Severity
High
Analysis Summary
The Gunra ransomware campaign, first emerging in April 2025, represents a weaponized evolution of the leaked Conti source code, delivering highly targeted double-extortion attacks on Windows systems. Unlike traditional widespread spam-based ransomware, Gunra operators prefer hands-on breaches through compromised Remote Desktop Protocol (RDP) credentials or unpatched VPN gateways. Once inside, they escalate privileges and pivot to domain controllers, deploying the ransomware through PsExec or Group Policy to dozens of machines in minutes. Victims are pressured to pay within five days under the threat of public data leaks, aligning Gunra with aggressive extortion tactics observed in advanced threat operations.
Technically, Gunra replicates Conti’s multithreaded design by dynamically spawning encryption threads that match the number of logical CPU cores, maximizing performance and minimizing detection time. For each thread, an RSA-2048 key is generated to derive a ChaCha20 session key used to encrypt files in 5 MB chunks. Files are appended with the “.ENCRT” extension, while the malware deliberately avoids encrypting critical executable, driver, or system files to maintain system stability. This ensures that ransom notes labeled “R3ADM3.txt” can still be accessed in every affected directory, guiding victims toward the ransom payment process.
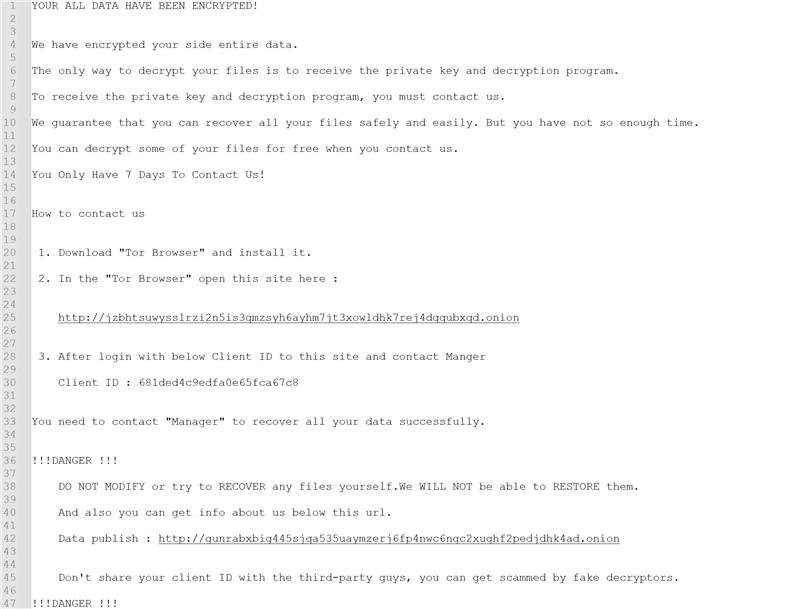
A defining feature of Gunra’s execution chain is its stealth and speed. Upon launch, the malware creates a unique mutex and gathers system architecture information to calculate thread allocation. All encryption routines remain memory-resident and avoid external communication, making the attack largely invisible to perimeter-based defenses. The hard-coded RSA public key further limits network indicators of compromise, highlighting Gunra’s design for quiet, swift, and devastating execution.
As a final blow, Gunra surgically deletes Windows Volume Shadow Copies via WMI using WMIC commands, wiping out recovery options and cementing the attack’s impact. Analysts have tracked over a dozen affected enterprises across industries like manufacturing, healthcare, and logistics within the first three months of its activity. With minimal observable network traffic, defenders must rely on behavioral detection monitoring for aggressive thread spawning and WMIC-based shadow copy deletions as key indicators of Gunra’s presence before backup systems are compromised.
Impact
- Sensitive Data Theft
- Double-Extortion
- File Encryption
- Gain Access
Indicators of Compromise
MD5
3178501218c7edaef82b73ae83cb4d91
7dd26568049fac1b87f676ecfaac9ba0
9a7c0adedc4c68760e49274700218507
SHA-256
6d25d5c988a8cda3837dff5f294cbc25c97aea48dde1a74cba71a2439cab0a11
a82e496b7b5279cb6b93393ec167dd3f50aff1557366784b25f9e51cb23689d9
854e5f77f788bbbe6e224195e115c749172cd12302afca370d4f9e3d53d005fd
SHA1
08a3b8d6f5f386a0a86ac39b5cdcc1e5dbbf42e2
bb79502d301ba77745b7dbc5df4269fc7b074cda
77b294117cb818df701f03dc8be39ed9a361a038
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Disable RDP if not needed and enforce strong passwords with multi-factor authentication (MFA) for remote access.
- Regularly patch VPN gateways, firewalls, and public-facing services to close known vulnerabilities.
- Segment the network to limit lateral movement and apply least privilege access controls to sensitive systems.
- Monitor for unusual CPU activity, excessive thread spawning, or abnormal WMIC usage indicating ransomware behavior.
- Restrict or closely monitor the use of administrative tools like PsExec and Group Policy scripts.
- Maintain secure, offline, and immutable backups, and routinely test backup restoration procedures.
- Deploy endpoint detection and response (EDR/XDR) tools that can detect in-memory and behavior-based threats.
- Log and analyze all WMIC command usage, especially those targeting shadow copy deletion.
- Conduct regular employee awareness training on phishing and credential theft techniques.
- Schedule periodic security audits and penetration testing to identify and fix exploitable weaknesses.

