Severity
High
Analysis Summary
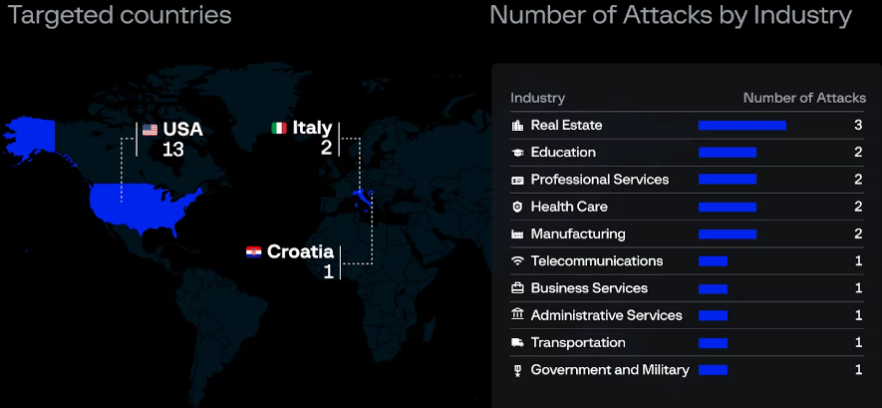
Eldorado is a brand-new ransomware-as-a-service (RaaS) that debuted in March and has Windows and VMware ESXi locker versions. The group has already claimed 16 victims in the real estate, healthcare, education, and manufacturing sectors, most of whom are from the United States.
Cybersecurity researchers tracked Eldorado's activity and saw that its operators were recruiting knowledgeable affiliates to join the scheme and advertising the malicious service on dark web forums. While it was unavailable at the time of writing, Eldorado also operates a victim-listing data leak website.
Eldorado is a ransomware that runs on the Go platform and has two unique variations that share a great deal of operational similarities. It can encrypt files on both Linux and Windows systems. The encryptor that the researchers acquired from the developer included a user manual indicating that 32- and 64-bit versions for Windows and VMware ESXi hypervisors are available. Eldorado is a unique development that doesn't rely on previously released builder sources.
For every file that is locked, the malware creates a different 32-byte key and 12-byte nonce using the ChaCha20 encryption algorithm. Next, the Optimal Asymmetric Encryption Padding (OAEP) algorithm is applied to encrypt the keys and nonces using RSA. The ".00000001" extension is added to files after the encryption step, and ransom notes with the name "HOW_RETURN_YOUR_DATA.TXT" are put into the Documents and Desktop folders.
Eldorado also removes shadow volume copies from the affected Windows computers to hinder recovery and encrypts network shares using the SMB communication protocol to maximize its effect. To avoid making the system unusable or unbootable, the ransomware ignores DLLs, LNK, SYS, and EXE files in addition to files and directories about system boot and fundamental operation. Lastly, it is configured to self-delete by default to avoid being discovered and examined by response teams.
Researchers, who broke into the operation, say that affiliates can alter their attacks. On Windows, for example, users can choose which directories to encrypt, ignore local files, target network shares on particular subnets, and stop the malware from erasing itself. However, Linux customization parameters only allow you to encrypt the directories.
Researchers emphasize that the Eldorado ransomware threat is not a rebranding of another group, but rather a brand-new, independent operation. It is recommended to apply protections, such as MFA, EDR, making data backups, and applying security patches, which can partially guard against any ransomware attack. Experts also advise against paying a ransom as it hardly guarantees data recovery and can encourage further attacks.
Ransom Note:

Impact
- Sensitive Data Theft
- File Encryption
- Financial Loss
- Unauthorized Access
Indicators of Compromise
IP
- 173.44.141.152
MD5
- 315a9d36ed86894269e0126b649fb3d6
SHA-256
- cb0b9e509a0f16eb864277cd76c4dcaa5016a356dd62c04dff8f8d96736174a7
SHA-1
- caaa1f85dd333c9d19767b5de527152d5acbc2a4
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Implement robust multi-layered security measures to detect and respond to ransomware and cyber espionage activities.
- Conduct regular security assessments and penetration testing to identify and mitigate vulnerabilities in critical infrastructure and government systems.
- Deploy advanced threat detection tools, such as Endpoint Detection and Response (EDR) and Network Traffic Analysis (NTA), to monitor for suspicious activities and anomalies.
- Ensure timely patching and updating of all software and systems to close known security gaps.
- Use multi-factor authentication (MFA) and strong password policies to protect user accounts from unauthorized access.
- Segment networks to limit lateral movement within the organization in case of a breach.
- Develop and maintain an incident response plan that includes procedures for ransomware attacks and data breaches.
- Train employees on cybersecurity best practices and phishing awareness to reduce the risk of social engineering attacks.
- Regularly back up critical data and ensure backups are stored securely and are not accessible from the primary network.
- Collaborate with cybersecurity firms and government agencies for threat intelligence sharing and coordinated defense strategies.
- Implement encryption for sensitive data at rest and in transit to protect against data theft.
- Limit access to critical systems and data to only those individuals who require it for their role.
- Monitor for and immediately investigate the presence of known malware and indicators of compromise associated with state-sponsored groups.
- Engage in regular cybersecurity drills and exercises to ensure readiness for potential cyber incidents.
- Ensure legal and compliance measures are in place, particularly for industries subject to specific regulatory requirements.

