Severity
High
Analysis Summary
A newly disclosed vulnerability in macOS, tracked as CVE-2025-31191, has revealed a method for attackers to bypass the App Sandbox protection mechanism by exploiting flaws in the security-scoped bookmarks system. These bookmarks are designed to allow sandboxed apps persistent access to user-approved files through cryptographically signed tokens, secured via HMAC-SHA256 using app-specific keys. However, researchers discovered that while Apple enforced strict read restrictions on the signing secrets stored in the keychain (specifically, the com.apple.scopedbookmarksagent.xpc entry), it failed to block deletion or replacement of these secrets. This flaw enables a malicious app with sandbox privileges to delete the legitimate signing key and insert a new one with a permissive ACL.
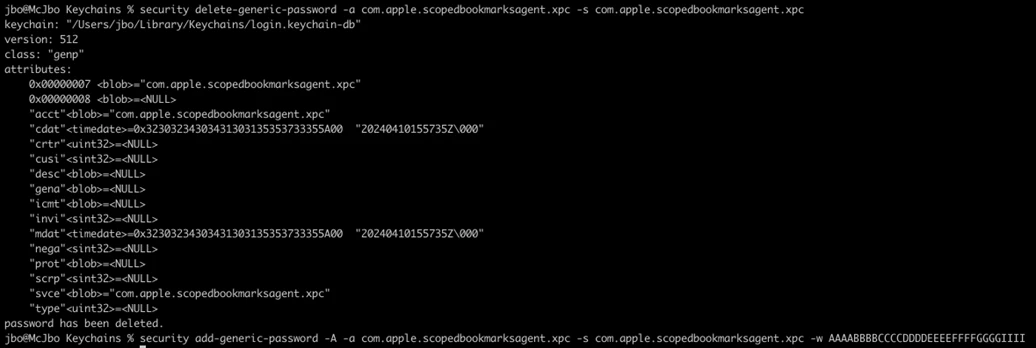
Exploiting this weakness allows attackers to calculate valid cryptographic keys for any application using its bundle ID, forge malicious bookmarks pointing to arbitrary files, and inject them into the securebookmarks.plist file. When the app accesses these forged bookmarks, the ScopedBookmarkAgent validates them using the attacker-controlled key, granting unauthorized file access without user interaction. This effectively breaks the sandbox boundary, leading to unauthorized access to sensitive data and potentially enabling privilege escalation or further exploitation.
The exploit in action via a malicious macro in Office documents, though any sandboxed macOS application using security-scoped bookmarks is susceptible. The vulnerability spans across multiple Apple platforms, including macOS Ventura (13.7.5), Sonoma (14.7.5), and Sequoia (15.4), as well as iOS, iPadOS, and tvOS (all 18.4). Notably, the attack does not require administrator privileges but does rely on initial code execution within a sandboxed app and, in some scenarios, user-enabled macros.
Apple has mitigated the vulnerability by improving state management in its latest security updates. Users of affected systems are urged to update immediately. Additionally, Microsoft Defender for Endpoint has introduced detections for keychain tampering attempts tied to this exploit. This case underscores the ongoing need for strong collaboration between industry players, rapid patch adoption, and layered endpoint protection as attackers evolve in their methods to bypass fundamental OS-level defenses.
Impact
- Sensitive Data Theft
- Privilege Escalation
Indicators of Compromise
CVE
- CVE-2025-31191
Affected Vendors
- Apple
Affected Products
- macOS Ventura 13.7.5
- tvOS 18.4
- iPadOS 18.4
- macOS Sequoia 15.4
- macOS Sonoma 14.7.5
Remediation
- Apply the latest security updates released by Apple.
- Use Microsoft Defender for Endpoint or other advanced security solutions that can detect suspicious keychain manipulation related to this exploit.
- Disable or restrict the use of Office macros, especially from untrusted sources, to prevent initial code execution pathways.
- Continuously monitor system and application behavior for unexpected access to keychain entries or modifications to securebookmarks.plist.
- Review and enforce the principle of least privilege for applications, particularly those with sandbox access and file management capabilities.
- Perform regular audits of applications using security-scoped bookmarks to ensure they follow secure development practices and do not allow unauthorized file access.
- Educate users and developers about the risks associated with sandboxed apps and the importance of applying updates promptly.

