Severity
High
Analysis Summary
The North Korean Kimsuky threat actors are reportedly launching attacks on Japanese organizations, according to Japan's Computer Emergency Response Team Coordination Center (JPCERT/CC).
Kimsuky has been identified by the US government as a North Korean advanced persistent threat (APT) group that launches attacks against targets all over the world to obtain intelligence on subjects that are of relevance to the North Korean leadership. It is well known that the threat actors utilize phishing and social engineering to get first access to networks. After that, they use specially designed malware to steal information and stay persistent on networks.
According to JPCERT, attribution of the Kimsuky attacks was made earlier this year based on indications of compromise (IOCs) disclosed by researchers in two different publications. To begin their attack, the threat actors pose as security and diplomatic organizations in phishing emails that they send to targets in Japan along with a malicious ZIP attachment.
The ZIP file includes two bogus document files and an executable that can infect a system with malware. The ".exe" portion of the executable filename is hidden by the numerous spaces it employs to appear as a document. The payload downloads and runs a VBS file when it is executed by the victim. It also sets up 'C:\Users\Public\Pictures\desktop.ini.bak' to launch automatically using Wscript.
To gather data, including process lists, network information, file lists from folders (Downloads, Documents, Desktop), and user account information, the VBS file downloads a PowerShell script. After that, the attackers control a remote URL to which this data is transferred. Kimsuky uses the information gathered to assess if the compromised device is an analysis environment or a genuine user computer.
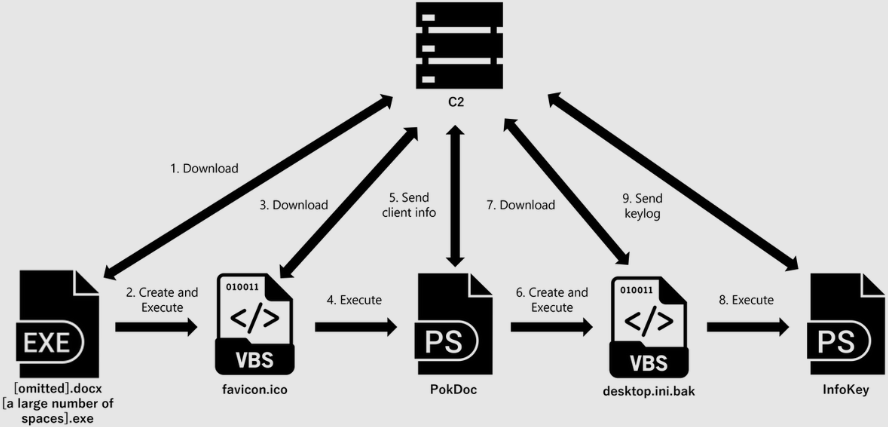
Ultimately, a new VBS file is made and used to download a PowerShell script that records clipboard data and keystrokes and sends it to the attackers. Credentials that would enable threat actors to access more systems and apps within the company could be among the data gathered by the keylogger.
Kimsuky was found by researchers to be disseminating a CHM malware variant in Korea in May 2024. OneNote, DOC, and LNK were among the earlier formats in which the malware was disseminated. A malicious script is launched in the background while a Compiled HTML Help (CHM) file that shows a help screen is executed. This is how the attack is carried out.
A file in the user's profile path is created and executed by this script. After that, the file establishes a connection with an external URL to run more malicious Base64-encoded scripts. These scripts are in charge of keylogging, producing and registering a malicious script as a service, and exfiltrating user data.
The most recent malware samples that analysts have examined use more advanced obfuscation to avoid detection when compared to previous versions. Japan's CERT emphasizes the necessity for enterprises to exercise caution when dealing with CHM files that may include executable scripts intended to spread malware, in light of the detected Kimsuky activity in that nation.
Impact
- Cyber Espionage
- Sensitive Data Theft
- Keylogging
- Credential Theft
Remediation
- Ensure all operating systems and software are up to date with the latest security patches.
- Employ reliable antivirus and antimalware software to detect and block known threats.
- Regularly update these tools to maintain the latest threat intelligence.
- Implement IDPS to detect and prevent unusual network activity, system behavior, or similar threats.
- Enabling two-factor authentication (2FA) on your accounts adds an extra layer of security and can help prevent unauthorized access even if your login credentials have been stolen.
- Regularly backing up your important data can help ensure that you don’t lose any critical information in the event of a malware infection or other data loss event.
- Be wary of emails, attachments, and links from unknown sources. Also, avoid downloading software from untrusted sources or clicking on suspicious ads or pop-ups.
- Use email filtering solutions to block malicious attachments and links that may deliver malware to users via phishing emails.
- Segment your network to limit lateral movement for attackers.
- Employ application whitelisting to only allow approved software to run on systems, reducing the risk of unauthorized applications being executed.
- Implement robust monitoring solutions to detect any unusual or suspicious activities, such as unauthorized access attempts or data exfiltration. Establish an effective incident response plan to respond to and mitigate any potential breaches quickly.
- Make sure all of your software, including your operating system and applications, is up-to-date with the latest security patches. This can help prevent vulnerabilities that info-stealers and other types of malware could exploit.

