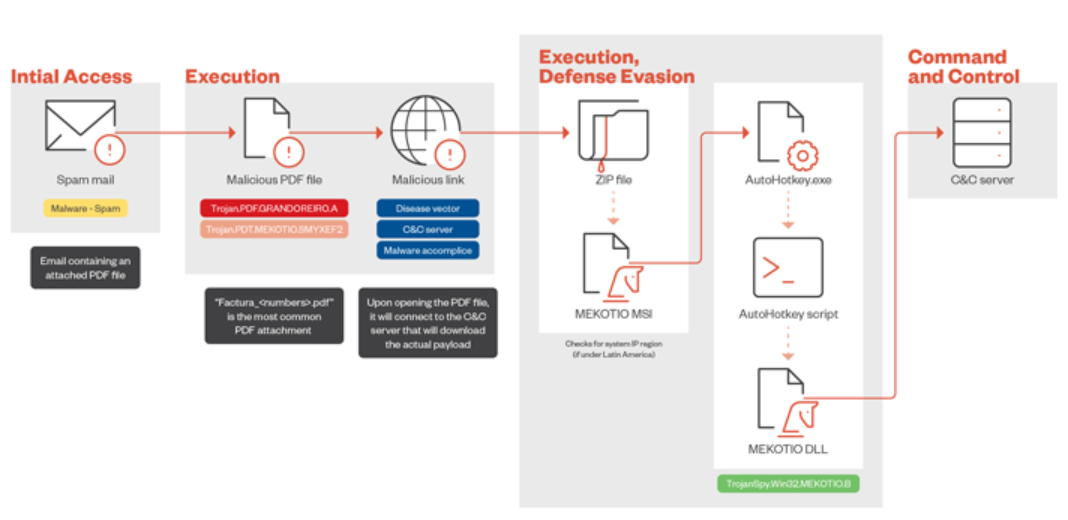
The Mekotio operation faced a significant setback in July 2021 when Spanish law enforcement arrested 16 individuals connected to a criminal network responsible for delivering Mekotio and Grandoreiro via social engineering campaigns targeting European users. Attack chains typically involve tax-themed phishing emails that trick recipients into opening malicious attachments or links leading to the deployment of an MSI installer file.
This installer uses an AutoHotKey (AHK) script to launch the malware, marking a deviation from a previously documented infection process that used an obfuscated batch script to run a PowerShell script. Once installed, Mekotio gathers system information and connects to a command-and-control (C2) server for further instructions. Its primary goal is to steal banking credentials by displaying fake pop-ups mimicking legitimate banking sites.
Additionally, it can capture screenshots, log keystrokes, steal clipboard data, and establish persistence on the infected machine through scheduled tasks. The harvested information allows threat actors to access victims' bank accounts and execute fraudulent transactions, posing a significant threat to financial systems in Latin America.
Alongside Mekotio, a new threat named Red Mongoose Daemon has emerged. This banking trojan, like Mekotio, employs MSI droppers distributed via phishing emails disguised as invoices and tax notes. Aimed at Brazilian end users and employees with banking information, Red Mongoose Daemon's primary objective is to steal banking details by spoofing PIX transactions through overlapping windows. It also can manipulate and create windows, execute commands, control computers remotely, hijack clipboards, and impersonate Bitcoin wallets by replacing copied wallets with those controlled by cybercriminals.
Impact
- Credential Theft
- Keylogging
- Financial Loss
Indicators of Compromise
Domain Name
- tudoprafrente.org
IP
- 23.239.4.149
- 68.233.238.122
URL
- https://christcrucifiedinternational.org/descargafactmayo/eletricidad/
- https://intimaciones.afip.gob.ar.kdental.cl/Documentos_Intimacion/
- https://techpowerup.net/cgefacturacl/descargafactmayo/eletricidad/
MD5
- d447a2f6c83e2f6c18bad592ed029bdd
- 00329d659b4166066737320f725cfd93
- 38a9671a253750cbe517ce75af2117e3
- 3e4f3d7f962653220759a1169c3bad45
- 6c81cf6d72baffb7cfe0d62d8d17d5f4
SHA-256
- b6a82774b81a965033716351d92dd0a75f494069b4b4436d21327c06c917e6e0
- e082dc1c11afff40efe2cf92e36ac37129b78320b5cc656f4b80488307770eab
- 008c7e556beba4a5d026211259114ba686013b5fd5f9cb9e677b2641bd2c2fc5
- a7112aa5b398fc7a77100164c818b5e17612d828320b4e3e1f895e56b4fd6797
- 439eecb230fb53b817ae535d6a6d978066134b4b52e49e065e9ddeff5f2bbbd3
SHA-1
- 5e92f0fcddc1478d46914835f012137d7ee3c217
- f68d3a25433888aa606e18f0717d693443fe9f5a
- 3fe5d098952796c0593881800975bcb09f1fe9ed
- 1087b318449d7184131f0f21a2810013b166bf37
- ef22c6b4323a4557ad235f5bd80d995a6a15024a
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Implement multi-factor authentication (MFA) mechanisms such as biometric verification or one-time passwords (OTPs) to add an extra layer of security to banking transactions.
- Utilize advanced threat detection and monitoring tools to proactively identify and respond to suspicious activities or anomalies indicative of mobile banking.
- Adopt secure coding practices and conduct regular security assessments and code reviews to identify and remediate vulnerabilities in mobile banking applications.
- Educate users about the risks associated with mobile banking trojans including phishing scams, social engineering tactics, and suspicious app downloads.
- Establish partnerships with other financial institutions, cybersecurity firms, and law enforcement agencies to share threat intelligence and collaborate on the detection and mitigation of mobile banking trojan campaigns.
- Adhere to industry regulations and compliance standards governing data protection, privacy, and financial transactions.
- Deploy advanced security technologies such as endpoint detection and response (EDR) solutions, network intrusion detection systems (NIDS), and machine learning-based anomaly detection tools, to detect and prevent mobile banking trojan infections.

