Severity
High
Analysis Summary
Cybersecurity researchers have discovered a highly sophisticated web shell attack targeting Microsoft Internet Information Services (IIS) servers, granting threat actors full remote control over compromised systems. Identified as “UpdateChecker.aspx,” this malicious script represents a significant advancement in web shell complexity. Unlike traditional PHP or ASP scripts, it employs heavily obfuscated C# code embedded within an ASPX page, using techniques such as Unicode encoding, randomly generated identifiers, and encrypted constants to evade detection and hinder analysis.
The web shell emerged during an investigation into cyberattacks targeting critical infrastructure in the Middle East, where multiple IIS servers were found compromised. The malware’s architecture is modular, comprising three core components: Base for system reconnaissance, CommandShell for executing Windows commands with IIS-level privileges, and FileManager for full control over the file system.
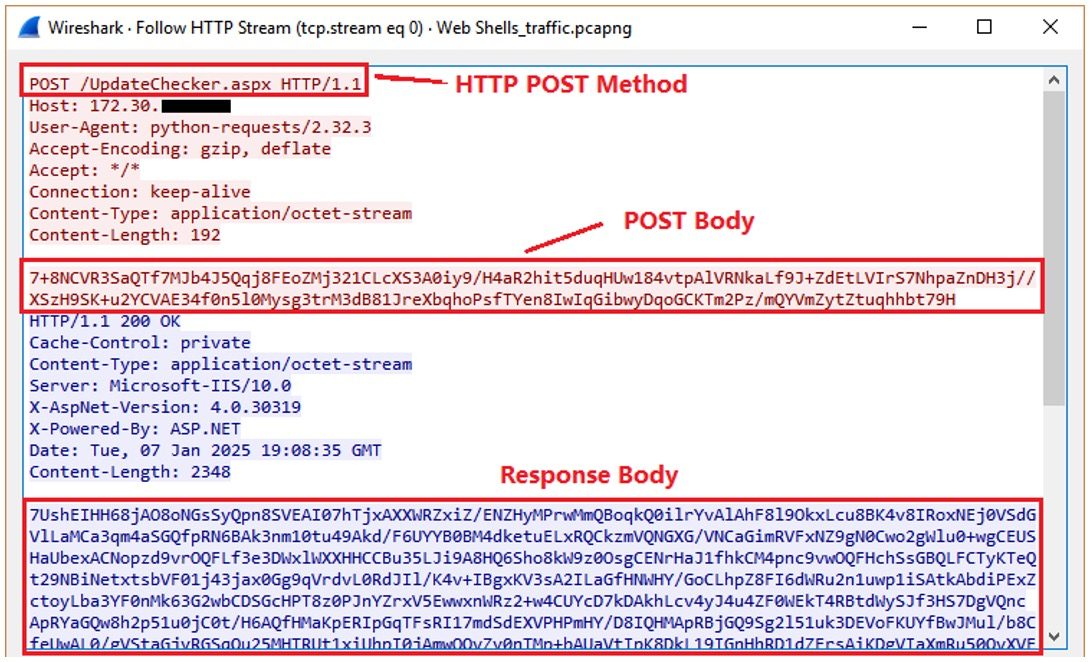
It communicates via HTTP POST requests, using the "application/octet-stream" content type, and transmits commands in a structured JSON format with fields such as ProtocolVersion, ModuleName, and RequestName, along with parameters depending on the function. The web shell supports a wide range of capabilities including file creation, movement, deletion, directory management, command execution, and content manipulation, all disguised as regular IIS activity.
A dual-encryption mechanism enhances its stealth, with the first 16 bytes of communication containing an encrypted key based on hardcoded values, followed by command data encrypted with a derived 15-byte key. These features allow the web shell to operate covertly within enterprise environments, posing a severe threat due to its persistent access and high privilege execution. Discovered by security researchers, the malware underscores the evolving sophistication of cyber threats targeting server infrastructure, especially in regions of geopolitical interest. Its seamless integration into Windows IIS environments makes it particularly dangerous, enabling long-term persistence and deep system access for threat actors.
Impact
- System Compromise
- Defense Evasion
- Command Execution
- Data Theft
Remediation
- Regularly update and patch IIS servers to eliminate known vulnerabilities
- Monitor server logs for unusual POST requests or abnormal activity patterns
- Deploy advanced endpoint detection tools capable of detecting obfuscated scripts
- Restrict access to web server directories and enforce least privilege principles
- Implement application whitelisting to block unauthorized web shell execution
- Use network segmentation to isolate web servers from sensitive internal systems
- Conduct regular code audits on web applications hosted on IIS
- Implement strong web application firewalls (WAFs) to filter malicious traffic
- Enable multi-factor authentication for administrative access to servers
- Periodically scan servers for web shells and hidden backdoors using forensic tools
- Encrypt internal communications to prevent interception of sensitive data
- Train IT staff to recognize and respond to advanced persistent threats (APTs)

