Severity
High
Analysis Summary
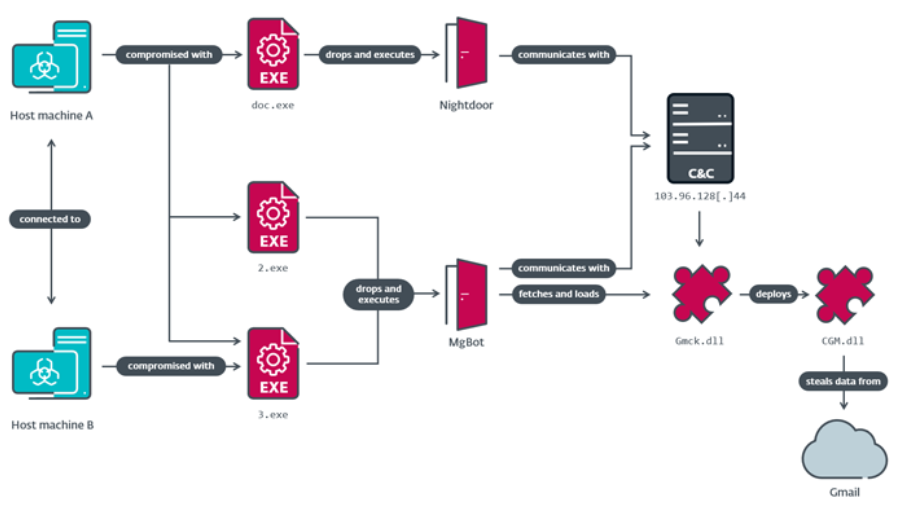
Evasive Panda, a China-affiliated threat actor, infiltrated a government agency and a religious group in Taiwan with a hitherto unreported post-compromise toolset called CloudScout. By using stolen browser session cookies, the CloudScout toolkit may retrieve data from various cloud providers. CloudScout integrates with Evasive Panda's signature malware framework, MgBot, via a plugin.
According to the researchers, the use of the .NET-based malware program was discovered between May 2022 and February 2023. It consists of ten distinct C# modules, three of which are designed to steal data from Outlook, Gmail, and Google Drive. The remaining modules' function is still unknown. The cyber espionage group Evasive Panda, also known as Bronze Highland, Daggerfly, and StormBamboo, has a history of targeting different organizations in Taiwan and Hong Kong. It is also notorious for planning supply chain and watering hole attacks on the Tibetan diaspora.
The utilization of many initial access vectors, from recently revealed vulnerabilities to supply chain compromise through DNS poisoning, to enter victim networks and install MgBot and Nightdoor distinguishes the threat actor from the others. According to cybersecurity researchers, the purpose of the CloudScout modules is to obtain unauthorized access to Google Drive, Gmail, and Outlook by stealing cookies from authenticated sessions in the web browser. A C++-programmed MgBot plugin deploys each of these modules.
The CommonUtilities package, which supplies all the low-level libraries required for the modules to function, is the foundation of CloudScout. Even though there are many comparable open-source libraries available online, CommonUtilities has a significant number of custom-implemented libraries. Compared to open-source options, these proprietary libraries offer the developers greater freedom and control over the inner workings of their implant.
For later exfiltration by MgBot or Nightdoor, the data collected by the three modules—mail folder listings, email messages (including attachments), and files with specific extensions (.doc, .docx, .xls, .xlsx, .ppt, .pptx, .pdf, and .txt)—is compressed into a ZIP archive. Nevertheless, Google's new security features, such as App-Bound Encryption and Device Bound Session Credentials (DBSC), will eventually make cookie-theft malware obsolete.
Impact
- Sensitive Data Theft
- Cyber Espionage
- Unauthorized Access
Indicators of Compromise
IP
- 103.96.128.44
MD5
- 166b0d75858ec81744921b133d72ab2d
- 624d58a9a56c0f0a5c4923557a99f808
- c643ef13ab7d1f78c8a1fba2143311c0
- 963f9805fa2867df5d3d328c863f9dfa
- c02b6a7cc4f4da2d6956049b90ff53ba
- be17d056039267973e36043c678a5d56
- 6b32494ab850f7b8e61d30085ab7dbd7
SHA-256
- b9f44273a1993d32c0dfbae59946e5e0811eb71dcb8924afbe9c5756693384db
- 6062e6f44c235bb4b0c22f6c473b2781ae381f38fcbee71e7bd51a2764875305
- 1f34527a01bd3c05affe6c90aeaea926f57efa2fac06859f8427988865ccd310
- 420700a96c1c0a136cff5445e4160b58316b5f837975bbd00f67007849af9459
- 73d50eabd0b377e22210490a06ecf2441191558d97ce14ba79517c0e7696318b
- d7468510a0123f4ecea9cb7c1636a024d3ab96cc856439a924349b00618b87ae
- 8ebce3ceaf166fe2edab157b88aa84349d2d848242ff305cdc7edb6a34e5b72f
SHA-1
- 621e2b50a979d77ba3f271fab94326cccbc009b4
- c058f9fe91293040c8b0908d3dafc80f89d2e38b
- 4a5bcdaac0bc315edd00bb1fccd1322737bcbeeb
- 67028aeb095189fdf18b2d7b775b62366ef224a9
- b3556d1052bf5432d39a6068ccf00d8c318af146
- 84f6b9f13cdcd8d9d15d5820536bc878cd89b3c8
- 93c1c8ad2af64d0e4c132f067d369ecbebae00b7
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Enable antivirus and anti-malware software and update signature definitions promptly. Using multi-layered protection is necessary to secure vulnerable assets.
- Along with network and system hardening, code hardening should be implemented within the organization so that their websites and software are secure. Use testing tools to detect any vulnerabilities in the deployed codes.
- Ensure that all software, particularly those from third-party vendors, are obtained from trusted sources and that updates are obtained from the vendor’s official website or app store.
- Conduct regular security assessments and audits of all software, especially those that handle sensitive data, to detect any suspicious activities.
- Implement multi-factor authentication and strong password policies to prevent unauthorized access to sensitive systems and data.
- Train employees on best practices for identifying and reporting suspicious activities, such as phishing emails or unusual network traffic.
- Deploy endpoint protection solutions with advanced threat detection capabilities to identify and block any malicious activities.
- Implement network segmentation and access controls to limit the spread of malware in case of a successful attack.
- Monitor network traffic and system logs to detect any unusual or suspicious activities, such as unauthorized file transfers or unusual process execution.
- Develop an incident response plan that outlines the steps to be taken in case of a successful attack, including how to isolate and contain the affected systems and how to communicate with stakeholders, such as customers and regulatory bodies.

