Severity
High
Analysis Summary
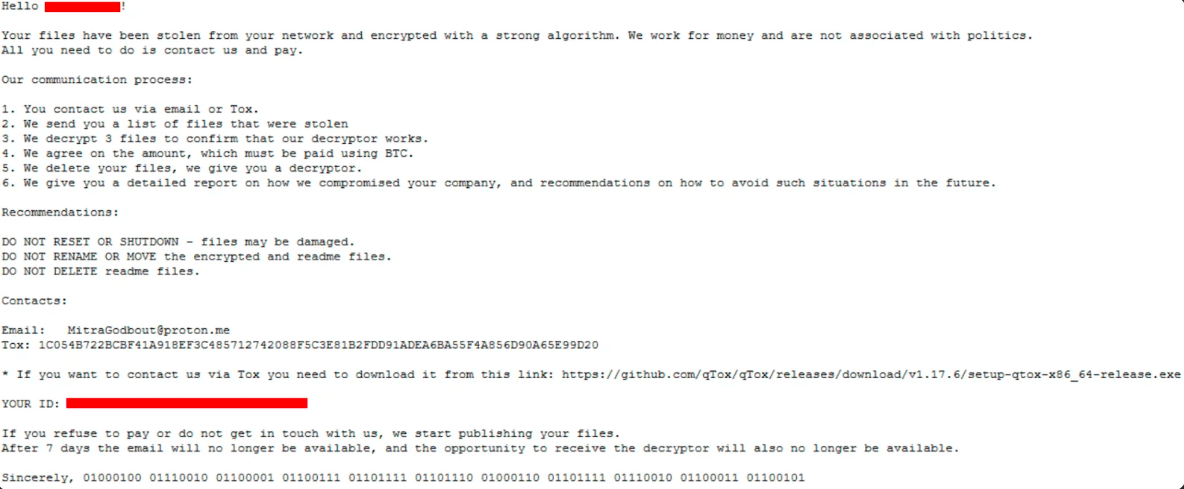
DragonForce Ransomware is a relatively new but highly disruptive ransomware strain that emerged in mid-2023 and gained prominence throughout 2024. Believed to have originated from a cybercriminal collective operating out of Eastern Europe or Southeast Asia, DragonForce is known for its aggressive double-extortion tactics—encrypting victim data and threatening to leak sensitive information unless a ransom is paid.
While not officially attributed to a well-known Advanced Persistent Threat (APT) group, threat researchers have observed TTPs (tactics, techniques, and procedures) that resemble those used by APT38 (linked to North Korea) and FIN12, suggesting either collaboration or imitation. Some sources have also referred to the ransomware under aliases such as DFLocker or ForceCrypt, depending on slight code variations and ransom note signatures.
DragonForce has primarily targeted critical infrastructure, healthcare, and logistics sectors, with a clear pattern of targeting high-value organizations across North America, Europe, and parts of Asia. A spike in activity was noted in late 2024, with several hospital systems and freight operators forced into downtime.
In 2025, the group launched a coordinated campaign against multiple cloud service providers and MSPs (Managed Service Providers), exploiting known vulnerabilities in outdated RMM tools. The group also incorporated new evasion techniques, including custom obfuscators and living-off-the-land binaries (LOLBins), making detection significantly harder.
Its recent activity shows a shift toward persistent access and modular payloads, indicating a maturation of its toolset and operational strategy. Security agencies have raised the threat level associated with DragonForce as it continues to evolve.
Impact
- Operational Disruption
- Data Exfiltration
- Financial Loss
- Reputational Damage
Indicators of Compromise
MD5
e84270afa3030b48dc9e0c53a35c65aa
SHA-256
df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403
SHA1
4a34bbad85312ef34b60818a47f7b5bb8e9a7e26
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Disconnect infected devices from the internet and local networks immediately to prevent the ransomware from spreading.
- Do not pay the ransom, paying does not guarantee file recovery and may encourage further attacks.
- Use reputable antivirus or anti-malware software to detect and remove the ransomware from your system.
- Restore files from clean backups if available, ensure backups are not connected to the infected network during restoration.
- Update all software, operating systems, and firmware to their latest versions to patch known vulnerabilities.
- Implement network segmentation to limit the spread of ransomware within your organization.
- Conduct regular security audits and vulnerability assessments to identify and address potential security gaps.
- Implement strict user access controls, granting permissions based on the principle of least privilege.
- Develop and regularly update an incident response plan to effectively respond to ransomware attacks.
- Monitor network traffic for unusual activity that may indicate a ransomware infection.
- Regularly back up critical data and store backups offline or in a secure, isolated environment.

