

North Korean APT Kimsuky aka Black Banshee – Active IOCs
April 18, 2025
Mirai Botnet aka Katana – Active IOCs
April 19, 2025
North Korean APT Kimsuky aka Black Banshee – Active IOCs
April 18, 2025
Mirai Botnet aka Katana – Active IOCs
April 19, 2025Severity
High
Analysis Summary
A new hacker group named CrazyHunter is targeting organizations in Taiwan, especially in healthcare, education, and industry. They use free tools from GitHub to carry out their attacks, making it easier and cheaper for them to operate.
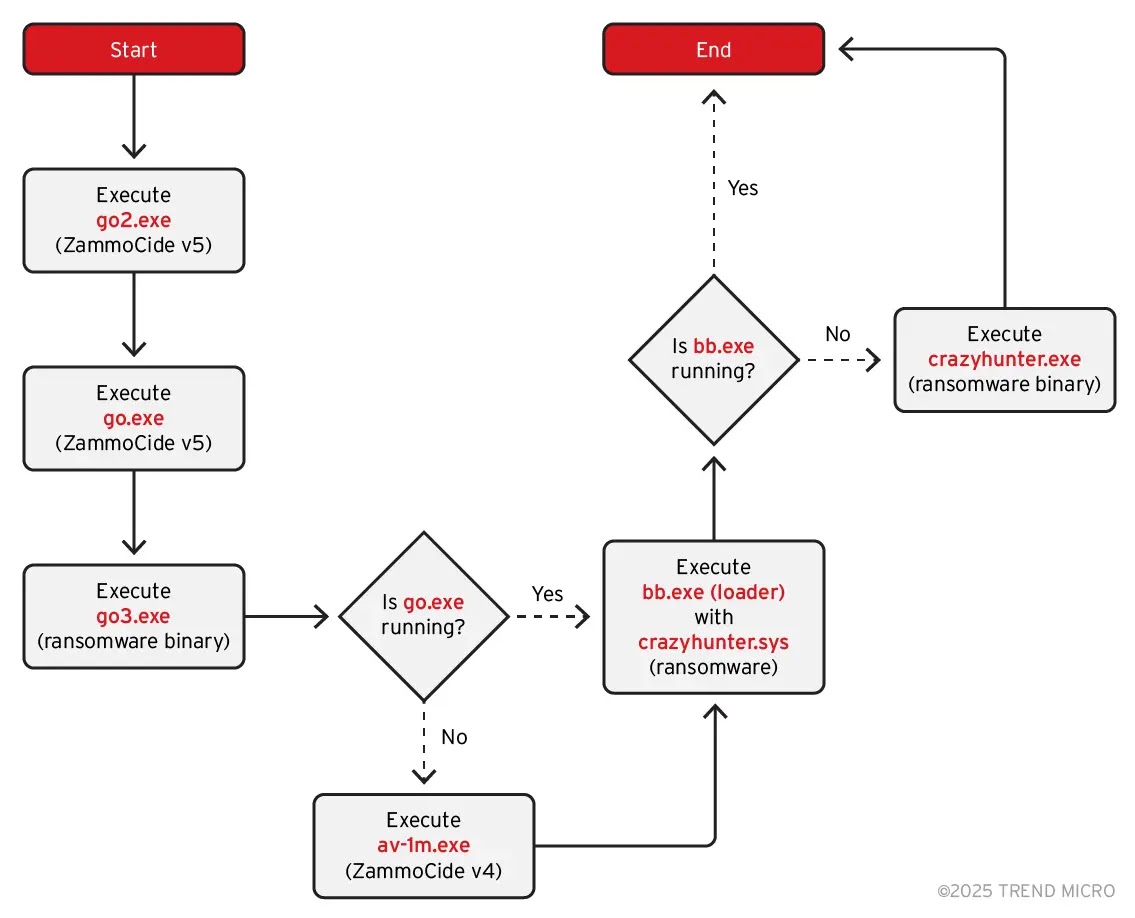
One of their main tactics is using a method called "Bring Your Own Vulnerable Driver" (BYOVD). This involves exploiting weak drivers already present in systems to disable security software. For instance, they use a tool called ZammoCide to stop antivirus programs, allowing their ransomware to run without being detected.
Their ransomware, built using the Prince Ransomware Builder, encrypts files and adds a ".Hunter" extension. Victims receive a ransom note titled "Decryption Instructions.txt" and see their desktop wallpaper changed with ransom demands.
CrazyHunter's attack process is thorough. They use batch scripts to run multiple programs in sequence, ensuring the ransomware is deployed even if some steps fail. They also employ tools like SharpGPOAbuse to move through networks and gain higher access rights.
Their operations are focused on Taiwan, with evidence pointing to deliberate targeting of the region. For example, their ransom notes include email addresses with "tw" in them, indicating a focus on Taiwanese victims.
This group represents a growing threat, combining freely available tools with advanced techniques to disrupt critical services.
Impact
- Gain Access
- Privilege Escalation
- Financial Loss
Indicators of Compromise
MD5
- 9fe3322dd4fc35d1ed510bf715dae814
- 88f8ba23ccafdac9cf5f8d9e9210a713
- 906e89f6eb39919c6d12a660b68ae81f
- b7a812586c037ca8d41968842a211b8a
- ca257aaa1ded22ca22086b9e95cb456d
- da1a93627cec6665ae28baaf23ff27c5
- 6a70c22a5778eaa433b6ce44513068da
- 9e45ab7d2d942a575b2f902cccfb3839
- f45cc69f74f75a707a02d26ccd912845
SHA-256
- 2cc975fdb21f6dd20775aa52c7b3db6866c50761e22338b08ffc7f7748b2acaa
- 918e2f2e3d7db628fb34b627d3c03fc95a720f578d09f265cbbc1f492a24df94
- 5316060745271723c9934047155dae95a3920cb6343ca08c93531e1c235861ba
- 14359f54d49799c713c2a8cc0c19a88392a0c6ad2c383494023008326cd0ba15
- 754d5c0c494099b72c050e745dde45ee4f6195c1f559a0f3a0fddba353004db6
- 983f5346756d61fec35df3e6e773ff43973eb96aabaa8094dcbfb5ca17821c81
- f72c03d37db77e8c6959b293ce81d009bf1c85f7d3bdaa4f873d3241833c146b
- 512f785d3c2a787b30fa760a153723d02090c0812d01bb519b670ecfc9780d93
- d1081c77f37d080b4e8ecf6325d79e6666572d8ac96598fe65f9630dda6ec1ec
SHA1
- 0937377d1ef1d47a04f1e55d929fe79c313d7640
- 1b826a12a630e777aa2c3036f1159db15f2bdd66
- 15823b729ad7aad20192ebe3fc1c21ea985001d7
- 318a601a5d758dd870c38b8c4792a2c3405e6c28
- 79c3fd97d33e114f8681c565f983cd8b8f9d8d93
- b6737248f7baed88177658598002df5433155450
- bed4229e774f136e1898fad9d37bd96e9156369e
- 9e126627dff082000a830b8e2e04206ced8663ff
- 086262abb7e85c43ffb6c384966d130ca612169b
Remediation
- Regularly update all software, operating systems, and drivers to patch known vulnerabilities.
- Implement endpoint detection and response (EDR) solutions to monitor and block malicious activities.
- Restrict user privileges by enforcing the principle of least privilege to minimize potential attack vectors.
- Conduct regular audits of installed drivers to identify and remove vulnerable or unnecessary ones.
- Disable or limit the use of Remote Desktop Protocol (RDP) and other remote access tools unless necessary.
- Employ multi-factor authentication (MFA) across all user accounts to enhance security.
- Monitor network traffic for unusual activities, such as unauthorized lateral movements or data exfiltration attempts.
- Educate employees about phishing attacks and social engineering tactics to reduce the risk of credential compromise.
- Maintain regular, offline backups of critical data to ensure recovery in case of ransomware attacks.
- Develop and regularly update an incident response plan to quickly address and mitigate security breaches.
- Avoid using open-source tools from unverified sources, and regularly review and vet any such tools in use.
- Implement network segmentation to contain potential breaches and prevent the spread of malware.
- Regularly review and update security policies and procedures to adapt to evolving threats.
- Engage with cybersecurity experts or services to conduct periodic security assessments and penetration testing.
- Stay informed about the latest threats and vulnerabilities by subscribing to threat intelligence feeds and security bulletins.








