Severity
High
Analysis Summary
Security researchers have discovered a malware campaign targeting developers who write Solidity code on Windows using Visual Studio Code (VS Code). The attackers, identified as threat group MUT-9332, uploaded fake VS Code extensions that looked legitimate but secretly infected users’ systems.
These malicious extensions were named solaibot, among-eth, and blankebesxstnion. They claimed to help with Solidity syntax checking or vulnerability scanning, but once installed, they executed hidden malicious code. This triggered a step-by-step infection process that downloaded harmful files onto the victim’s system.
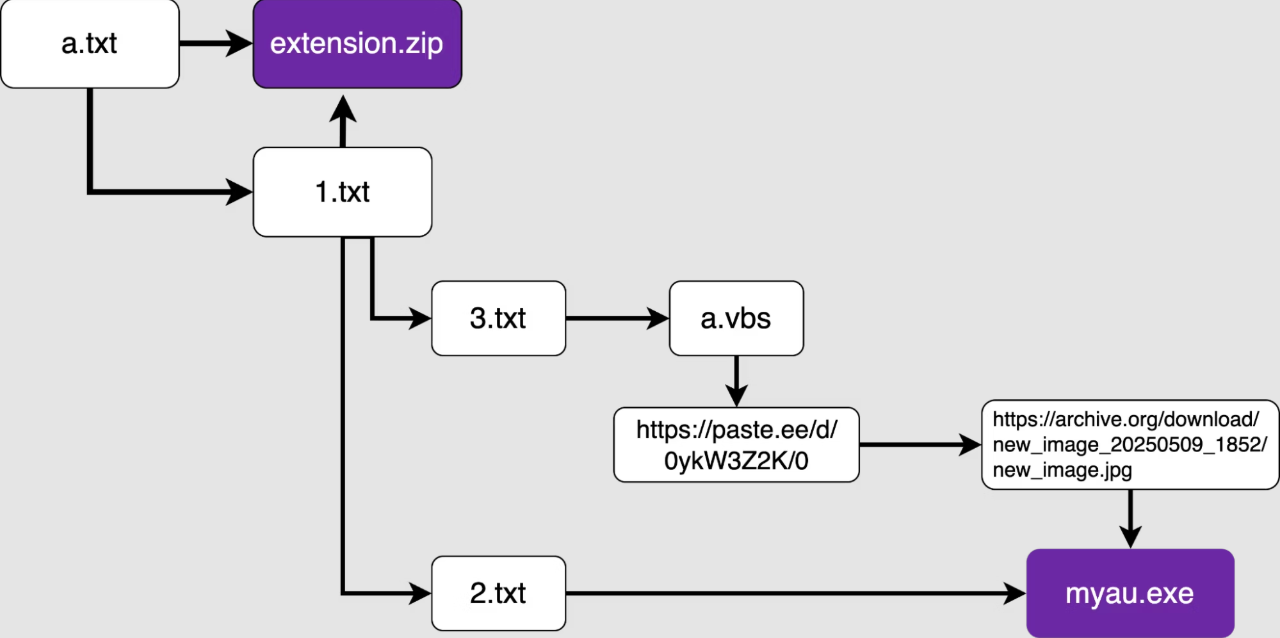
The first step involved a PowerShell command that downloaded two main payloads: a browser extension and an executable file named myau.exe. These were designed to steal sensitive data, especially cryptocurrency wallet credentials, and to keep the malware active even after reboots.
This attack is a strong reminder that even trusted platforms like the VS Code Marketplace can be misused by attackers. Developers often install extensions to boost productivity, but these tools can silently turn into serious threats if not properly reviewed. Once infected, attackers can spy on your activity, steal sensitive files, and gain control over your development environment. This is especially dangerous for blockchain and crypto developers, where stolen credentials can result in major financial loss. Staying cautious and security-aware is essential even during routine coding work.
The malware used advanced evasion techniques. It disabled Windows Defender, added firewall rules to block Microsoft’s security services, and even crashed the system if someone tried to stop it. One payload was hidden inside an image file to bypass detection. The final stage of the attack involved a tool that stole information from apps like Chrome, Brave, Discord, and others.
Even though these extensions had fewer than 50 installs before Microsoft removed them, the attack shows how risky it can be to blindly trust browser-based tools and extensions in developer environments.
Impact
- Data Theft
- Financial Loss
Indicators of Compromise
Domain Name
- solidity.bot
MD5
3fcf6a47d9fa4b252898a0afbfbb57a8
c3c7178b225242af3978c4aa2acac19c
c514e59054f1eb03290e7a44f21e4016
SHA-256
c5c0228a1e0ba2bb748219325f66acf17078a26165b45728d8e98150377aa068
a1eadd41327bd8736e275627d3953944fe7089c032d72a3e429ff18ad0958ada
c3684164933c3f54d5b0b242a8a906a85d633de479079a820bb804c0f73c0f58
SHA1
1778838e8a209a9ec0b7eeeb34991f362c557bf7
5243c5afea7b7c4609846f0ce4d417ba641e65a2
e161c437495f39185d2c4444a218c335255f5618
URL
- https://m-vn.ws/bird.php
- https://myaunet.su
- http://paste.ee/d/0ykW3Z2K/0
- https://archive.org/download/new_image_20250509_1852/new_image.jpg
- https://begalinokotobananinotrippitroppacrocofanclub.su/m
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Uninstall any of these extensions if installed: solaibot, among-eth, blankebesxstnion
- Run a full antivirus scan and check for suspicious processes like myau.exe or myaunet.exe
- Re-enable Windows Defender if disabled
- Check your browser for unknown extensions and remove them
- Change passwords for crypto wallets, developer tools, and any linked accounts
- Download VS Code extensions only from trusted authors with verified profiles
- Use endpoint protection that monitors script and PowerShell abuse

