Severity
High
Analysis Summary
Interlock is a relatively new ransomware operation that targets FreeBSD systems by developing an encryptor, an unconventional tactic used to attack enterprises all over the world. Since its launch at the end of September 2024, Interlock has targeted six firms and, once a ransom was not paid, published stolen data on its data leak website. Wayne County, Michigan, was among the victims of a cyberattack that occurred around the start of October.
In early October, an incident responder discovered a new backdoor used in an Interlock ransomware event, which provided some of the initial information on the ransomware campaign. A cybersecurity researcher discovered what was thought to be a Linux ELF encryptor for the Interlock operation shortly after. After testing the sample on a virtual machine, it crashed right away.
It was compiled especially for FreeBSD, as demonstrated by the strings in the executable, and the Linux "File" command further verified that it was compiled on FreeBSD 10.4. Although Linux encryptors are frequently made to target VMware ESXi servers and virtual machines, FreeBSD encryptors are uncommon. The now-defunct Hive ransomware operation, which was stopped by the FBI in 2023, is the only other ransomware organization known to have produced FreeBSD encryptors.
Researchers reported this week that they had discovered a second sample of the FreeBSD ELF encryptor as well as a sample of the Windows encryptor used by the operation. They added that as the operating system is frequently used in critical infrastructure, where attacks have the potential to cause extensive disruption, the threat actors most likely developed a FreeBSD encryptor. Because FreeBSD is commonly used in servers and other important infrastructure, Interlock targets it. Attackers can force victims to pay, demand large ransoms, and interfere with essential services.
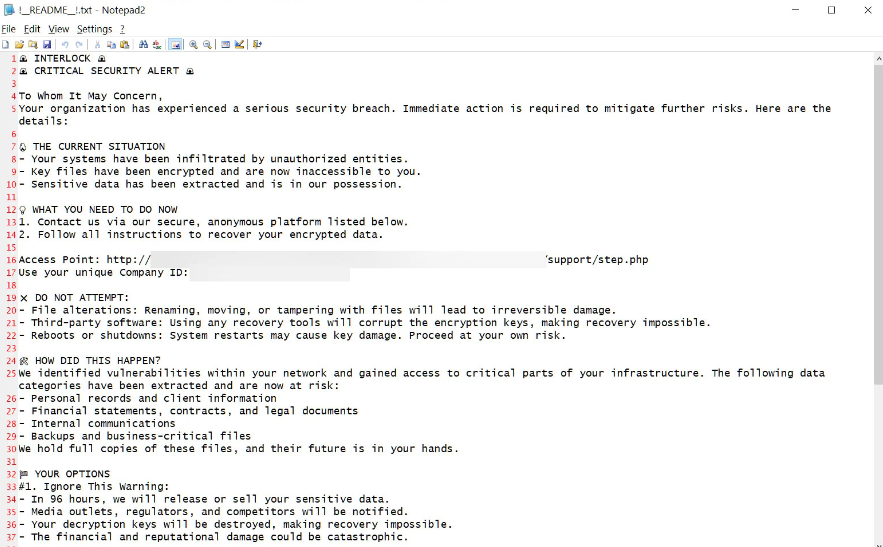
If self-deletion is enabled, the Windows encryptor will utilize a DLL to remove the main binary using rundll32.exe after clearing the Windows event logs. When files are encrypted, the ransomware will write a ransom note in each folder and add the .interlock extension to all encrypted file names. Named !__README__!.txt, this ransom letter includes links to the Tor negotiation and data leak websites, threats, and a brief description of what happened to the victim's files.
To register on the threat actor's Tor negotiation website, each victim is given a distinct "Company ID" in addition to their email address. The victim-facing negotiating site merely has a chat interface that may be used to interact with the threat actors, just like many other recent ransomware campaigns. During an attack, Interlock will infiltrate a business network, steal information from servers, and then spread to additional devices. After that, the threat actors encrypt every file on the network by deploying the ransomware.
Threat actors exploit the stolen material in a double-extortion attack, threatening to make it public if a ransom is not paid. Researchers have discovered that, depending on the size of the company, the ransomware operation seeks ransoms that range from hundreds of thousands to millions of dollars.
Impact
- File Encryption
- Financial Loss
- Sensitive Data Theft
Indicators of Compromise
MD5
- f76d907ca3817a8b2967790315265469
- e11d147dad6e47a1cecb1f2755f95a55
- f7f679420671b7e18677831d4d276277
SHA-256
- 28c3c50d115d2b8ffc7ba0a8de9572fbe307907aaae3a486aabd8c0266e9426f
- e86bb8361c436be94b0901e5b39db9b6666134f23cce1e5581421c2981405cb1
- a26f0a2da63a838161a7d335aaa5e4b314a232acc15dcabdb6f6dbec63cda642
SHA-1
- 8a38825ee33980a27ab6970e090a30a46226f752
- 5cc81e0df62e0d68710e14b31e2270f2ec7ed166
- 1cb6a93e6d2d86d3479a1ea59f7d5b258f1c5c53
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Implement robust multi-layered security measures to detect and respond to ransomware and cyber espionage activities.
- Conduct regular security assessments and penetration testing to identify and mitigate vulnerabilities in critical infrastructure and government systems.
- Deploy advanced threat detection tools, such as Endpoint Detection and Response (EDR) and Network Traffic Analysis (NTA), to monitor for suspicious activities and anomalies.
- Ensure timely patching and updating of all software and systems to close known security gaps.
- Use multi-factor authentication (MFA) and strong password policies to protect user accounts from unauthorized access.
- Segment networks to limit lateral movement within the organization in case of a breach.
- Develop and maintain an incident response plan that includes procedures for ransomware attacks and data breaches.
- Train employees on cybersecurity best practices and phishing awareness to reduce the risk of social engineering attacks.
- Regularly back up critical data and ensure backups are stored securely and are not accessible from the primary network.
- Collaborate with cybersecurity firms and government agencies for threat intelligence sharing and coordinated defense strategies.
- Implement encryption for sensitive data at rest and in transit to protect against data theft.
- Limit access to critical systems and data to only those individuals who require it for their role.
- Monitor for and immediately investigate the presence of known malware and indicators of compromise associated with state-sponsored groups.
- Engage in regular cybersecurity drills and exercises to ensure readiness for potential cyber incidents.
- Ensure legal and compliance measures are in place, particularly for industries subject to specific regulatory requirements.

