Severity
High
Analysis Summary
The government, manufacturing, transportation, and law enforcement sectors in the United States have been the focus of ransomware attacks by the threat actor Storm-0501.
According to Microsoft, the multi-stage attack campaign aims to penetrate hybrid cloud systems and carry out lateral movement from on-premises to cloud settings. This might lead to ransomware deployment, data exfiltration, credential theft, manipulation, and persistent backdoor access. Storm-0501 is a financially driven cybercrime group that operates ransomware using open-source and commodity tools.
The threat actor, active since 2021, previously used Sabbath (54bb47h) ransomware to target educational institutions. Later, the actor became an affiliate of ransomware-as-a-service (RaaS) and began distributing different ransomware payloads, such as Embargo, BlackCat (ALPHV), Hive, Hunters International, and LockBit. The use of overly privileged accounts and weak credentials to transfer from on-premises organization infrastructure to cloud infrastructure is a noteworthy feature of Storm-0501's attacks.
Additional initial access techniques involve leveraging a footing that has already been established by access brokers such as Storm-0249 and Storm-0900, or leveraging multiple known vulnerabilities related to remote code execution in unpatched internet-facing servers including Adobe ColdFusion 2016, Citrix NetScaler, and Zoho ManageEngine.
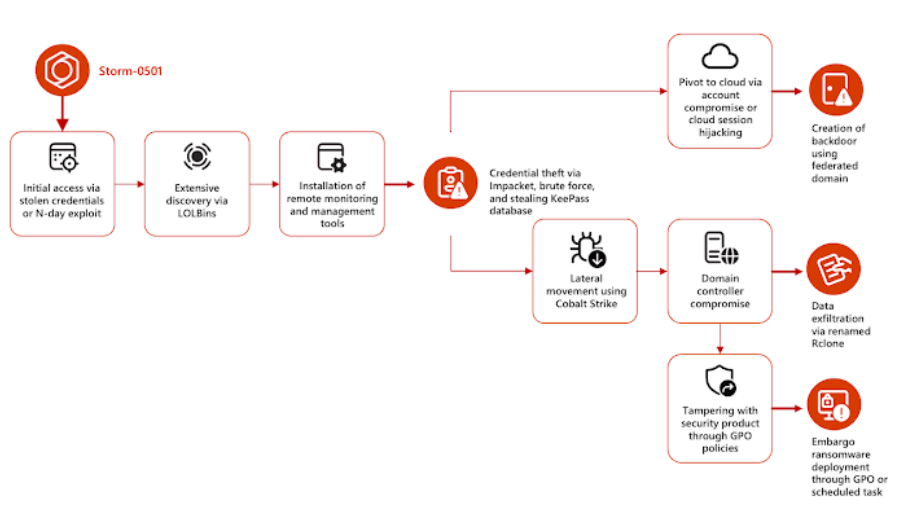
Any of the previously listed methods that provide access open the door for thorough discovery operations that identify high-value assets, collect domain data and carry out Active Directory reconnaissance. Remote monitoring and management solutions (RMMs) like AnyDesk are then deployed to ensure permanence.
Using the administrator capabilities on the machines it had initially infiltrated, the threat actor tried several approaches to obtain access to additional accounts on the network. To obtain credentials, the threat actor mostly used Impacket's SecretsDump module, which extracts credentials over the network and leverages it across a large number of devices. The threat actor simultaneously accesses sensitive files to extract KeePass secrets and uses brute-force attacks to gain credentials for specific accounts. The compromised credentials are then used to access even more devices and retrieve more credentials.
Microsoft reported that it discovered Storm-0501, which was using Cobalt Strike to deliver orders and move laterally across the network while using credentials that had been compromised. Rclone is used to move data from the on-premises environment to the MegaSync public cloud storage service to exfiltrate the data. After Octo Tempest and Manatee Tempest, this threat actor is the most recent to target hybrid cloud settings. It has also been seen to create persistent backdoor access to the cloud environment and to transmit ransomware to the on-premises.
The threat actor moved laterally from the on-premises to the cloud environment and established persistent access to the target network through a backdoor by using the credentials—specifically, Microsoft Entra ID (previously Azure AD)—that were taken earlier in the attack. It is said that either a hacked Microsoft Entra Connect Sync user account or the cloud session hijacking of an on-premises user account with an associated admin account in the cloud that has multi-factor authentication (MFA) turned off allowing the pivot to the cloud.
The attack culminates in the exfiltration of files of interest, lateral migration to the cloud, and deployment of Embargo ransomware throughout the victim company after gaining adequate control over the network. First identified in May 2024, Embargo is a ransomware that is based on Rust. The ransomware gang behind Embargo uses the RaaS model, allowing affiliates like Storm-0501 to utilize its platform to launch attacks in exchange for a portion of the payment.
Embargo affiliates use double extortion, in which they encrypt the files of their victims and then threaten to release important information that has been taken unless a ransom is paid. Nevertheless, data acquired by the manufacturer of Windows indicates that the threat actor does not constantly use ransomware dissemination, choosing instead to occasionally keep network access through a backdoor.
Impact
- Data Exfiltration
- Credential Theft
- File Manipulation
- Unauthorized Access
Indicators of Compromise
MD5
- 92d0125f2b4187680e5fcc2c4423045b
SHA-256
- caa21a8f13a0b77ff5808ad7725ff3af9b74ce5b67426c84538b8fa43820a031
SHA-1
- 031491d3fab8d79a78a0b89c4267b9658e86f1ff
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Implement robust multi-layered security measures to detect and respond to ransomware and cyber espionage activities.
- Conduct regular security assessments and penetration testing to identify and mitigate vulnerabilities in critical infrastructure and government systems.
- Deploy advanced threat detection tools, such as Endpoint Detection and Response (EDR) and Network Traffic Analysis (NTA), to monitor for suspicious activities and anomalies.
- Ensure timely patching and updating of all software and systems to close known security gaps.
- Use multi-factor authentication (MFA) and strong password policies to protect user accounts from unauthorized access.
- Segment networks to limit lateral movement within the organization in case of a breach.
- Develop and maintain an incident response plan that includes procedures for ransomware attacks and data breaches.
- Train employees on cybersecurity best practices and phishing awareness to reduce the risk of social engineering attacks.
- Regularly back up critical data and ensure backups are stored securely and are not accessible from the primary network.
- Collaborate with cybersecurity firms and government agencies for threat intelligence sharing and coordinated defense strategies.
- Implement encryption for sensitive data at rest and in transit to protect against data theft.
- Limit access to critical systems and data to only those individuals who require it for their role.
- Monitor for and immediately investigate the presence of known malware and indicators of compromise associated with state-sponsored groups.
- Engage in regular cybersecurity drills and exercises to ensure readiness for potential cyber incidents.
- Ensure legal and compliance measures are in place, particularly for industries subject to specific regulatory requirements.

