Severity
High
Analysis Summary
APT28, also known by various aliases including BlueDelta and Fancy Bear, is a sophisticated Russian GRU-backed threat actor known for its stealth and adaptability in cyber espionage. From April to December 2023, APT28 launched a series of campaigns targeting European networks particularly focusing on Ukraine.
The primary malware used in these attacks, HeadLace, was distributed through spear-phishing emails containing malicious links. These links initiated a multi-stage infection sequence designed to bypass security measures and implant the malware. APT28's operations demonstrate a high level of preparedness and customization, often leveraging legitimate internet services and living off-the-land binaries to blend their activities into regular network traffic thus evading detection.
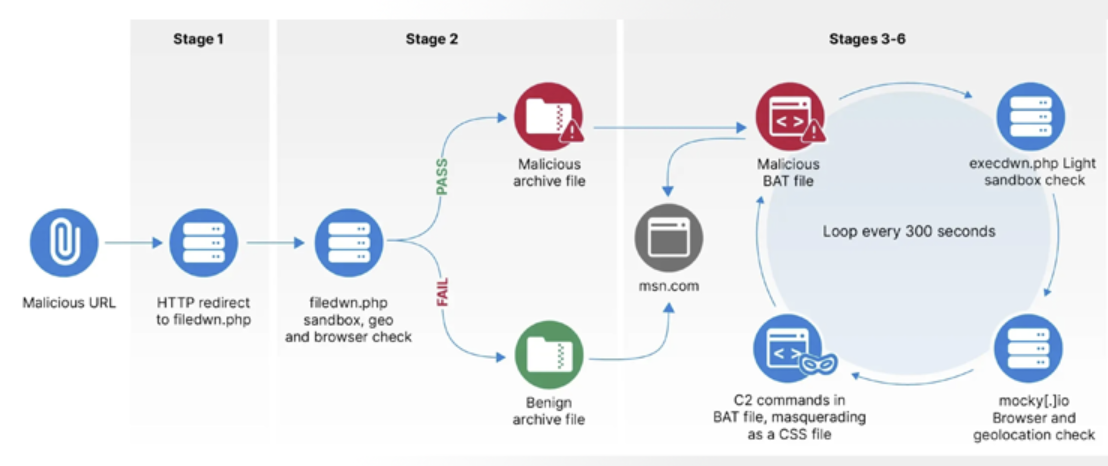
According to researchers, the deployment of HeadLace occurred in three distinct phases. The first phase involved a complex seven-stage infrastructure chain to deliver a malicious Windows BAT script capable of downloading and executing further shell commands with checks for sandbox environments and geofencing to target specific networks. The second phase which began on September 28, 2023, marked a shift to using GitHub for redirection infrastructure, and the third phase, starting October 17, 2023, moved to PHP scripts hosted on InfinityFree. The last recorded activity in this phase was in December 2023 after which APT28 transitioned to using webhook[.]site and mocky[.]io for hosting their malicious infrastructure.
In addition to malware deployment, APT28 conducted credential-harvesting operations. These operations targeted services such as Yahoo! and UKR[.]net by creating lookalike web pages to deceive users into entering their credentials. One sophisticated method involved using dedicated pages on Mocky to interact with a Python script on compromised Ubiquiti routers to exfiltrate credentials.
In February, a U.S.-led law enforcement operation disrupted a botnet of Ubiquiti EdgeRouters that APT28 had been using. The targets of these credential-harvesting activities included the Ukrainian Ministry of Defence, Ukrainian defense companies, European railway infrastructure, and a think tank in Azerbaijan reflecting APT28's strategic focus on gathering intelligence with significant military implications.
The broader strategy behind APT28's espionage activities appears to be aimed at collecting intelligence that could influence battlefield tactics and broader military strategies. Infiltrating networks associated with Ukraine's Ministry of Defence and European railway systems could provide critical insights into logistical and strategic operations. The interest in the Azerbaijan Center for Economic and Social Development suggests an agenda to understand and potentially influence regional policies highlighting the geopolitical dimensions of APT28's operations.
This wave of cyber-attacks by APT28 underscores the persistent threat posed by state-sponsored Russian cyber activities. It highlights the group's ability to evolve its tactics, techniques, and procedures to maintain operational effectiveness. Meanwhile, another Russian state-sponsored group, Turla, has also been active, using human rights seminar invitations as phishing lures to deliver a payload similar to the TinyTurla backdoor via the Microsoft Build Engine (MSBuild), illustrating the broader context of coordinated cyber operations by Russian intelligence against geopolitical adversaries.
Impact
- Credential Theft
- Cyber Espionage
- Command Execution
Indicators of Compromise
Domain Name
- robot-876.frge.io
- setnewcred.ukr.net.frge.io
- panelunregistertle-348.frge.io
- settings-panel.frge.io
- ukrprivacysite.frge.io
- smtp-relay.frge.io
- config-panel.frge.io
IP
- 85.240.182.23
- 202.175.177.238
- 24.11.70.85
- 174.53.242.108
- 68.76.150.97
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Perform comprehensive security audits on the email server infrastructure to identify and address any potential weaknesses. This includes reviewing server configurations, access controls, and encryption protocols to ensure they meet industry best practices.
- Emails from unknown senders should always be treated with caution. Never trust or open links and attachments received from unknown sources/senders.
- Enable 2FA for user accounts on the email server to add an extra layer of security. This prevents unauthorized access even if usernames and passwords are compromised.
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Implement network segmentation to isolate critical systems and sensitive data from the rest of the network. This limits the lateral movement of attackers in case of a breach and reduces the impact of potential future attacks.
- Implement a regular backup strategy for email servers and critical data. Ensure that backups are stored securely and regularly tested for data restoration.
- Apply the latest security patches and updates to the email server software and associated components to address any vulnerabilities that may have been exploited by APT28. Also, prioritize patching known exploited vulnerabilities and zero-days.

