Severity
High
Analysis Summary
Kimsuky, also known by various aliases such as APT43, ARCHIPELAGO, and Velvet Chollima, is a North Korean threat actor known for extensively using spear phishing tactics.
Active since at least 2012, Kimsuky has established a reputation for successfully deceiving victims into downloading malware through carefully crafted phishing emails. Researchers identified two new malware strains associated with this group, KLogEXE and FPSpy. These strains add to the group's already diverse and potent malware arsenal, underscoring Kimsuky’s evolving capabilities.
KLogEXE is a C++ adaptation of a previously identified PowerShell-based keylogger called InfoKey, which was linked to Kimsuky’s campaigns targeting Japanese organizations. This malware is designed to collect and exfiltrate a wide range of information, including details about the applications running on the compromised machine, keystrokes, and mouse clicks. The shift from PowerShell to C++ in KLogEXE indicates a strategic enhancement in the group's approach potentially aimed at evading detection mechanisms that might be more familiar with the PowerShell version.
FPSpy, the second malware strain identified, appears to be a variant of a backdoor initially disclosed by researchers in 2022, with further ties to a malware known as KGH_SPY, documented in 2020. FPSpy goes beyond simple keylogging, incorporating advanced functionalities such as gathering comprehensive system information, downloading and executing additional payloads, executing arbitrary commands, and enumerating drives, folders, and files on the infected device. This sophisticated set of capabilities makes FPSpy a versatile tool in Kimsuky’s arsenal suitable for both espionage and broader cyber operations.
The discovery of KLogEXE and FPSpy not only highlights Kimsuky’s continuous evolution but also demonstrates the group's focused targeting of entities in South Korea and Japan. The similarities in the source code of these two malware strains further suggest that they are likely the work of the same author pointing to a consistent and deliberate development effort within Kimsuky’s ranks. As the group continues to refine its tactics and expand its capabilities, it poses an ongoing and significant threat to organizations within its areas of interest.
Impact
- Sensitive Data Theft
- Cyber Espionage
- Code Execution
- Data Exfiltration
- Keylogging
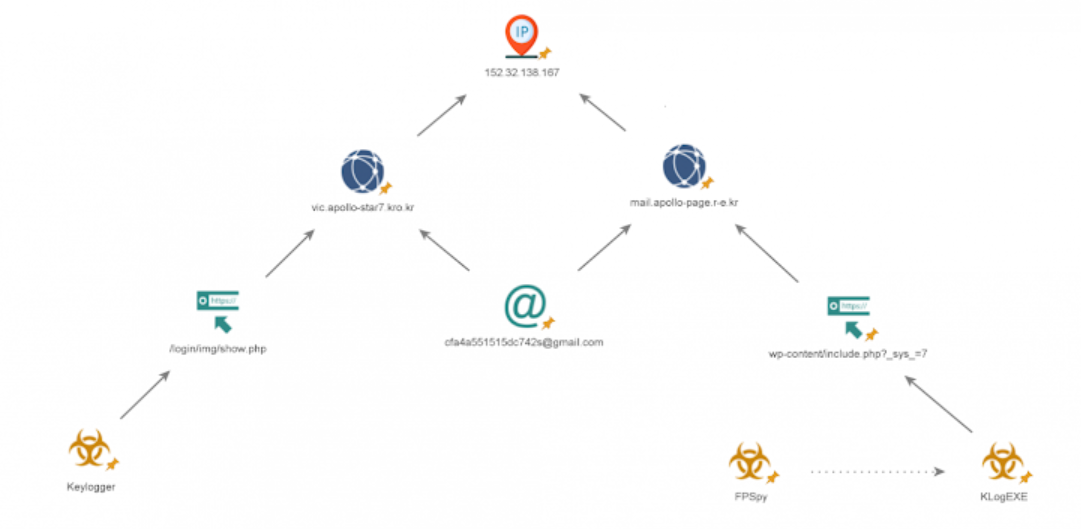
Indicators of Compromise
Domain Name
- www.vic.apollo-star7.kro.kr
- bitjoker2024.000webhostapp.com
- mail.apollo-page.r-e.kr
- nidlogin.apollo.r-e.kr
IP
- 152.32.138.167
MD5
- e1d683ee1746c08c5fff1c4c2b3b02f0
- 54c58b72f98cb63c44e7694add551e9d
- 6d6c1b175e435f5564341cc1f2c33ddf
SHA-256
- 990b7eec4e0d9a22ec0b5c82df535cf1666d9021f2e417b49dc5110a67228e27
- c69cd6a9a09405ae5a60acba2f9770c722afde952bd5a227a72393501b4f5343
- 2e768cee1c89ad5fc89be9df5061110d2a4953b336309014e0593eb65c75e715
SHA-1
- 65a76ccf28a6c9593683a874df1c9bca514fb9c4
- 35bfaab9d1811f8b6f3126caced09e77fdfafdb9
- a5d5263546cd2d67eb7941154cc24e6c64e78599
URL
- http://mail.apollo-page.r-e.kr/wp-content/include.php?_sys_=7
- http://mail.apollo-page.r-e.kr/plugin/include.php?_sys_=7
- http://nidlogin.apollo.r-e.kr/cmd/index.php?_idx_=7
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Ensure all operating systems and software are up to date with the latest security patches.
- Employ reliable antivirus and antimalware software to detect and block known threats.
- Regularly update these tools to maintain the latest threat intelligence.
- Implement IDPS to detect and prevent unusual network activity, system behavior, or similar threats.
- Enable two-factor authentication (2FA) on your accounts adds an extra layer of security and can help prevent unauthorized access even if your login credentials have been stolen.
- Regularly backing up your important data can help ensure that you don’t lose any critical information in the event of a malware infection or other data loss event.
- Be wary of emails, attachments, and links from unknown sources. Also, avoid downloading software from untrusted sources or clicking on suspicious ads or pop-ups.
- Use email filtering solutions to block malicious attachments and links that may deliver malware to users via phishing emails.
- Segment your network to limit lateral movement for attackers.
- Employ application whitelisting to only allow approved software to run on systems, reducing the risk of unauthorized applications being executed.
- Implement robust monitoring solutions to detect any unusual or suspicious activities, such as unauthorized access attempts or data exfiltration. Establish an effective incident response plan to respond to and mitigate any potential breaches quickly.
- Make sure all of your software, including your operating system and applications, is up-to-date with the latest security patches. This can help prevent vulnerabilities that info-stealers and other types of malware could exploit.

