Severity
High
Analysis Summary
A newly identified spear-phishing campaign attributed to Iranian-aligned actors, specifically the Homeland Justice group linked to Iran’s Ministry of Intelligence and Security (MOIS), has been observed targeting diplomatic missions worldwide. First detected in August 2025, the operation leveraged a compromised Ministry of Foreign Affairs of Oman mailbox (@fm.gov.om), allowing attackers to send malicious emails that appeared highly credible. These emails, routed through a NordVPN exit node in Jordan (212.32.83.11) to obscure attribution, were sent to more than 270 recipients across embassies, consulates, and international organizations. Subjects such as “The Future of the region after the Iran-Israel war and the role of Arab countries in the Middle East” were used to enhance the social engineering lure.
Analysis by the Researcher revealed that the scope of the campaign was far broader than initially assessed, involving 104 unique compromised accounts to mask its true origin. The attackers distributed Microsoft Word documents embedded with macros that executed sophisticated payload delivery techniques. These malicious files were crafted to resemble urgent diplomatic communications, significantly increasing the likelihood of success. The macros were hidden within “This Document” and “UserForm1” modules, showcasing advanced obfuscation and encoding methods designed to bypass detection.
The VBA macro execution chain featured a primary decoder function named “dddd,” which processed encoded strings by converting three-digit numerical sequences into ASCII characters. Additionally, the attackers employed a unique anti-analysis evasion technique through the “laylay” function, which introduced artificial delays using nested loops of 10⁵ iterations. This significantly hindered automated sandbox environments and dynamic malware analysis, allowing the payload to execute with reduced risk of early detection. The decoded payload was written to C:\Users\Public\Documents\ManagerProc[.]log, masquerading as a benign log file before execution using the Shell command with stealth parameters.
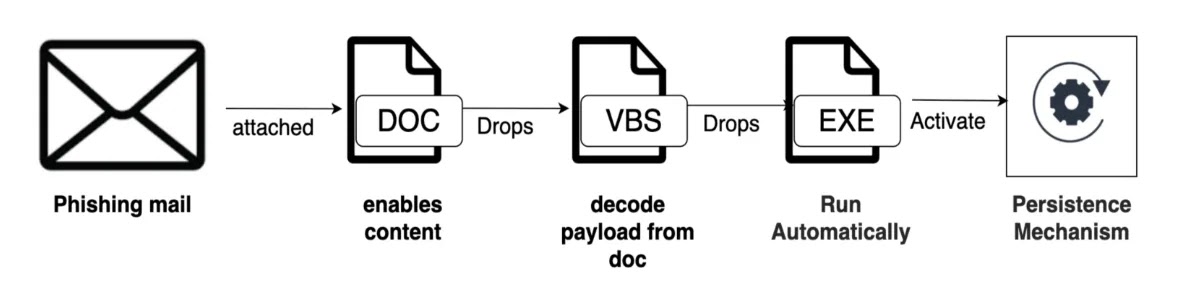
Once executed, the malware identified as sysProcUpdate.exe established persistence by copying itself into C:\ProgramData\sysProcUpdate[.]exe and altering Windows registry DNS parameters. It then initiated system reconnaissance, gathering metadata such as username, computer name, and administrative privileges. This information was exfiltrated over encrypted HTTPS POST requests to the command-and-control server at screenai.online/Home/. The campaign’s blend of social engineering, compromised government infrastructure, advanced encoding, and stealthy persistence mechanisms highlights the technical sophistication and geopolitical focus of Iranian-aligned cyber operations targeting global diplomatic channels.
Impact
- Gain Access
- Security Bypass
Indicators of Compromise
Domain Name
screenai.online
MD5
3ab16bd1c339fd0727be650104b74dd1
1de19958e7c2ef14addfb35b43a594ec
3bb65d389d5c535f068328e607d2d688
7e73ca410dc6480c77a9236c0733c0a1
78b778ba0bcd546337077a50b8f90532
SHA-256
b2c52fde1301a3624a9ceb995f2de4112d57fcbc6a4695799aec15af4fa0a122
1c16b271c0c4e277eb3d1a7795d4746ce80152f04827a4f3c5798aaf4d51f6a1
f0ba41ce46e566f83db1ba3fc762fd9b394d12a01a9cef4ac279135e4c1c67a9
76fa8dca768b64aefedd85f7d0a33c2693b94bdb55f40ced7830561e48e39c75
3d6f69cc0330b302ddf4701bbc956b8fca683d1c1b3146768dcbce4a1a3932ca
SHA1
2b5ddc48fe17d014e38b9fd6646b23d5eb70b471
ec251c5b831be6265d8daeb0437229b8b00e0b68
290ab496ab0a66e16f0558d621a52cacd5c66392
29f86bc6921b56ea178c8f2b06f136b3b1fc80a6
f326bb96544e1b0c9df9bdc496c417dcf5760067
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Enforce multi-factor authentication (MFA) on all government and diplomatic email accounts to reduce the risk of mailbox compromise.
- Configure email security gateways to block or quarantine messages containing macros, suspicious attachments, or originating from VPN/proxy services.
- Apply macro restrictions in Microsoft Office, disabling automatic execution of VBA code unless explicitly approved.
- Implement endpoint detection and response (EDR) tools with behavioral monitoring to detect suspicious script execution, registry changes, and persistence attempts.
- Regularly patch operating systems and Office applications to close vulnerabilities exploited by macro-based malware.
- Conduct security awareness training for diplomats and staff to recognize phishing lures, especially those imitating urgent diplomatic communications.
- Monitor network traffic for anomalies, including outbound HTTPS POST requests to suspicious or newly registered domains (e.g., screenai.online).

